That_Sound_Guy
2[H]4U
- Joined
- Apr 29, 2002
- Messages
- 3,076
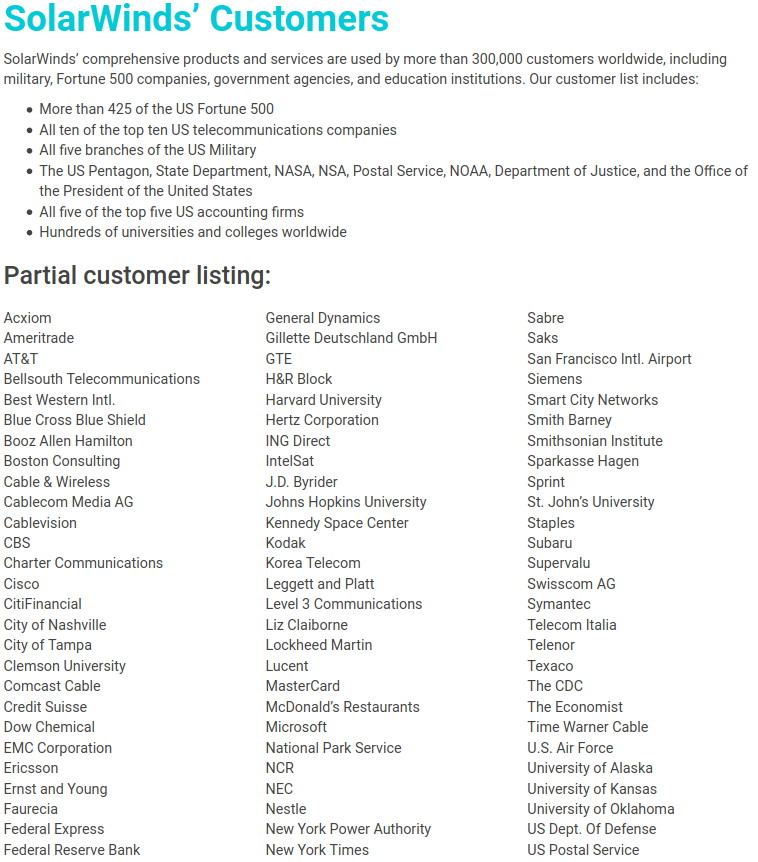
"SolarWinds has just been made aware our systems experienced a highly sophisticated, manual supply chain attack on SolarWinds® Orion® Platform software builds for versions 2019.4 HF 5 through 2020.2.1, released between March 2020 and June 2020. We have been advised this attack was likely conducted by an outside nation state and intended to be a narrow, extremely targeted, and manually executed attack, as opposed to a broad, system-wide attack. We recommend taking the following steps related to your use of the SolarWinds Orion Platform."
https://www.solarwinds.com/securityadvisory
https://www.solarwinds.com/securityadvisory
![[H]ard|Forum](/styles/hardforum/xenforo/logo_dark.png)