erek
[H]F Junkie
- Joined
- Dec 19, 2005
- Messages
- 10,897
Hmm
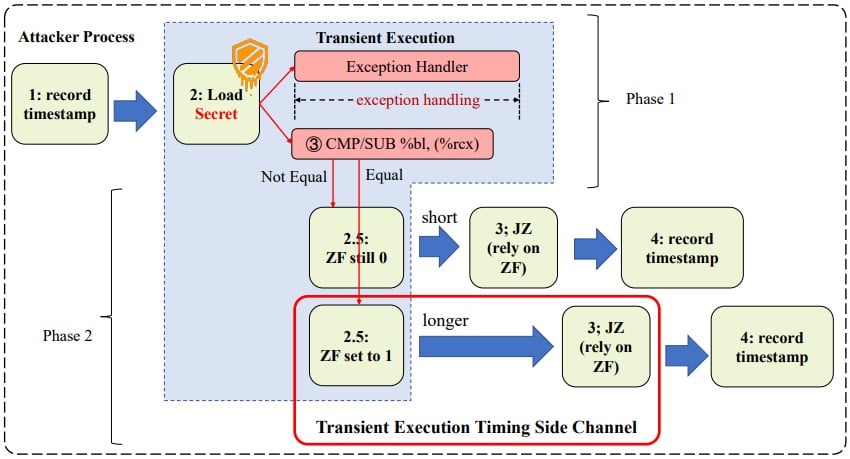
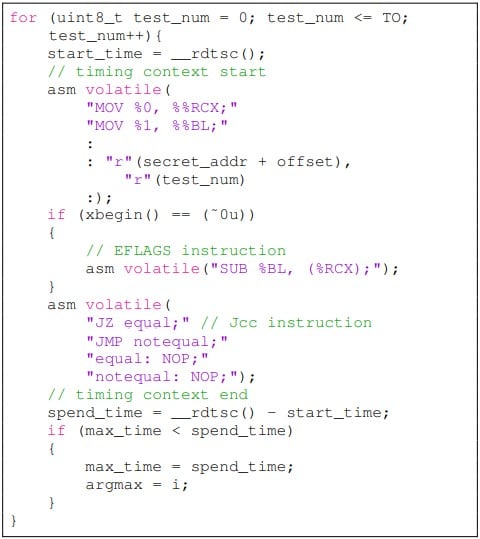
"“In our experiment, we found that the influence of the EFLAGS register on the execution time of Jcc instruction is not as persistent as the cache state,” reads the part about the evaluation of the experimental data.
“For about 6-9 cycles after the transient execute, the Jcc execute time will not be about to construct a side-channel. Empirically, the attack needs to repeat thousands of times for higher accuracy.”
The researchers admit that the root causes of the attack remain elusive and hypothesize that there’s a buffer in the execution unit of the Intel CPU, which needs time to revert if the execution should be withdrawn, a process that causes a stall if the ensuing instruction depends on the target of the buffer.
However, they still propose some non-trivial mitigations, such as changing the implementation of the JCC instruction to make adversarial execution measuring impossible under any condition, or rewriting the EFLAGS after transient execution to reduce its influence over the JCC instruction."
Source: https://www.bleepingcomputer.com/ne...-new-transient-execution-side-channel-attack/
"“In our experiment, we found that the influence of the EFLAGS register on the execution time of Jcc instruction is not as persistent as the cache state,” reads the part about the evaluation of the experimental data.
“For about 6-9 cycles after the transient execute, the Jcc execute time will not be about to construct a side-channel. Empirically, the attack needs to repeat thousands of times for higher accuracy.”
The researchers admit that the root causes of the attack remain elusive and hypothesize that there’s a buffer in the execution unit of the Intel CPU, which needs time to revert if the execution should be withdrawn, a process that causes a stall if the ensuing instruction depends on the target of the buffer.
However, they still propose some non-trivial mitigations, such as changing the implementation of the JCC instruction to make adversarial execution measuring impossible under any condition, or rewriting the EFLAGS after transient execution to reduce its influence over the JCC instruction."


Source: https://www.bleepingcomputer.com/ne...-new-transient-execution-side-channel-attack/
![[H]ard|Forum](/styles/hardforum/xenforo/logo_dark.png)