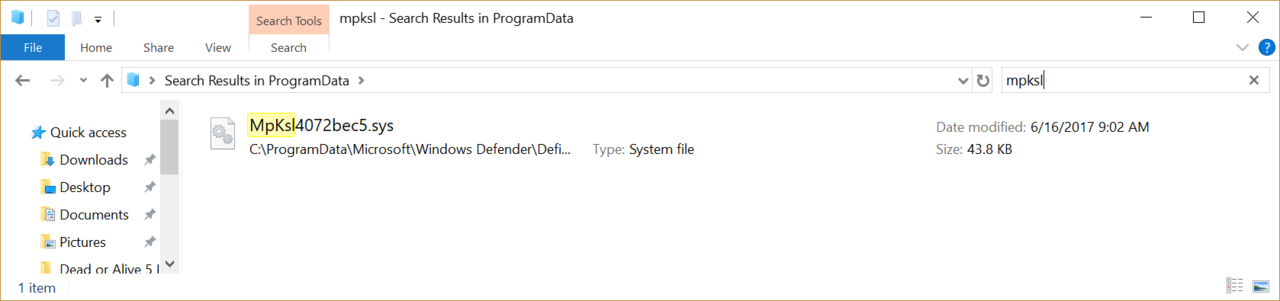
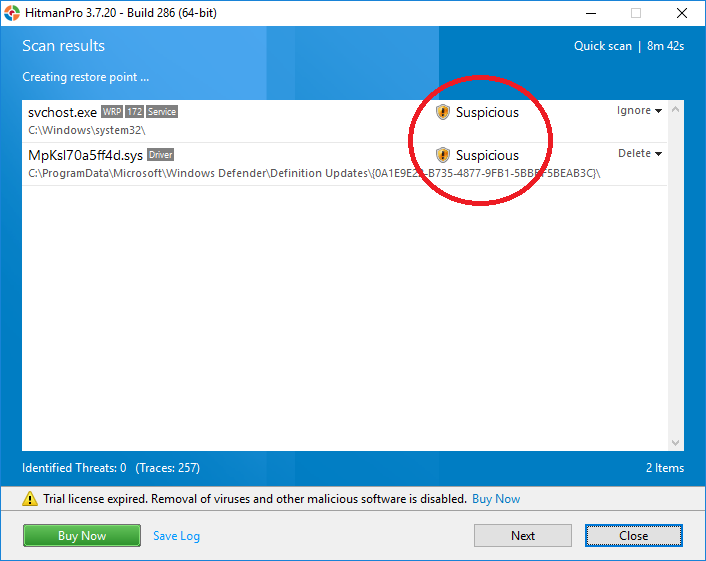
Within the past 24 hours, I've detected and isolated a rootkit on a Windows 10 system attached to MpKsl2ad74297.sys in the Windows Defender Definition Update folder, which cannot be purged due unless the Windows Defender Service is disabled.
Searches are not netting me accurate results - how do I disable the Windows Defender Services via CMD to purge the obstinate file? "net stop windefend" results in a System error 5 - Access is denied.
Thanks!
Searches are not netting me accurate results - how do I disable the Windows Defender Services via CMD to purge the obstinate file? "net stop windefend" results in a System error 5 - Access is denied.
Thanks!
![[H]ard|Forum](/styles/hardforum/xenforo/logo_dark.png)