Navigation
Install the app
How to install the app on iOS
Follow along with the video below to see how to install our site as a web app on your home screen.
Note: This feature may not be available in some browsers.
More options
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Millions of PC Motherboards Were Sold With a Firmware Backdoor
- Thread starter erek
- Start date
Red Falcon
[H]ard DCOTM December 2023
- Joined
- May 7, 2007
- Messages
- 12,455
QFT, and just imagine the backdoors that haven't been found in Gigabyte's enterprise products, let alone everything else.When people think they're buying a product, when in fact the product is them.
Just like the backdoor open ports found in Netgear network equipment (lied about fixing it by de-listing it and just left it open) and HPE servers in the mid-2010s.Yeah, like how the US government had tens of thousands of compromised Cisco network devices just a few years ago. If it exists, theres a back door for somebody.
It was one of the reasons I dumped Netgear completely and have never looked back.

I didn't see it on my x570 aorus elite wifi, although the board isn't listed under that name in the pdf above. I have a z690-i ultra ddr4, (the new version, not the older, lite one) and it's on the list, but it's in the closet, sans cpu, so I can't check it right now.Do those of you with an affected motherboard have the option "APP Center Download & Install"
I've seen Asus motherboards with bios settings for Armoury [sic] Crate, though.
jlbenedict
2[H]4U
- Joined
- May 22, 2005
- Messages
- 2,208
The following is one the recommendations that Eclypsium Labs issued in its blog: Inspect and disable the “APP Center Download & Install” feature in UEFI/BIOS Setup on Gigabyte systems and set a BIOS password to deter malicious changes.
—https://eclypsium.com/blog/supply-chain-risk-from-gigabyte-app-center-backdoor/
Do those of you with an affected motherboard have the option "APP Center Download & Install" (or possibly a similarly named option) in the firmware settings?
I guess I was at least ahead of things as I disabled this option before knowing about this "vulnerability".
WhoBeDaPlaya
2[H]4U
- Joined
- Dec 16, 2002
- Messages
- 2,642
B650M Aorus Elite AX represent!
Whatever, still on BIOS F3c from last Nov with VSOC behaving itself.
Will wait a couple of months / releases before updating (and revalidating the PBO undervolt + underwatt)
Whatever, still on BIOS F3c from last Nov with VSOC behaving itself.
Will wait a couple of months / releases before updating (and revalidating the PBO undervolt + underwatt)
Never fear, I is here...You hacked the Gibson then or what? Hmm

Halon
Gawd
- Joined
- Aug 13, 2004
- Messages
- 856
I was pleasantly surprised to see that the x299 Aorus Gaming 7 I ran for several years was not affected... but the cheap as chips B450M I snagged as part of a Micro Center combo deal late last year was. Jesus, what a mess. I am going to turn into someone who only runs enterprise kit at this rate...Full list of affected boards.
https://eclypsium.com/wp-content/uploads/Gigabyte-Affected-Models.pdf
But it’s basically ever consumer or prosumer board they have produced over the last 5 years…
Last edited:
Say what you will about prebuilts, but Dell still offers bios updates for the Gen 6 Intels as things are found.I was pleasantly surprised to see that the x299 Aorus Gaming 7 I ran for several years was not affected... but the cheap as chips B450M I snagged as part of a Micro Center late last year was. Jesus, what a mess. I am going to turn into someone who only runs enterprise kit at this rate...
SuperMicro is solid though, if you snag one with the IPMI managers it makes any diagnostics easy.
The Mad Atheist
2[H]4U
- Joined
- Mar 9, 2018
- Messages
- 2,193
The masses are just a recourse to milk.When people think they're buying a product, when in fact the product is them.
Halon
Gawd
- Joined
- Aug 13, 2004
- Messages
- 856
I wish AMD would update their Epyc Embedded line - a 16 core chip in a SuperMicro ITX motherboard would be just about perfect for my needs. May I never buy a gaming-targeted motherboard again.Say what you will about prebuilts, but Dell still offers bios updates for the Gen 6 Intels as things are found.
SuperMicro is solid though, if you snag one with the IPMI managers it makes any diagnostics easy.
GoodBoy
2[H]4U
- Joined
- Nov 29, 2004
- Messages
- 2,772
If they had at least securely implemented it, it would have improved the overall security of those systems. Firmware updates often fix security issues, spectre/meltdown, etc. So if it had been better designed, it would have been a good idea. I do think that the user should get a pop-up saying "An update is available" before it is 'just installed'.. but I haven't seen the process in question in action, so could be incorrect in my understanding of how it works.... the idea that something like a firmware update should take place automatically and outside the view of the owner/admin just doensn't make any sense...
I’m still using one of their first gen ones based on the Zen1. She’s old but she does the job.I wish AMD would update their Epyc Embedded line - a 16 core chip in a SuperMicro ITX motherboard would be just about perfect for my needs. May I never buy a gaming-targeted motherboard again.
They way they did it was intercepting the shipments and modifying the units. They didn't have Cisco build hacked units, they hacked them in transit. For a targeted attack it makes much more sense to do it that way, as there are less people that know about it. If they try to get Cisco to make hacked units that means that not only are people at Cisco going to know about it, but Cisco might decide to fight it. While some people, including some in the government, think National Security Letters are magic wands that can force anything, they aren't. A company very well might push back legally against a demand like "put a backdoor in your routers."And they probably did it with a national security letter. Cisco would have to have been aware of that one, but being subject to U.S. law being forced to comply with the national security letter, and also being forced to not disclose it's existence.
As I recall the Cisco products were specifically targeted at certain customers as well. Not just inserted in every unit.
Also the NSA's job is twofold: It is to spy on other countries, but also to keep US data safe, and having Cisco weaken their routers would be contrary to that. Much better to just insert the backdoor themselves in to the units they know are going to people they want to spy on.
As for this stupidity, Gigabyte needs to stop with the dumb shit and get on board with capsule updates. These get distributed through the OS, they come down in Windows update if you use Windows, and are verified and signed. It is not only a good way to maintain security on the updates, but since it comes in the normal update channel, you can manage it with whatever your update management solution is and decide when they get rolled out.
Dell does it, and it is great. Your just get UEFI updates along with other drivers. It even knows how to suspend bitlocker automatically.
Gigabyte doing their own auto updater is extremely stupid because, well, this could happen. While OS updates aren't perfectly secure, they are a hell of a lot more likely to be secure and they are easy to patch if there's an issue.
erek
[H]F Junkie
- Joined
- Dec 19, 2005
- Messages
- 10,906
They way they did it was intercepting the shipments and modifying the units. They didn't have Cisco build hacked units, they hacked them in transit. For a targeted attack it makes much more sense to do it that way, as there are less people that know about it. If they try to get Cisco to make hacked units that means that not only are people at Cisco going to know about it, but Cisco might decide to fight it. While some people, including some in the government, think National Security Letters are magic wands that can force anything, they aren't. A company very well might push back legally against a demand like "put a backdoor in your routers."
Also the NSA's job is twofold: It is to spy on other countries, but also to keep US data safe, and having Cisco weaken their routers would be contrary to that. Much better to just insert the backdoor themselves in to the units they know are going to people they want to spy on.
As for this stupidity, Gigabyte needs to stop with the dumb shit and get on board with capsule updates. These get distributed through the OS, they come down in Windows update if you use Windows, and are verified and signed. It is not only a good way to maintain security on the updates, but since it comes in the normal update channel, you can manage it with whatever your update management solution is and decide when they get rolled out.
Dell does it, and it is great. Your just get UEFI updates along with other drivers. It even knows how to suspend bitlocker automatically.
Gigabyte doing their own auto updater is extremely stupid because, well, this could happen. While OS updates aren't perfectly secure, they are a hell of a lot more likely to be secure and they are easy to patch if there's an issue.
GIGABYTE Fortifies System Security with Latest BIOS Updates and Enhanced Verification
PRESS RELEASE by GFreeman Today, 11:59 Discuss (2 Comments)GIGABYTE Technology, one of the leading global manufacturers of motherboards, graphics cards, and hardware solutions, has always prioritized cybersecurity and information security. GIGABYTE remains committed to fostering close collaboration with relevant units and implementing robust security measures to safeguard its users. GIGABYTE engineers have already mitigated potential risks and uploaded the Intel 700/600 and AMD 500/400 series Beta BIOS to the official website after conducting thorough testing and validation of the new BIOS on GIGABYTE motherboards.
To fortify system security, GIGABYTE has implemented stricter security checks during the operating system boot process. These measures are designed to detect and prevent any possible malicious activities, providing users with enhanced protection:
- 1. Signature Verification: GIGABYTE has bolstered the validation process for files downloaded from remote servers. This enhanced verification ensures the integrity and legitimacy of the contents, thwarting any attempts by attackers to insert malicious code.
- 2. Privilege Access Limitations: GIGABYTE has enabled standard cryptographic verification of remote server certificates. This guarantees that files are exclusively downloaded from servers with valid and trusted certificates, ensuring an added layer of protection.
EmerilLIVE
Weaksauce
- Joined
- Jan 31, 2008
- Messages
- 111
I have one of the effected B550 motherboards. There is no BIOS update on the support page.
Meh, I'll get around to updating my boards. This seems more like a man in the middle attack anyway.
I'm the meantime disable the app center download in the bios, as most people should have anyway since it's annoying.
https://www.tomshardware.com/news/gigabyte-firmware-update-backdoor
I'm the meantime disable the app center download in the bios, as most people should have anyway since it's annoying.
https://www.tomshardware.com/news/gigabyte-firmware-update-backdoor
The b550i aorus pro ax (rev 1.2) doesn't have the option in the bios. Since it's also not stated in the manual and I haven't seen any nags, I am assuming it is not affected by this vulnerability.The following is one the recommendations that Eclypsium Labs issued in its blog: Inspect and disable the “APP Center Download & Install” feature in UEFI/BIOS Setup on Gigabyte systems and set a BIOS password to deter malicious changes.
—https://eclypsium.com/blog/supply-chain-risk-from-gigabyte-app-center-backdoor/
Do those of you with an affected motherboard have the option "APP Center Download & Install" (or possibly a similarly named option) in the firmware settings?
Delicieuxz
[H]ard|Gawd
- Joined
- May 11, 2016
- Messages
- 1,668
My guess is that almost everything from a major US company is backdoored or otherwise infiltrated by the state, and has been for a very long time.
NSA Built Back Door In All Windows Software by 1999
U.S. Agencies Said to Swap Intelligence With Thousands of Firms
WikiLeaks #Vault7: 85% of world’s smart phones ‘weaponized’ by CIA
Advanced CIA firmware has been infecting Wi-Fi routers for years
Photos of an NSA “upgrade” factory show Cisco router getting implant
Google’s true origin partly lies in CIA and NSA research grants for mass surveillance
The NSA’s Hidden Spy Hubs in Eight U.S. Cities
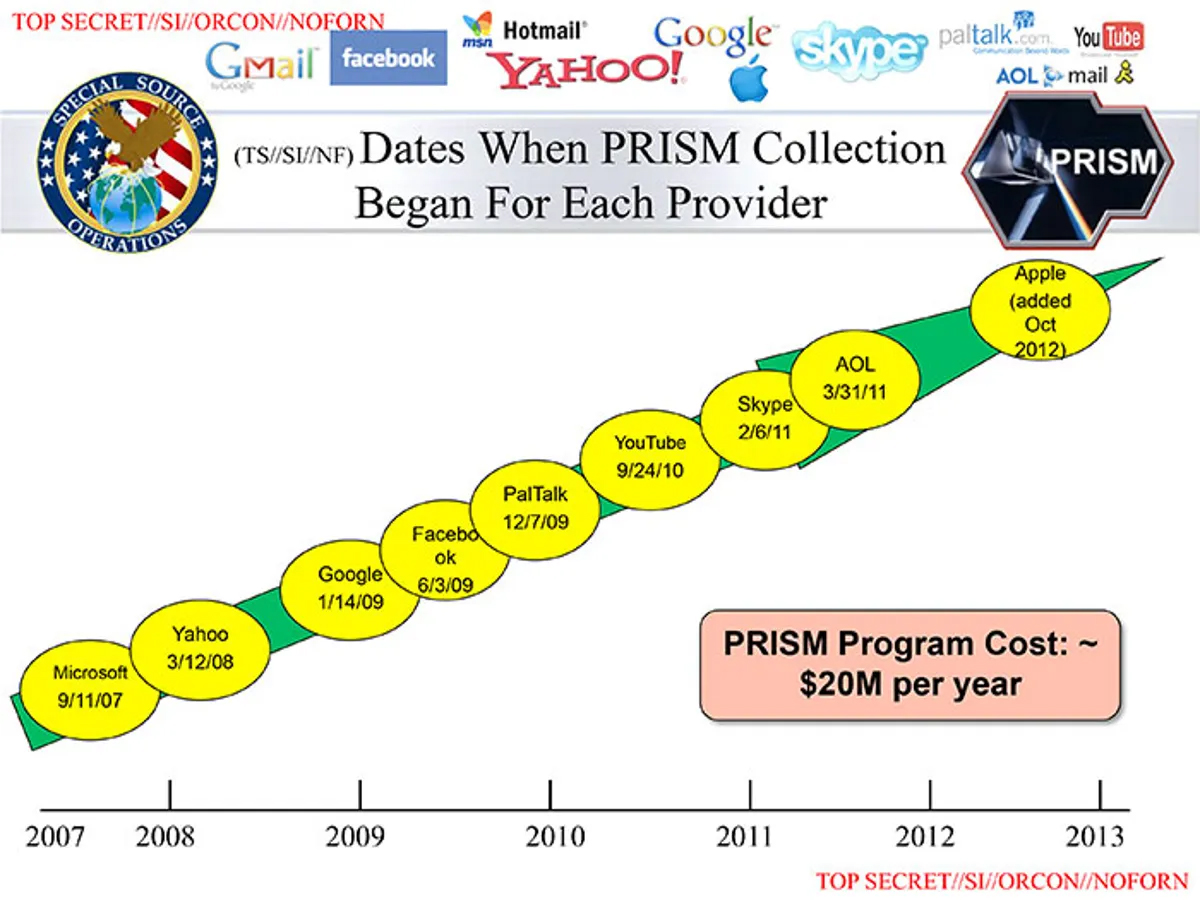
NSA Built Back Door In All Windows Software by 1999
U.S. Agencies Said to Swap Intelligence With Thousands of Firms
WikiLeaks #Vault7: 85% of world’s smart phones ‘weaponized’ by CIA
Advanced CIA firmware has been infecting Wi-Fi routers for years
Photos of an NSA “upgrade” factory show Cisco router getting implant
Google’s true origin partly lies in CIA and NSA research grants for mass surveillance
The NSA’s Hidden Spy Hubs in Eight U.S. Cities


Last edited:
erek
[H]F Junkie
- Joined
- Dec 19, 2005
- Messages
- 10,906
My guess is that almost everything from a major US company is backdoored or otherwise infiltrated by the state, and has been for a very long time.
NSA Built Back Door In All Windows Software by 1999
U.S. Agencies Said to Swap Intelligence With Thousands of Firms
WikiLeaks #Vault7: 85% of world’s smart phones ‘weaponized’ by CIA
Advanced CIA firmware has been infecting Wi-Fi routers for years
Photos of an NSA “upgrade” factory show Cisco router getting implant
The NSA’s Hidden Spy Hubs in Eight U.S. Cities
View attachment 574086
View attachment 574075
PRISM’s Controversial Forerunner: PROMIS
Using a powerful computer program known as PRISM, the U.S. government has been downloading vast amounts of communications data and mining it for counterterrorism purposes. But these capabilities began more than three decades ago with the controversial PROMIS software, Richard L. Fricker reports."Prosecutors Management Information Systems (PROMIS) software. PROMIS was developed by Inslaw Inc., a company founded by Bill and Nancy Hamilton, and was designed to modernize the case management systems within the Department of Justice (DOJ) in the late 1970s and early 1980s. However, the software's capabilities expanded beyond its initial purpose, raising numerous ethical and legal issues.
PROMIS was originally designed to track and manage criminal cases, but subsequent adaptations made it suitable for broader data integration, allowing it to track anything kept in a database, such as birth and death certificates, licenses, mortgages, and lawsuits, as well as more confidential matters like banking transactions, communications, and arms shipments.
Controversy arose when it was alleged that the DOJ terminated payments to Inslaw and retained the software, leading to Inslaw's bankruptcy in 1986. The company claimed that the DOJ had stolen their software and made efforts to push them out of business. This claim was supported by a bankruptcy judge in 1987, although later overruled by the DC District Court of Appeals.
There were also rumors that the DOJ provided the software to intelligence agencies, including the National Security Agency (NSA) and the Central Intelligence Agency (CIA). Moreover, it was reported that friends of the Reagan administration were selling unauthorized versions of PROMIS.
In 1989, the chairman of the House Judiciary Committee launched an investigation into these allegations, concluding that Inslaw's software was indeed stolen and distributed internationally for financial gain and intelligence objectives. However, the recommended settlement for Inslaw and the appointment of a special prosecutor never occurred.
To this day, Inslaw has not received any settlements, although PROMIS is legally used in multiple countries. Despite the controversy, the capabilities and ethical implications of PROMIS remain largely unexplored. Its significant data gathering and tracking abilities over the last three decades make it a major, yet under-discussed, presence in the world of digital surveillance."
"The controversy centered around INSLAW's case management software called PROMIS, which was installed in U.S. Attorney offices nationwide after a $10 million contract was awarded to INSLAW by the Justice Department in 1982. Disputes arose, leading INSLAW to allege that the Department of Justice conspired to steal its software and deny it proper compensation. These claims sparked multiple lawsuits, congressional investigations, and internal Justice Department reviews.
The report being released affirms previous findings that there is no credible evidence to support INSLAW's allegations. It states that Justice Department employees did not conspire to steal the PROMIS software or harm INSLAW. It also determined that the software's use conformed with the contract agreements, and therefore, INSLAW was not entitled to additional compensation.
INSLAW's claims that Justice Department officials conspired to destroy the company and covertly profit from its work were mostly based on anonymous sources, none of which came forward despite assurances of protection from Attorney General Janet Reno. The report considered the primary sources relied upon by INSLAW to be non-credible.
Further investigations were conducted into recent claims by INSLAW, such as the accusation that the FBI's FOIMS software is a pirated version of PROMIS. Dr. Randall Davis, an MIT professor, was hired to compare the software codes and found no relation between FOIMS and PROMIS.
The report also dismissed allegations that PROMIS software had been stolen to raise money for other covert operations or that it was being improperly used or distributed within the government or to foreign entities.
Lastly, the report addressed the death of J. Daniel Casolaro, a freelance journalist investigating the INSLAW case, who INSLAW claimed was murdered in connection with the case. It supported previous police findings that Casolaro's death was a suicide, backed by extensive forensic evidence and accounts of his depression and professional struggles.
In conclusion, the report found no credible evidence supporting INSLAW's claims and recommended that the matter be closed. It also advised against granting additional compensation to INSLAW, asserting that the company had had ample opportunity to litigate its claims and that its ongoing allegations should not be rewarded."
Prince Valiant
Limp Gawd
- Joined
- May 3, 2023
- Messages
- 345
A friend has the same X570 board and they couldn't find the setting either. It's mentioned once early in the manual and then there's nothing in the BIOS section.I didn't see it on my x570 aorus elite wifi, although the board isn't listed under that name in the pdf above. I have a z690-i ultra ddr4, (the new version, not the older, lite one) and it's on the list, but it's in the closet, sans cpu, so I can't check it right now.
I've seen Asus motherboards with bios settings for Armoury [sic] Crate, though.
Meh, I'll get around to updating my boards. This seems more like a man in the middle attack anyway.
I'm the meantime disable the app center download in the bios, as most people should have anyway since it's annoying.
https://www.tomshardware.com/news/gigabyte-firmware-update-backdoor
I explained that on page 1 but people like outrage more better. lol
EmerilLIVE
Weaksauce
- Joined
- Jan 31, 2008
- Messages
- 111
That's the board I have, not sure which revision. All the revisions are listed in the PDF as affected.The b550i aorus pro ax (rev 1.2) doesn't have the option in the bios. Since it's also not stated in the manual and I haven't seen any nags, I am assuming it is not affected by this vulnerability.
Does your board have the download app option in the bios and/or do you get a nag screen on windows boot to download live update? If the board doesn't have the feature which contains the vulnerability, it is extremely unlikely that is has this particular vulnerability.That's the board I have, not sure which revision. All the revisions are listed in the PDF as affected.
Given the quality and hysterical tone of the eclypsium article, I wouldn't be surprised if that pdf list was (semi) automatically generated (based on chipset/branding) without actually verifying for each board whether it had the vulnerability.
You can find the hardware revision printed on the board itself, in one of the corners near the internal hd-audio connector, if I remember correctly.
Last edited:
Pretty much. I feel much safer giving China my data than the US.Western designed or Eastern designed, the only difference it makes is who is getting your data and who has access to the back doors.
China may use it to gain an edge over US companies.
The US may use it (during some seemingly, rapidly approaching, dystopian future) to persecute me for thought crimes.
Format _C:
2[H]4U
- Joined
- Jun 12, 2001
- Messages
- 3,885
Glad my X570 AORUS Elite is not on that list!Full list of affected boards.
https://eclypsium.com/wp-content/uploads/Gigabyte-Affected-Models.pdf
But it’s basically ever consumer or prosumer board they have produced over the last 5 years…
I am UNHAPPY that my Z690 Aorus Elite AX (DDR5) seems to have this ****....
In fairness I should have probably noticed this earlier and disabled it, However I uninstalled the app center then disabled this in the bios...
My wife's B550 Aorus Elite doesn't seem to be affected....
Next time I goto build, I may look elsewhere from gigabyte for the 1st time basically since 2010, I am very annoyed by this issue.
In fairness I should have probably noticed this earlier and disabled it, However I uninstalled the app center then disabled this in the bios...
My wife's B550 Aorus Elite doesn't seem to be affected....
Next time I goto build, I may look elsewhere from gigabyte for the 1st time basically since 2010, I am very annoyed by this issue.
I have a B550i Aorus Pro AX Rev. 1.2 and noticed today that there's a Bios update addressing the issue. Also this mentioned above is not true (The b550i aorus pro ax (rev 1.2) doesn't have the option in the bios) in Settings, I/O Ports the App Center Download Assistant is what should be disabled.
Last edited:
EmerilLIVE
Weaksauce
- Joined
- Jan 31, 2008
- Messages
- 111
It looks like there are now updated BIOS's posted for all revisions of the board dated June 1st. They weren't there at the time of my prior post on June 2nd, at which time the press release from Gigabyte said they had posted updates for all the B550 motherboards.I have a B550i Aorus Pro AX Rev. 1.2 and noticed today that there's a Bios update addressing the issue. Also this mentioned above is not true (The b550i aorus pro ax (rev 1.2) doesn't have the option in the bios) in Settings, I/O Ports the App Center Download Assistant is what should be disabled.
![[H]ard|Forum](/styles/hardforum/xenforo/logo_dark.png)