So I was benching my new 2070 with Timespy on the 17th. I've had windows update since then and I'm just now getting around to attempting more over the scanner overclock.
Might I say they did a good job with that because if I bump the core up to the next notch it crashes Timespy. lol
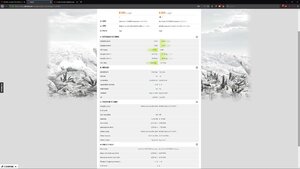
Anyway I had some windows updates this morning and I'm wondering if they put patches in for this new Zombieload or what ever it is that may be affecting my scores on my 6700K?
When I was benching on the 17th the cpu scores were pretty level +- a few points but to drop around 300 points seems a bit odd to me. Not running the cpu overclock so nothing has been changed with it just the windows update that ran this morning is the only change.
Might I say they did a good job with that because if I bump the core up to the next notch it crashes Timespy. lol
Anyway I had some windows updates this morning and I'm wondering if they put patches in for this new Zombieload or what ever it is that may be affecting my scores on my 6700K?
When I was benching on the 17th the cpu scores were pretty level +- a few points but to drop around 300 points seems a bit odd to me. Not running the cpu overclock so nothing has been changed with it just the windows update that ran this morning is the only change.
![[H]ard|Forum](/styles/hardforum/xenforo/logo_dark.png)