peppergomez
2[H]4U
- Joined
- Sep 15, 2011
- Messages
- 2,179
Ugh, this thing is VICIOUS.
I just got this virus, which is a doozy. It locks users out of Windows completely.
http://malwaretips.com/blogs/fbi-cybercrime-division-icspa-virus/
("If your computer is locked, and you are seeing a “ATTENTION! Your computer has been locked and all data is encrypted!” notification from FBI CyberCrime Division (ICSPA) , then your computer is infected with a piece of malware known as Trojan Reveton.")
I am trying to solve it based on the instructions in that link above, but no luck so far. Hitman Pro didn't detect it, and I can only boot into Safe Mode with Command Prompt (while staying in the command prompt window). All other safe modes reboot immediately back into "regular" Windows, so I'm unable to navigate to Device Manager in Windows or to run any kind of Malware Removal software. I downloaded and isntalled HitmanPro using a clean secondary computer (obviously).
I am trying to fix this without having to revert to a restore point.
Other details:
I can boot into Safe Mode with Command Prompt, and got here (see screenshot)after typing start mmc.exe.
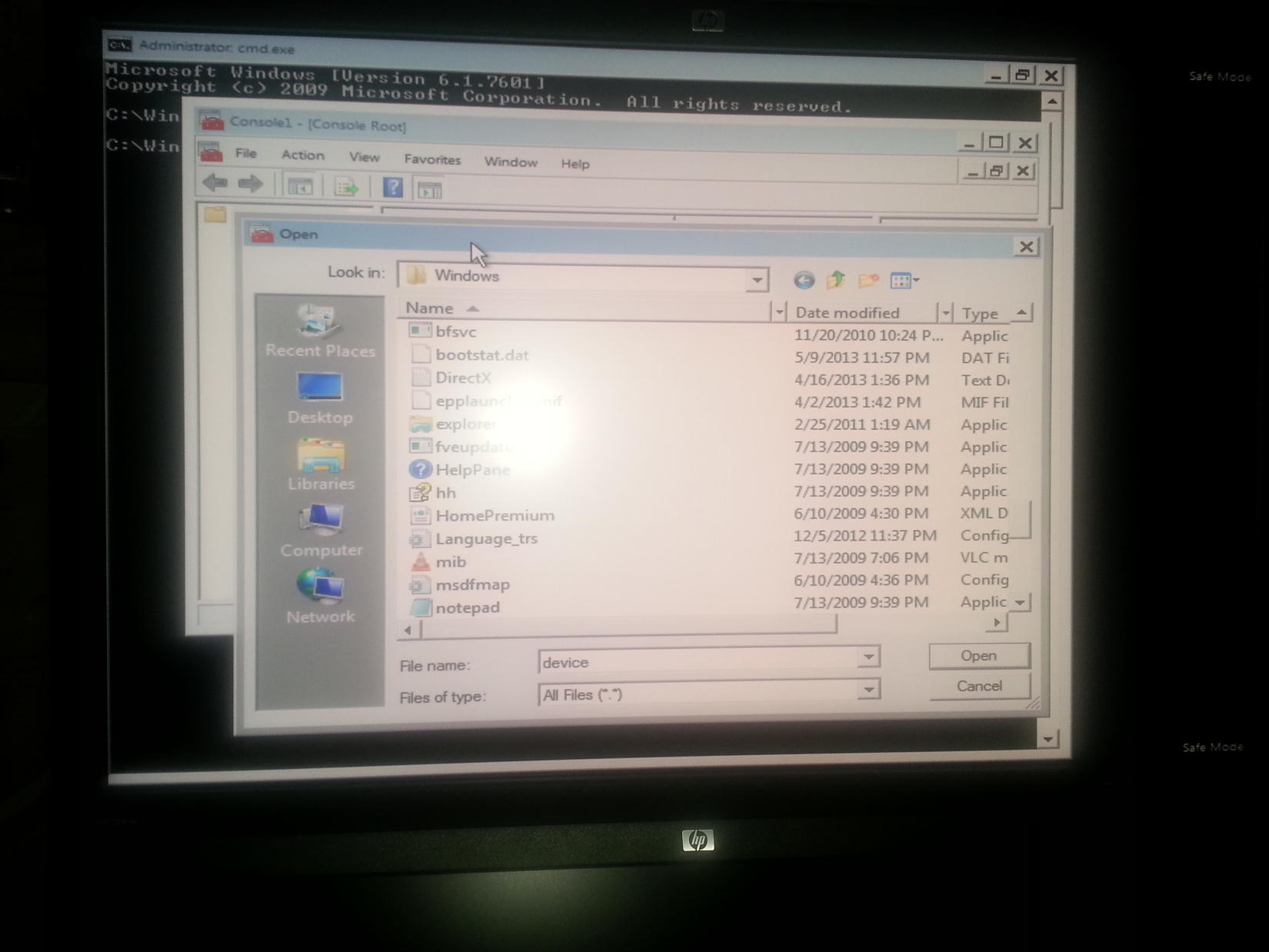
I am trying to get to my drivers in Device Manager, or wherever it is I need to be to look for any suspicious tunnel adapters, viruses, etc etc.
I ran Hitman Pro from a USB boot drive but it failed to find anything after scanning. I also looked in the Startup and Services tabs in msconfig and didn't see anything suspicious. I unchecked a few unfamiliar things for good measure and then rebooted, but it didn't work
Basically, I need to get into Windows so I can run Malwarebytes Anti-Malware to remove this freaking ICSPA virus. But the virus is totally blocking me from using Windows.
Thanks a lot for any help...it sucks not being able to use my computer.
PS- Can anyone recommend another good program that I can save to a USB thumb drive that will allow me to boot and bypass Windows, and then run a Malware scan? Hitman Pro didn't detect any viruses or malware, which is a fail.
I just got this virus, which is a doozy. It locks users out of Windows completely.
http://malwaretips.com/blogs/fbi-cybercrime-division-icspa-virus/
("If your computer is locked, and you are seeing a “ATTENTION! Your computer has been locked and all data is encrypted!” notification from FBI CyberCrime Division (ICSPA) , then your computer is infected with a piece of malware known as Trojan Reveton.")
I am trying to solve it based on the instructions in that link above, but no luck so far. Hitman Pro didn't detect it, and I can only boot into Safe Mode with Command Prompt (while staying in the command prompt window). All other safe modes reboot immediately back into "regular" Windows, so I'm unable to navigate to Device Manager in Windows or to run any kind of Malware Removal software. I downloaded and isntalled HitmanPro using a clean secondary computer (obviously).
I am trying to fix this without having to revert to a restore point.
Other details:
I can boot into Safe Mode with Command Prompt, and got here (see screenshot)after typing start mmc.exe.

I am trying to get to my drivers in Device Manager, or wherever it is I need to be to look for any suspicious tunnel adapters, viruses, etc etc.
I ran Hitman Pro from a USB boot drive but it failed to find anything after scanning. I also looked in the Startup and Services tabs in msconfig and didn't see anything suspicious. I unchecked a few unfamiliar things for good measure and then rebooted, but it didn't work
Basically, I need to get into Windows so I can run Malwarebytes Anti-Malware to remove this freaking ICSPA virus. But the virus is totally blocking me from using Windows.
Thanks a lot for any help...it sucks not being able to use my computer.
PS- Can anyone recommend another good program that I can save to a USB thumb drive that will allow me to boot and bypass Windows, and then run a Malware scan? Hitman Pro didn't detect any viruses or malware, which is a fail.
![[H]ard|Forum](/styles/hardforum/xenforo/logo_dark.png)