Horizon_Galaxy
Weaksauce
- Joined
- Feb 21, 2014
- Messages
- 116
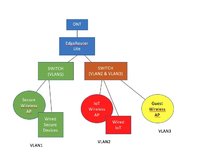
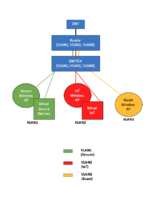
This spring I finally upgraded my home router from the ISP router to a higher end consumer router. I have fiber and I was able to get the router to connect directly to the ONT. I was happy because I finally had a network with a separate guest SSID! Fancy!
Now I'm realizing I should also segregate my IoT devices (over a dozen of them) to their own group, since having them on the main network appears to be a security risk. Most commonly I see this done using VLAN groups.
My consumer router can't do VLAN tagging on the LAN ports. I could shuffle all my IoT devices onto the guest network, but then I either have to put guests on my IoT network or my secure home network.
I was thinking I could get a router that can tag VLAN groups on the LAN ports. Could I continue to use my current router in AP mode to act as an access point for one of the VLAN tagged LAN ports. I'd also need to get APs for my guest and IoT network...
Am I missing another way to secure my IoT devices?
Now I'm realizing I should also segregate my IoT devices (over a dozen of them) to their own group, since having them on the main network appears to be a security risk. Most commonly I see this done using VLAN groups.
My consumer router can't do VLAN tagging on the LAN ports. I could shuffle all my IoT devices onto the guest network, but then I either have to put guests on my IoT network or my secure home network.
I was thinking I could get a router that can tag VLAN groups on the LAN ports. Could I continue to use my current router in AP mode to act as an access point for one of the VLAN tagged LAN ports. I'd also need to get APs for my guest and IoT network...
Am I missing another way to secure my IoT devices?
![[H]ard|Forum](/styles/hardforum/xenforo/logo_dark.png)