Just got Win Server 2008 running on my ESXi server, with the intentions of running it as a 24x7 DC for my home network.
I followed this guide to setting up my domain:
https://support.cloudshare.com/hc/e...a-Domain-Controller-on-Windows-Server-2008-R2
I installed the role as Active Directory Domain Services. I unchecked the option to install the DNS server with it, because I want to use my ISP's DNS servers. my FQDN is home.smithnet.com
However when I tried to connect my first host to the domain, I get this error:
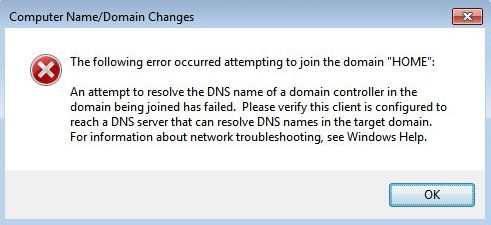
At first i figured this was because I didnt install the DNS role. So i went back and installed the DNS role to my server then added DNS fowarder to point to my ISP's DNS servers.
I tried connecting my host to the domain again but I still get the same error.
any ideas?
I followed this guide to setting up my domain:
https://support.cloudshare.com/hc/e...a-Domain-Controller-on-Windows-Server-2008-R2
I installed the role as Active Directory Domain Services. I unchecked the option to install the DNS server with it, because I want to use my ISP's DNS servers. my FQDN is home.smithnet.com
However when I tried to connect my first host to the domain, I get this error:

At first i figured this was because I didnt install the DNS role. So i went back and installed the DNS role to my server then added DNS fowarder to point to my ISP's DNS servers.
I tried connecting my host to the domain again but I still get the same error.
any ideas?
![[H]ard|Forum](/styles/hardforum/xenforo/logo_dark.png)