Navigation
Install the app
How to install the app on iOS
Follow along with the video below to see how to install our site as a web app on your home screen.
Note: This feature may not be available in some browsers.
More options
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Windows Update best practices?
- Thread starter KapsZ28
- Start date
Come up with some sort of "SOP" document for patching. Dates, responsibilities, actions, etc.
i.e. Windows Update SOP: The IT Manager is responsible for patching all servers .... blah blah ..... every month. The process includes .... blah blah .... . The IT Manager will perform the following actions to verify that the patch level is met ... blah blah ...
Then actually use it, and have some sort of log that documents that you are following this SOP.
This will become your own Best Practice.
This is how we do it at my company - I don't think we would be officially accredited if we didn't have all these SOP documents.
Best practices for Windows patching in general... monthly would be a great goal, quarterly is probably doable depending on your infrastructure. At least weekly for client machines.

i.e. Windows Update SOP: The IT Manager is responsible for patching all servers .... blah blah ..... every month. The process includes .... blah blah .... . The IT Manager will perform the following actions to verify that the patch level is met ... blah blah ...
Then actually use it, and have some sort of log that documents that you are following this SOP.
This will become your own Best Practice.
This is how we do it at my company - I don't think we would be officially accredited if we didn't have all these SOP documents.
Best practices for Windows patching in general... monthly would be a great goal, quarterly is probably doable depending on your infrastructure. At least weekly for client machines.

Mister Natural
2[H]4U
- Joined
- Oct 10, 2002
- Messages
- 3,441
Just tell them what you do now. Auditors make recommendations as to what should be changed if they feel it is out of place. They won't arrest you or nothin'. 
Every year I tell the auditors I don't set password complexity requirements nor set any password expiration. I tell them I don't have time to reset passwords all the time when someone forgets their password which is what I would be doing if I followed the standard. Their response to that is the company should hire more I.T. staff. Good luck with that.
Every year I tell the auditors I don't set password complexity requirements nor set any password expiration. I tell them I don't have time to reset passwords all the time when someone forgets their password which is what I would be doing if I followed the standard. Their response to that is the company should hire more I.T. staff. Good luck with that.
Last edited:
I put this together and my manager still wants me to add the purpose of Microsoft Updates or something like that.
SOP Microsoft Patches
Patch Tuesday is the second Tuesday of each month, on which Microsoft regularly releases security patches.
System Administrators are responsible for patching all Microsoft product within one month of the patch being released.
Patches should be tested and deployed based on the schedule below.
System Administrators are responsible for patching all Microsoft product within one month of the patch being released.
Patches should be tested and deployed based on the schedule below.
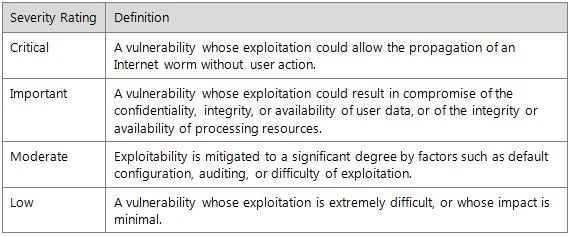
Critical Patch testing should begin immediately after released and deployed company-wide starting on Friday night and finished no later than Sunday morning.
Important Patch testing should begin no later than Friday after the patch has been released and deployed company-wide on the following Wednesday after 10:00 PM EST.
Moderate Patch testing should begin within two business weeks after the patch has been released and deployed company-wide on the following Wednesday after 10:00 PM EST.
Low Patch testing should begin within three business weeks after the patch has been released and deployed company-wide on the following Wednesday after 10:00 PM EST.
Important Patch testing should begin no later than Friday after the patch has been released and deployed company-wide on the following Wednesday after 10:00 PM EST.
Moderate Patch testing should begin within two business weeks after the patch has been released and deployed company-wide on the following Wednesday after 10:00 PM EST.
Low Patch testing should begin within three business weeks after the patch has been released and deployed company-wide on the following Wednesday after 10:00 PM EST.
Any patches found with compatibility issues will need to be reviewed by the Information Security Department, (ISD) before they can be exempt from being deployed.
If ISD finds that the risk is too high to exempt the patch, the Engineering department will need to resolve the compatibility issue within one month of the initial findings.
A workaround may be implemented as long as it does not impact security compliance.
If ISD finds that the risk is too high to exempt the patch, the Engineering department will need to resolve the compatibility issue within one month of the initial findings.
A workaround may be implemented as long as it does not impact security compliance.
I'd give yourself a little more time. Especially for production servers, I don't like to patch them for at least a couple of weeks because the updates could potentially screw something up and I want to ensure that I have time to do the updates, test, and make sure I have time to restore if necessary.


I'd give yourself a little more time. Especially for production servers, I don't like to patch them for at least a couple of weeks because the updates could potentially screw something up and I want to ensure that I have time to do the updates, test, and make sure I have time to restore if necessary.
http://www.hardfolding.com/fh_stats/?pz=102&tnum=33&id=756525
Eh, it's not even real. I've been working here for four months and have never seen a single Windows server patched. These guys don't ever even log out of the servers. Drives me nuts.
Mister Natural
2[H]4U
- Joined
- Oct 10, 2002
- Messages
- 3,441
I normally push the updates to clients the day after patch Tuesday. It's never caused me a problem though I know some will differ. In over 15 years I can only recall one patch in which I actually had to uninstall due to the problems it created. Though some patches can be buggy.
Servers I wait a few days and will usually update them within a week unless it's a patch for Internet Explorer. No web surfing on a server so not an urgent issue.
Servers I wait a few days and will usually update them within a week unless it's a patch for Internet Explorer. No web surfing on a server so not an urgent issue.
I normally push the updates to clients the day after patch Tuesday. It's never caused me a problem though I know some will differ. In over 15 years I can only recall one patch in which I actually had to uninstall due to the problems it created. Though some patches can be buggy.
Servers I wait a few days and will usually update them within a week unless it's a patch for Internet Explorer. No web surfing on a server so not an urgent issue.
Really, only one patch caused issues? I've seen several Microsoft updates over the years that caused issues with Microsoft products such as PowerPoint, Excel, etc. It seems like Microsoft doesn't even fully test patch compatibility before they are released.
Mister Natural
2[H]4U
- Joined
- Oct 10, 2002
- Messages
- 3,441
I didn't say only one patch caused problems. Only one that I can recall (perhaps 2 or 3) caused enough problems to warrant having to remove it.
S
shade91
Guest
Do you not have a pre-production or test environment? We always send the patches immediately to a test group of pre-prod servers and workstations and check its' impact. No issues? Deploy to production. If you are deploying patches immediately to production you're playing with fire (unfortunately, many people are playing with fire as I can tell this is their SOP).
There's nothing wrong with having a process not up to snuff of an audit. At least having a written SOP is a good start and will please your internal and external auditors. You should have your own internal auditing consultant who audits you against what SSAE16 audits for. This consultant will work as your advocate who will in turn work together with you and the external auditor to perform an audit and compare notes with the internal auditor. The external auditor will then give you a list of material weaknesses which need addressing with-in a certain time frame. You have time to address them at which time they get addressed, you're golden.
Source: Been there, done that hundreds of times on SoX audits. These audits are NOT very thorough and can be easily faked.
There's nothing wrong with having a process not up to snuff of an audit. At least having a written SOP is a good start and will please your internal and external auditors. You should have your own internal auditing consultant who audits you against what SSAE16 audits for. This consultant will work as your advocate who will in turn work together with you and the external auditor to perform an audit and compare notes with the internal auditor. The external auditor will then give you a list of material weaknesses which need addressing with-in a certain time frame. You have time to address them at which time they get addressed, you're golden.
Source: Been there, done that hundreds of times on SoX audits. These audits are NOT very thorough and can be easily faked.
![[H]ard|Forum](/styles/hardforum/xenforo/logo_dark.png)