HardOCP News
[H] News
- Joined
- Dec 31, 1969
- Messages
- 0
Watch what happens to this guy when he dares expert hackers to hack him. Yes, it goes just about as bad as you would expect it to.
Follow along with the video below to see how to install our site as a web app on your home screen.
Note: This feature may not be available in some browsers.
#2 started with the user installing a certificate. That's the same damn thing both Dell and Lenovo have been caught installing on their brand new laptops.#2 Guy's laptop is compromised by clicking a fishing email that installs (presumably) remote access software.
Neither one was really hacking.
#2 started with the user installing a certificate. That's the same damn thing both Dell and Lenovo have been caught installing on their brand new laptops.
TLDR Version of the video.
#1 Woman gains control of a cellphone account through phone support. Basic social engineering.
#2 Guy's laptop is compromised by clicking a fishing email that installs (presumably) remote access software.
Neither one was really hacking.
Anyone that knows better wipes the drive and reinstalls the OS from a know clean ISO.
What?!? And miss out on my free copy of McAfee AntiVirus!? Are you insane?
/s
Anyone that knows better wipes the drive and reinstalls the OS from a know clean ISO.
The engine, which resides in the computer's BIOS, replaces a core Windows system file with its own, allowing files to be downloaded once the device is connected to the internet.
It's textbook social engineering and phishing, not hacking. Hacking involves exploiting known vulnerabilities in software, or finding new vulnerabilities through experimentation and/or fuzzing, and then exploiting them. None of this was even mentioned in the video.Dude, That is TEXTBOOK HACKING. Hollywood movies that show a pencilneck typing 500WPM on a laptop cracking into the pentagon are about as accurate to real hacking as Commando was to actual gunfights.
most, if not ALL hacking is done by social engineering. Infiltration, information acquisition. Some big hacking jobs are months, maybe YEARS in the making and require TEAMS of people to get done.
that phone rep would be reprimanded for giving out the pin code
It's textbook social engineering and phishing, not hacking. Hacking involves exploiting known vulnerabilities in software, or finding new vulnerabilities through experimentation and/or fuzzing, and then exploiting them. None of this was even mentioned in the video.
No hacks were seen.
This is baiting into a nomenclature debate. Exploiting operating systems and web applications precisely falls under the definition of hacking, as far as the term is applied to software computer hacking. Cracking usually refers to breaking encryption ciphers or brute forcing passwords, which isn't what I was describing.I believe you are describing cracking, not hacking.
This is baiting into a nomenclature debate. Exploiting operating systems and web applications precisely falls under the definition of hacking, as far as the term is applied to software computer hacking. Cracking usually refers to breaking encryption ciphers or brute forcing passwords, which isn't what I was describing.
Hacking as a term has been recently incorrectly broadened in definition to include anything someone does that deviates from the normal. See: 25 Cheap, Easy Gardening Hacks That Everyone Should Know | Idealist Revolution
I disagree with Chad Perrin's analysis of both terms. I would submit that hackers both explore and exploit while crackers just simply break things. Take the following sentences for instance:The difference is one word. Exploiting vs exploring. Hackers explore, crackers exploit.
Hacker vs. cracker - TechRepublic
It's textbook social engineering and phishing, not hacking. Hacking involves exploiting known vulnerabilities in software, or finding new vulnerabilities through experimentation and/or fuzzing, and then exploiting them. None of this was even mentioned in the video.
No hacks were seen.
That social engineering woman seems to be proud of the fact that she is good at being a scammer. Not something to be proud and smug about, And what idiot plays a soundfile of a baby crying with graphics of a baby? You would just play a sound file in foobar or what have you.
It was all pre-setup IMO. The guy that got the master password never even explained how or where he got it from. Anyone that stores their master password in a "cloud" is an idiot anyway.
It's textbook social engineering and phishing, not hacking. Hacking involves exploiting known vulnerabilities in software, or finding new vulnerabilities through experimentation and/or fuzzing, and then exploiting them. None of this was even mentioned in the video.
No hacks were seen.
"Our security has been compromised, we haven't been hacked."Aaaand that's why you aren't employed in network security.
"Damn it Johnson, we've been hacked!"
"Actually, the attacker stole our customers' credit card details and personal information via social engineering and phishing, obtaining network details and administration passwords, and then infiltrated our building posed as an intern and installed a remote-acess application that was later used to mass extract all the valuable information and cover up most of the action: technically not hacking"
"Our security has been compromised, we haven't been hacked."
I don't need or want a job in "network security" as I believe it's akin to dousing the Sun with water.
"Our security has been compromised, we haven't been hacked."
I don't need or want a job in "network security" as I believe it's akin to dousing the Sun with water.
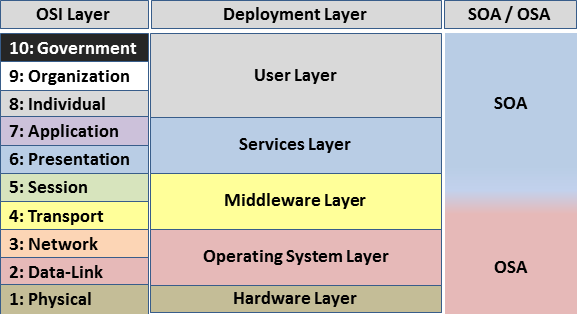
That sounds great until you realize layers 8-10 are made up. The OSI model has 7 layers. I've also pinged Chris Hadnagy to see if he'll respond to whether or not SE is actually hacking.Pointless differentiation nowadays.
All venues of obtaining illicit access fall under the aegis of hacking/cracking nowadays.
Or, if you want a real lesson, head out to Blackhat and Defcon and announce that "social engineering isn't hacking".
You'll be QUITE educated (one way or another) by the time they're done.
If you spend a month with Metasploit breaking into a system, and I spend a day and a half talking my way into a system, it doesn't matter.
We both obtained unauthorized access to a machine that doesn't belong to us.
The only difference is which layers of security we used to compromise a system. You attack on OSI layers 1-7. I attack on layers 8-10.
View attachment 694
We're both hackers/crackers.
My point was more that systems will never be secure and people in the infosec industry are basically using fear to sell snake oil.Security is a process. Not a product.
So yes, you could say it's akin to dousing the Sun with water.
You can't just sit back and lazy your way through the job.
The initial breach is rarely an actual hack when it comes to the high profile business related hacks. In most of those cases there were post-breach hacks used to get further into the networks.In that case, Sony PSN was never hacked, PayPal was never hacked, EA Origin was never hacked.... Pretty much every MAJOR hacking job in history does not contain what you consider 'hacking'.
I'm sure it was all dramatized and the guy admitted that he acted stupidly and clicked the link. This is exactly what the users that keep compromising their computers with cryptolocker are doing. I consider this video an excellent lesson for all those non-technical users out there. The way the hacker says that he could make the guy homeless just because he clicked the wrong things (and proceeded to log into his password manager, etc).This was all acting and nothing more.
TLDR Version of the video.
#1 Woman gains control of a cellphone account through phone support. Basic social engineering.
#2 Guy's laptop is compromised by clicking a fishing email that installs (presumably) remote access software.
Neither one was really hacking.
That sounds great until you realize layers 8-10 are made up.
The OSI model has 7 layers. I've also pinged Chris Hadnagy to see if he'll respond to whether or not SE is actually hacking.
My point was more that systems will never be secure and people in the infosec industry are basically using fear to sell snake oil.
Chris Hadnagy's response:Then you realize that Layers 1-7 are similarly "made up".
The OSI model has a weakness in that it assumes that all interactions happen within the codified seven layers.
This leaves security solutions that only secure those seven layers vulnerable to attacks that don't conform to any of the OSI layers (such as social engineering).
Hence the non-canonical recognition of layers above 7.
The term you're looking for is "risk management".
The only system that's 100% secure is one that's been powered down, disassembled and melted down into slag.
So yes, if you've got someone telling you that something will make you 100% secure, they're selling snake oil.
Basically, if someone wants into your system bad enough, they're getting in, regardless of what you do.
Security is the art of making the act of breaching your systems so not-worthwhile that they give up and move on to easier pickings. This is done by making the breaching of systems more difficult, hiding assets in ways that that are difficult to locate in an automated fashion and through being as innocuous a target as possible.
As was explained in the video, outside of malware (which is a "shotgun" approach), you could have a team of the best exploit programmers and social engineers on the planet.
Yippee.
If they aren't aware of your existence, they have exactly zero reason to come and attack you directly.
At every hacker con or group I've ever attended, nobody really drew lines between physical, software or social bypass. They're all equally valid.
About the only people who ever made any bones about it were usually young pedants who were convinced that sitting in front of a computer, clacking away at a keyboard was The One True Way...
Most of them were eventually disabused.
Umm... The only response to
is"Social engineering isn't hacking." true or false?
Doesn't that mean that "social engineering is hacking"?False!
And yet she did it anyways. It would seem threat of reprimand is not a fail safe security measure.