EnthusiastXYZ
Limp Gawd
- Joined
- Jun 26, 2020
- Messages
- 221
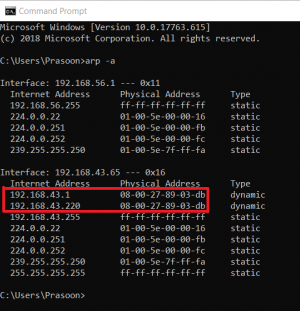
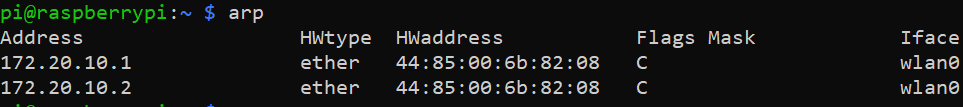
I set my UDM router (192.168.1.X) NAT firewall to drop all INPUT/FORWARD/OUTPUT Multicast+Broadcast IP range (224.0.0.0-255.255.255.255) packets along with all IGMP protocol packets and common UPnP, SSDP, mDNS, Bonjour, DIAL, and Chromecast port packets. Netfilter IPTables showed that there were dropped INPUT WAN packets from specific private (non-Multicast/Broadcast) IP ranges that were not part of my local network when ISP Gateway (192.168.0.X) was in Bridge Mode. When I set my ISP Gateway to Router Mode for further testing, Double-NAT was created. That was when I captured some strange traffic:
- Source 192.168.0.X (ISP router IP) - Destination 224.0.0.1 (IGMPv3 Membership Query)
- Source 192.168.1.Y (Rogue IP, not part of my LAN/WLAN) - Destination 224.0.0.1 (IGMPv3 Membership Query)
PCAP capture file showed that:
- ISP Gateway source MAC address was 02:00:00:00:00:04 and had VSS Monitoring Ethernet Trailer
- Rogue IP source MAC address was 02:00:00:00:00:07, had VSS Monitoring Ethernet Trailer, and 802.1Q VLAN tag
I remembered every static IP address, real MAC address, cloned MAC address, host names, and other info for every device on my LAN/WLAN by heart. I also had no VLAN set up at that time, which was more evidence that Rogue IP was not part of my local network. I wasn't sure to post or not to post the actual PCAP file, which could contain information about my network.
Questions:
- What was the Rogue IP? UDM was set to drop all IGMP/Multicast packets and it made sense for it to detect and drop packets if they were coming FROM ISP Gateway and/or Rogue IP, but why and how did UDM detect ISP Gateway and Rogue IP sending IGMP packets TO Multicast IP? ISP Gateway settings were incredibly limited, but UPnP was disabled. and UDM was the only device connected to ISP Gateway.
- Could IGMP allow you to discover devices, such as your neighbor's router when connecting to Multicast IP? I "sort of" comprehended how IGMP group joining and leaving worked, but I didn't think it would allow for discovery of other devices on WAN if all INBOUND/FORWARD/OUTBOUND IGMP packets were dropped...
- What was VSS Monitoring Ethernet Trailer? There was little information about it online. Supposedly it was meant for network tapping to improve performance, conduct surveillance, etc.
- Source 192.168.0.X (ISP router IP) - Destination 224.0.0.1 (IGMPv3 Membership Query)
- Source 192.168.1.Y (Rogue IP, not part of my LAN/WLAN) - Destination 224.0.0.1 (IGMPv3 Membership Query)
PCAP capture file showed that:
- ISP Gateway source MAC address was 02:00:00:00:00:04 and had VSS Monitoring Ethernet Trailer
- Rogue IP source MAC address was 02:00:00:00:00:07, had VSS Monitoring Ethernet Trailer, and 802.1Q VLAN tag
I remembered every static IP address, real MAC address, cloned MAC address, host names, and other info for every device on my LAN/WLAN by heart. I also had no VLAN set up at that time, which was more evidence that Rogue IP was not part of my local network. I wasn't sure to post or not to post the actual PCAP file, which could contain information about my network.
Questions:
- What was the Rogue IP? UDM was set to drop all IGMP/Multicast packets and it made sense for it to detect and drop packets if they were coming FROM ISP Gateway and/or Rogue IP, but why and how did UDM detect ISP Gateway and Rogue IP sending IGMP packets TO Multicast IP? ISP Gateway settings were incredibly limited, but UPnP was disabled. and UDM was the only device connected to ISP Gateway.
- Could IGMP allow you to discover devices, such as your neighbor's router when connecting to Multicast IP? I "sort of" comprehended how IGMP group joining and leaving worked, but I didn't think it would allow for discovery of other devices on WAN if all INBOUND/FORWARD/OUTBOUND IGMP packets were dropped...
- What was VSS Monitoring Ethernet Trailer? There was little information about it online. Supposedly it was meant for network tapping to improve performance, conduct surveillance, etc.
![[H]ard|Forum](/styles/hardforum/xenforo/logo_dark.png)