erek
[H]F Junkie
- Joined
- Dec 19, 2005
- Messages
- 10,875
Hope it's a good one. Hope it goes smoothly this time.
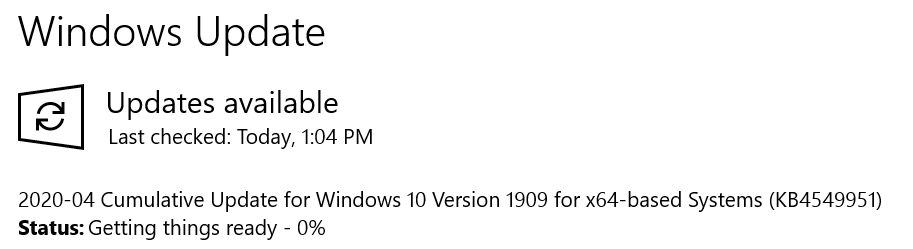
"If you see an Optional update available (you can see one in the screenshot), DON’T click Download and install. You’ll be bit by those bugs soon enough.
Don’t be spooked. Don’t be stampeded. And don’t install any patches that require you to click “Download and install now.”
If there are any immediate widespread problems protected by this month’s Patch Tuesday — a rare occurrence, but it does happen — we’ll let you know here, and at AskWoody.com, in very short order. Otherwise, sit back and watch while our usual monthly crowdsourced patch watch proceeds. Let’s see what problems arise."
https://www.computerworld.com/artic...-is-tomorrow-get-your-system-locked-down.html
"If you see an Optional update available (you can see one in the screenshot), DON’T click Download and install. You’ll be bit by those bugs soon enough.
Don’t be spooked. Don’t be stampeded. And don’t install any patches that require you to click “Download and install now.”
If there are any immediate widespread problems protected by this month’s Patch Tuesday — a rare occurrence, but it does happen — we’ll let you know here, and at AskWoody.com, in very short order. Otherwise, sit back and watch while our usual monthly crowdsourced patch watch proceeds. Let’s see what problems arise."
https://www.computerworld.com/artic...-is-tomorrow-get-your-system-locked-down.html
![[H]ard|Forum](/styles/hardforum/xenforo/logo_dark.png)