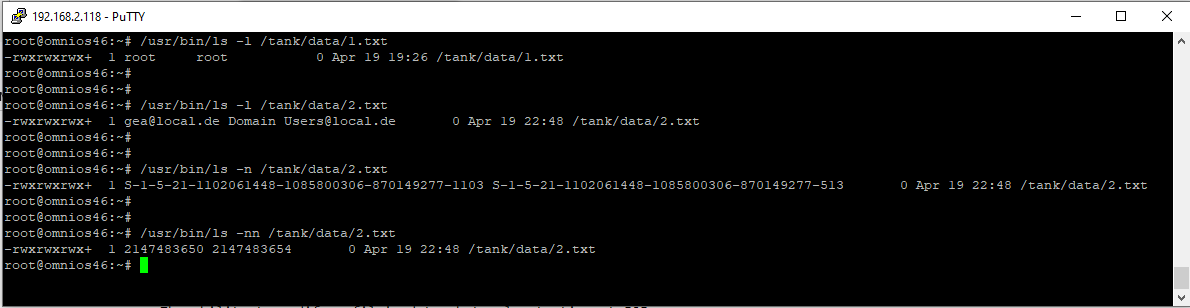
You do not want open Internet access to the management interface unless you use a VPN router ex GLinet and Wireguard. With VPN you can even simply use SMB. If you want to use Apache you can configure at /var/web-gui/_my/tools/apache/httpd.conf
Without VPN enabling a webbased Amazon S3 compatible cloud (minIO) is faster and more secure
Without VPN enabling a webbased Amazon S3 compatible cloud (minIO) is faster and more secure
![[H]ard|Forum](/styles/hardforum/xenforo/logo_dark.png)