Armenius
Extremely [H]
- Joined
- Jan 28, 2014
- Messages
- 42,084
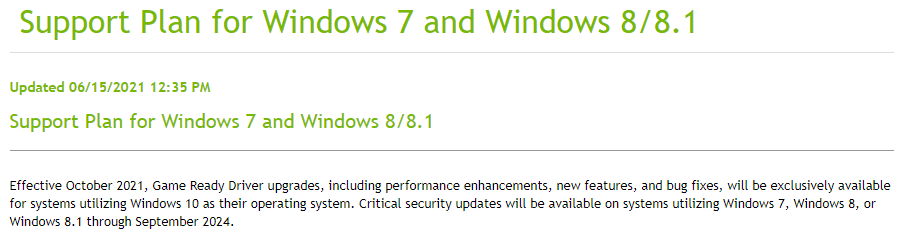
Game Ready updates will no longer be made for Windows operating systems prior to Windows 10 starting in October 2021. Critical security updates will still be offered on these legacy operating systems through September 2024.
https://nvidia.custhelp.com/app/answers/detail/a_id/5201/related/1
https://nvidia.custhelp.com/app/answers/detail/a_id/5201/related/1

![[H]ard|Forum](/styles/hardforum/xenforo/logo_dark.png)