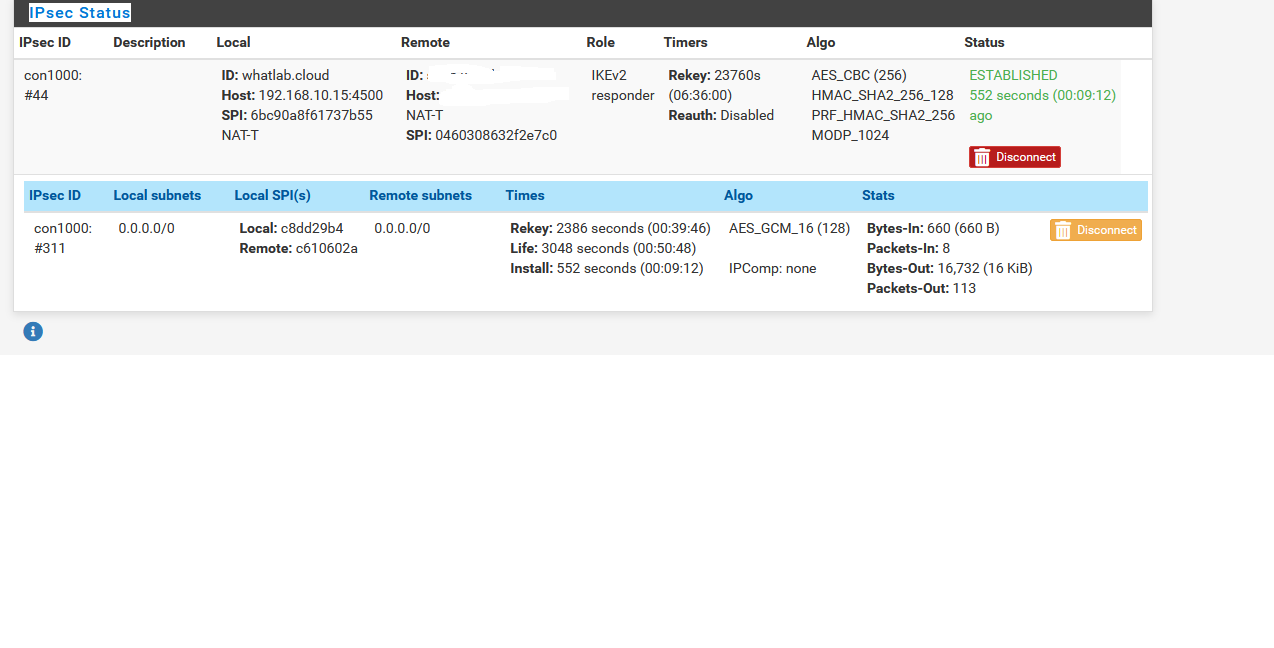
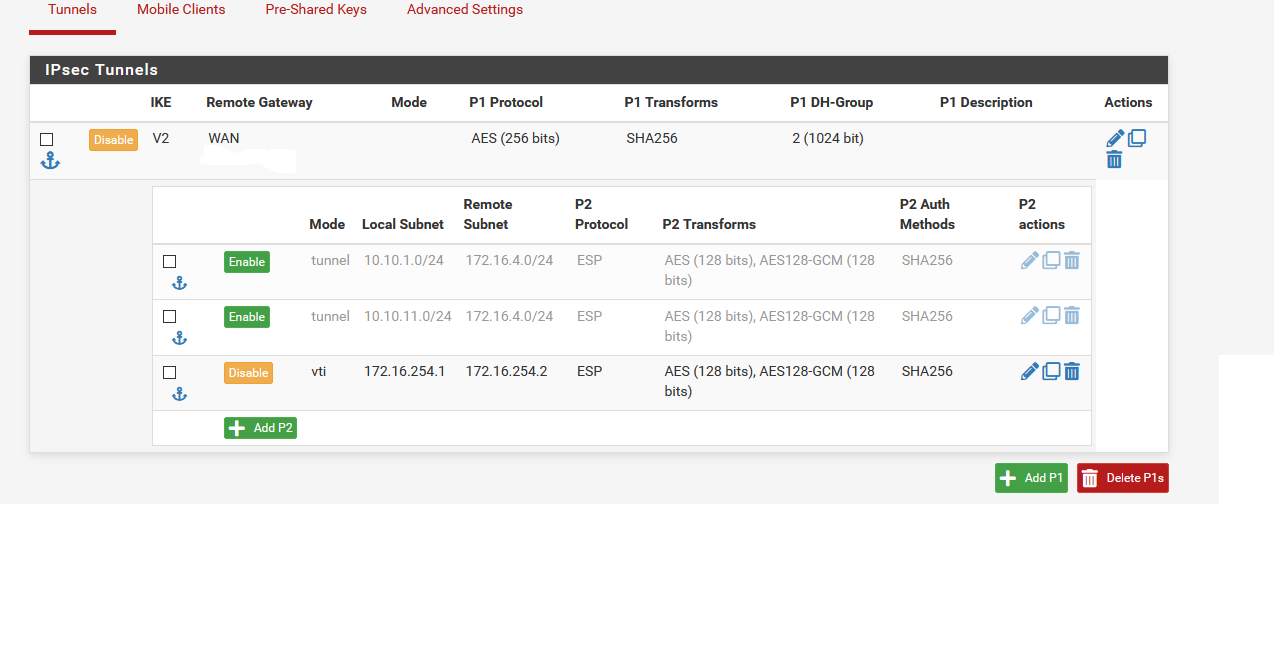
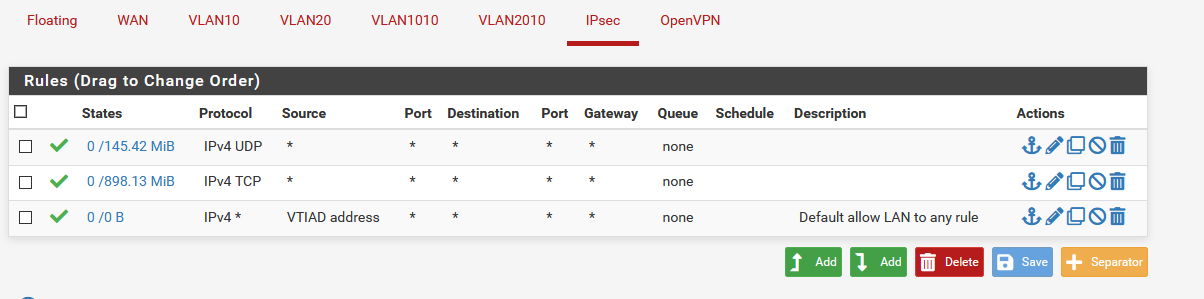
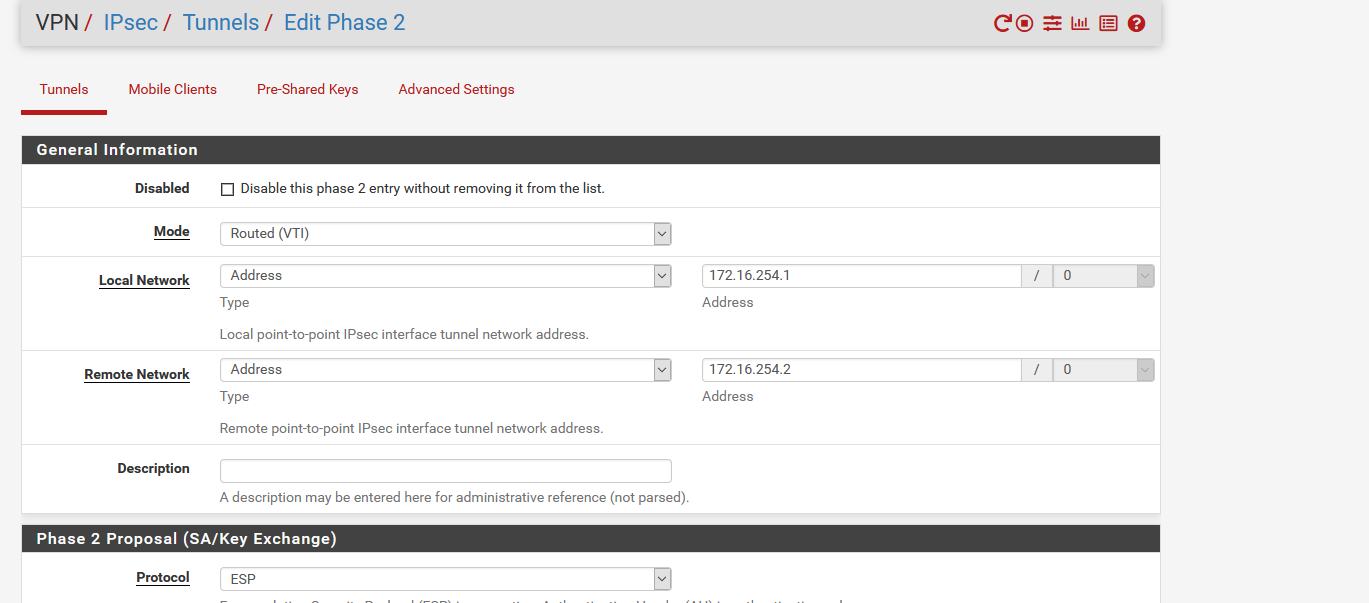
Sanity checking a few things here. Goal is IPSec that learns from BGP, since each site has subnets that are created/destroyed regularly (routed), and talk via BGP to update routing to the core.
2 sites. Site A, Site D (there will be a B/C eventually). PFSense handling core routing for both sites (2.5.0). IPSec tunnel with policy based routing configured (2 VLAN/Subnet per side are hard coded - management, and hte BGP Transit lan where the other routers talk to the PFSense core router).
EG Subnets at Site A:
10.10.1.X/24 - Management
10.10.11.X/24 - BGP to PFSense connection, basically .1 for PFsense, and .2/.3 for the next router (dual homed, redundant) down right now -
Current config has the one subnet for the DR side (hence site D) linked to both hard-coded VLANs at site A (ignore .2, it just went away - that doesn't need to route).
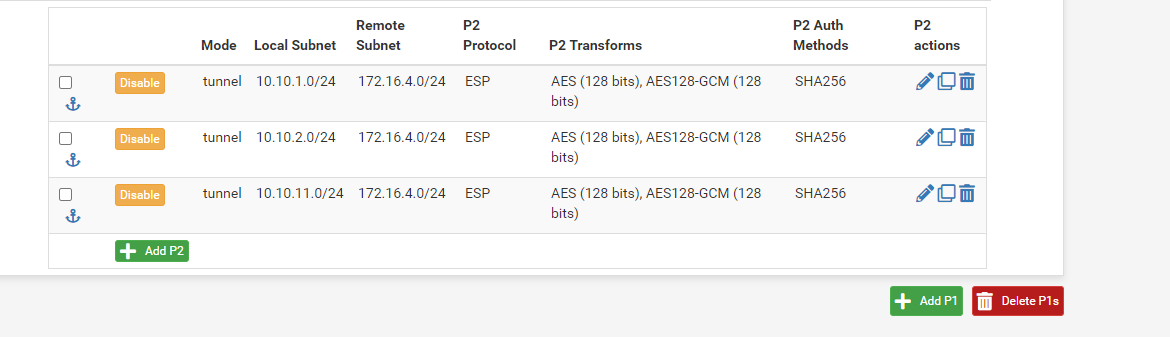
This works fine. On the BGP side, the next router down (T0 router, vs TNull for PFSense) is working perfectly, and the T1 routers/subnets created below are working fine:

20.0 and 21.0 are both On a T1 - goes T1->T0->PFSense (the lower layers are NSX-T, if you care).
Now - I want those routes to propagate across to site D, which only has the first set (1/2/11) accessible.
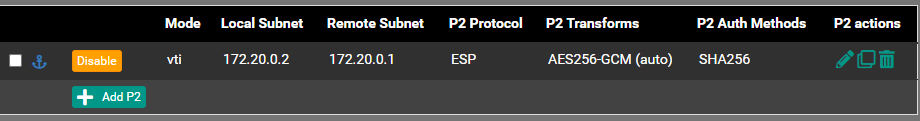
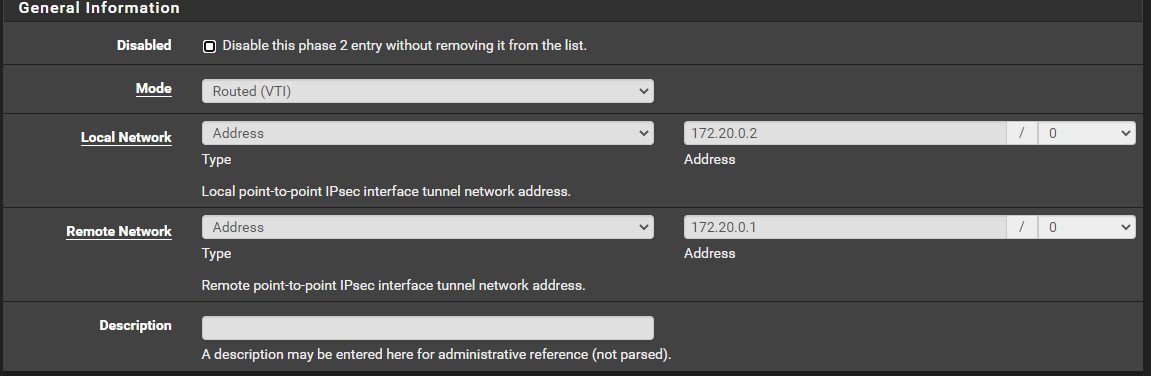
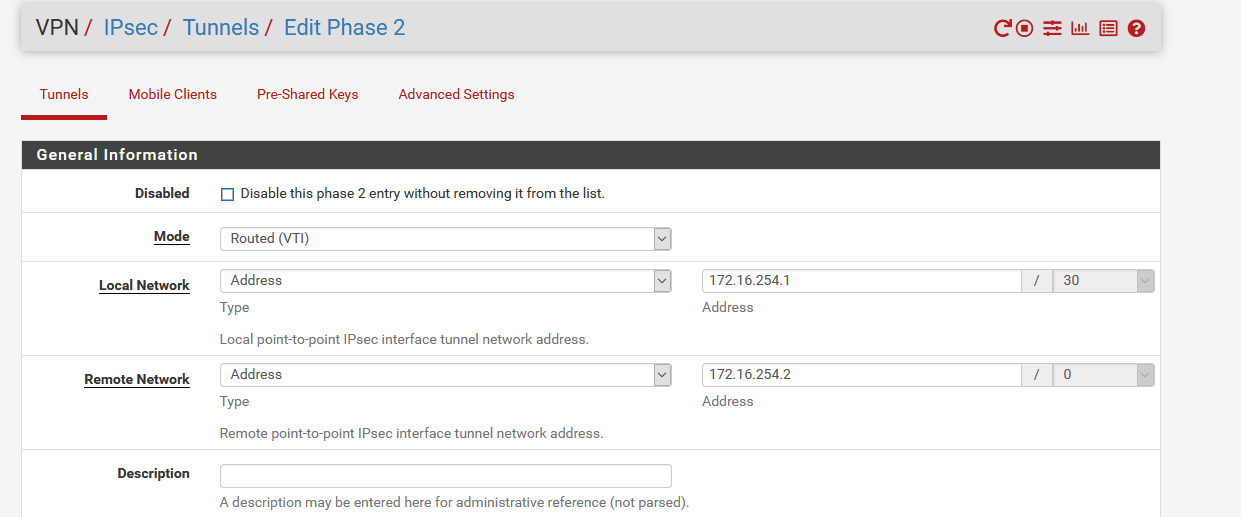
My understanding - I need to configure an IPSec VTI - I'll use 10.254.253.0/24 for this, because we're lazy and use /24 for everything, and put SiteA on .1. I'll also configure a .2 for SiteD, and... something then? That's where I get confused a bit.
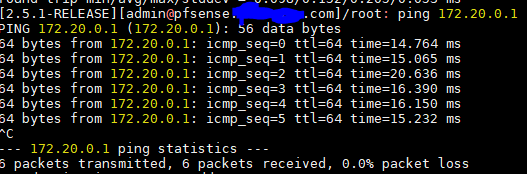
Will be trying this shortly. Expect questions to follow when this goes weird.
2 sites. Site A, Site D (there will be a B/C eventually). PFSense handling core routing for both sites (2.5.0). IPSec tunnel with policy based routing configured (2 VLAN/Subnet per side are hard coded - management, and hte BGP Transit lan where the other routers talk to the PFSense core router).
EG Subnets at Site A:
10.10.1.X/24 - Management
10.10.11.X/24 - BGP to PFSense connection, basically .1 for PFsense, and .2/.3 for the next router (dual homed, redundant) down right now -
Current config has the one subnet for the DR side (hence site D) linked to both hard-coded VLANs at site A (ignore .2, it just went away - that doesn't need to route).

This works fine. On the BGP side, the next router down (T0 router, vs TNull for PFSense) is working perfectly, and the T1 routers/subnets created below are working fine:

20.0 and 21.0 are both On a T1 - goes T1->T0->PFSense (the lower layers are NSX-T, if you care).
Now - I want those routes to propagate across to site D, which only has the first set (1/2/11) accessible.
My understanding - I need to configure an IPSec VTI - I'll use 10.254.253.0/24 for this, because we're lazy and use /24 for everything, and put SiteA on .1. I'll also configure a .2 for SiteD, and... something then? That's where I get confused a bit.
Will be trying this shortly. Expect questions to follow when this goes weird.
![[H]ard|Forum](/styles/hardforum/xenforo/logo_dark.png)