Cerulean
[H]F Junkie
- Joined
- Jul 27, 2006
- Messages
- 9,476
Greetings,
Before our hypervisor kicked the bucket taking down the file server VM with it, this is the way it worked:
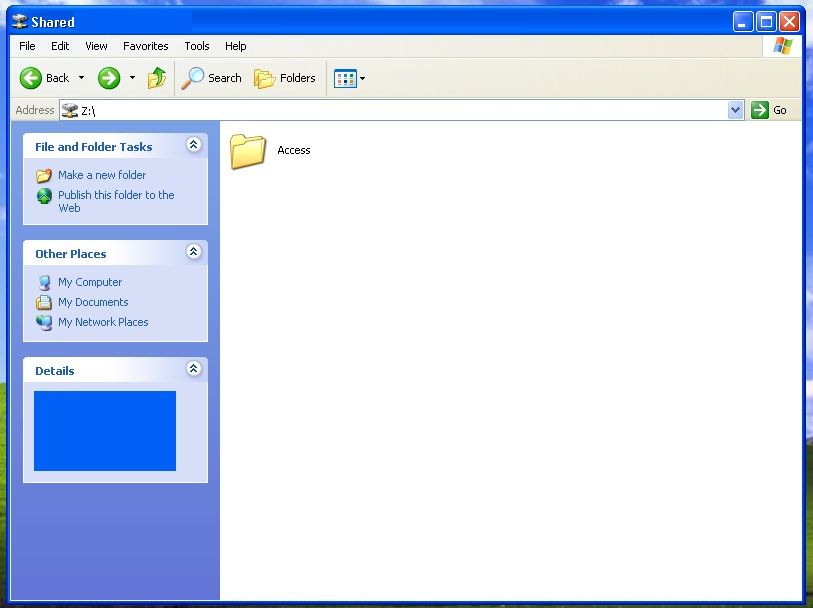
User would go to G:\ drive (network drive map to shared folder on file server VM).
Inside this drive was a handful of folders, each titled after the name of an overseas division.
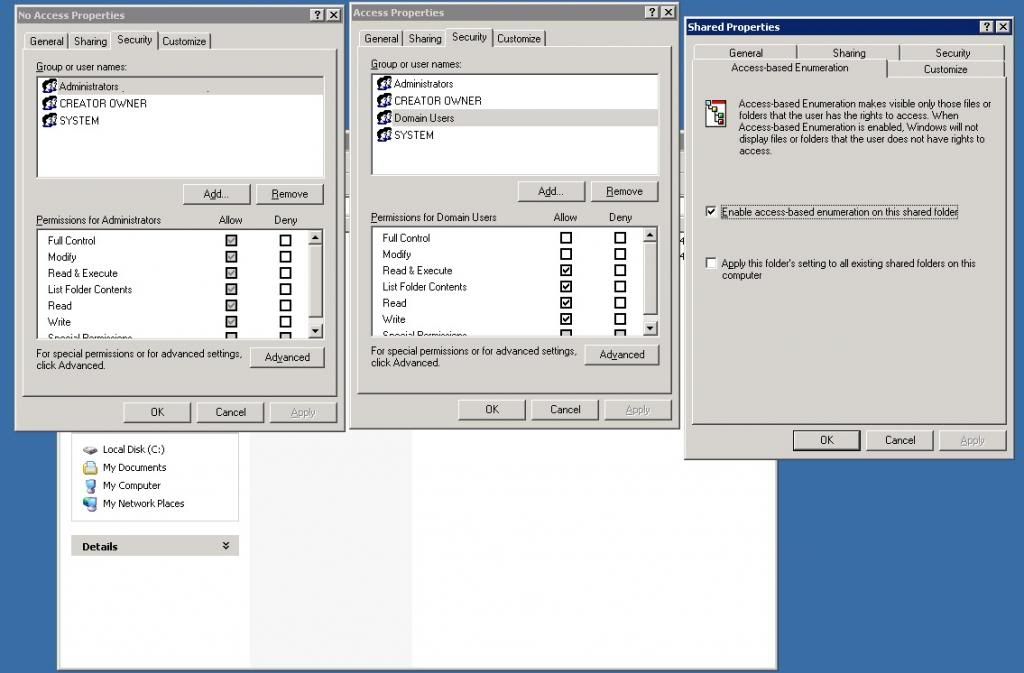
Each folder had NTFS permissions "Domain Admins" (Full Control) and "<name of overseas divison>" (Full Control). If the user did not have membership to all overseas divison groups, only the ones the user had access to would show up in the list of folders the user could open. This was nice and awesome because then the user would only see what they have access to.
Now the only permissions that changed after we finally got our file server back on the ground was the root folder NTFS & Shared permissions (a couple other things as well, but let's start from the root/simplest level).
If I recall correctly, Shared permissions had Domain Admins with Full Control, and either Authenticated Users or Domain Users with either Full Control or just Change+Read. The NTFS permissions had Domain Admins with Full Control, and either Authenticated Users or Domain Users with some read-only ability (I do not remember which checkboxes were checkmarked for the Permission Entry window, but nothing like being able to create/write/change/take ownership was checkmarked for sure).
I should have documented this and I was going to do it but I was too late and should have done it when I set it up.
Right now, users see all folders. If they try to open a folder they don't have access to, it will simply give them a pop-up message saying they don't have access to it.
EDIT: The first couple or few levels of folders do not inherit permissions. The folder structure is like this:
\\server-fs1.company.local\g\
\\server-fs1.company.local\g\Shared
\\server-fs1.company.local\g\DivisionA
\\server-fs1.company.local\g\DivisionA\Shared
\\server-fs1.company.local\g\\server1\g\DivisionA\Department1
\\server-fs1.company.local\g\DivisionA\Department2
\\server-fs1.company.local\g\DivisionA\Department3
\\server-fs1.company.local\g\DivisionB
\\server-fs1.company.local\g\DivisionB\Shared
\\server-fs1.company.local\g\DivisionB\Department1
\\server-fs1.company.local\g\DivisionB\Department2
\\server-fs1.company.local\g\DivisionB\Department3
\\server-fs1.company.local\g\DivisionC
\\server-fs1.company.local\g\DivisionC\Shared
\\server-fs1.company.local\g\DivisionC\Department1
\\server-fs1.company.local\g\DivisionC\Department2
\\server-fs1.company.local\g\DivisionC\Department3
'Shared' is a folder accessible by all within that level. For example, '\Shared' is available to the entire company regardless of what division you are part of; '\DivisionA\Shared' is only available to everyone at DivisionA.
EDIT2: Right now, this is how permissions are set
\
Shared permissions: Domain Admins (Full Control), Everyone (Change+Read), Domain Admins (Change+Read)
NTFS permissions: Authenticated Users (Traverse folder / execute file, List folder / read data, Read attributes, Read extended attributes, Read permissions; This folder, subfolders, and files), SYSTEM (Full control [every checkbox]; This folder, subfolders, and files)
\DivisionA
NTFS permissions: DivisionA (Traverse folder / execute file, List folder / read data, Read attributes, Read extended attributes, Read permissions; This folder, subfolders, and files), Domain Admins (Full control [every checkbox]; This folder, subfolders, and files), Authenticated Users (same as DivisionA), SYSTEM (same as Domain Admins), local Administrator (same as Domain Admins)
Before our hypervisor kicked the bucket taking down the file server VM with it, this is the way it worked:
User would go to G:\ drive (network drive map to shared folder on file server VM).
Inside this drive was a handful of folders, each titled after the name of an overseas division.
Each folder had NTFS permissions "Domain Admins" (Full Control) and "<name of overseas divison>" (Full Control). If the user did not have membership to all overseas divison groups, only the ones the user had access to would show up in the list of folders the user could open. This was nice and awesome because then the user would only see what they have access to.
Now the only permissions that changed after we finally got our file server back on the ground was the root folder NTFS & Shared permissions (a couple other things as well, but let's start from the root/simplest level).
If I recall correctly, Shared permissions had Domain Admins with Full Control, and either Authenticated Users or Domain Users with either Full Control or just Change+Read. The NTFS permissions had Domain Admins with Full Control, and either Authenticated Users or Domain Users with some read-only ability (I do not remember which checkboxes were checkmarked for the Permission Entry window, but nothing like being able to create/write/change/take ownership was checkmarked for sure).
I should have documented this and I was going to do it but I was too late and should have done it when I set it up.
Right now, users see all folders. If they try to open a folder they don't have access to, it will simply give them a pop-up message saying they don't have access to it.
EDIT: The first couple or few levels of folders do not inherit permissions. The folder structure is like this:
\\server-fs1.company.local\g\
\\server-fs1.company.local\g\Shared
\\server-fs1.company.local\g\DivisionA
\\server-fs1.company.local\g\DivisionA\Shared
\\server-fs1.company.local\g\\server1\g\DivisionA\Department1
\\server-fs1.company.local\g\DivisionA\Department2
\\server-fs1.company.local\g\DivisionA\Department3
\\server-fs1.company.local\g\DivisionB
\\server-fs1.company.local\g\DivisionB\Shared
\\server-fs1.company.local\g\DivisionB\Department1
\\server-fs1.company.local\g\DivisionB\Department2
\\server-fs1.company.local\g\DivisionB\Department3
\\server-fs1.company.local\g\DivisionC
\\server-fs1.company.local\g\DivisionC\Shared
\\server-fs1.company.local\g\DivisionC\Department1
\\server-fs1.company.local\g\DivisionC\Department2
\\server-fs1.company.local\g\DivisionC\Department3
'Shared' is a folder accessible by all within that level. For example, '\Shared' is available to the entire company regardless of what division you are part of; '\DivisionA\Shared' is only available to everyone at DivisionA.
EDIT2: Right now, this is how permissions are set
\
Shared permissions: Domain Admins (Full Control), Everyone (Change+Read), Domain Admins (Change+Read)
NTFS permissions: Authenticated Users (Traverse folder / execute file, List folder / read data, Read attributes, Read extended attributes, Read permissions; This folder, subfolders, and files), SYSTEM (Full control [every checkbox]; This folder, subfolders, and files)
\DivisionA
NTFS permissions: DivisionA (Traverse folder / execute file, List folder / read data, Read attributes, Read extended attributes, Read permissions; This folder, subfolders, and files), Domain Admins (Full control [every checkbox]; This folder, subfolders, and files), Authenticated Users (same as DivisionA), SYSTEM (same as Domain Admins), local Administrator (same as Domain Admins)
Last edited:
![[H]ard|Forum](/styles/hardforum/xenforo/logo_dark.png)