EnthusiastXYZ
Limp Gawd
- Joined
- Jun 26, 2020
- Messages
- 221
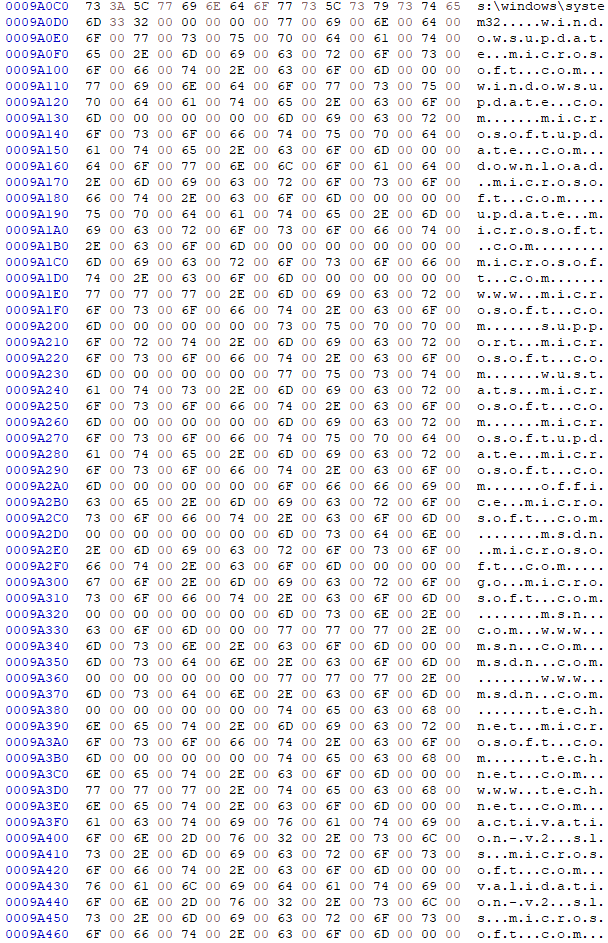
Microsoft hard-coded several domains (such as windowsupdate.com) into DNSAPI.dll file to make sure blocking those domains via hosts file is impossible. IP's for those domains change all the time, preventing IP-blocking firewalls from acting as a solution to block such telemetry. Stopping and/or disabling Windows DNS Cache Service (and/or Windows Update Service) does not prevent DNSAPI.dll from bypassing hosts file.
There are functional ways to block those domains, such as using Pi-Hole for local DNS server, but Pi-Hole does not work for VPN tunnels. VPN tunnels encrypt traffic and spoof IP's, but they don't prevent Microsoft from identifying your PC via mentioned domains. Blocking those telemetry domains is the only solution. There are 3rd party programs, such as YogaDNS, which function within VPN tunnels by acting as DNS drivers and blocking domains in hosts file, including domains hard-coded into DNSAPI.dll. The problem with YogaDNS is that it cannot be started up until after VPN tunnel is established, allowing Windows to send telemetry between the time VPN tunnel is established and time YogaDNS is started.
That leaves editing DNSAPI.dll as the only true solution to block domains hard-coded into it, but any attempt to HEX-edit DNSAPI.dll results in errors when programs, such as CCleaner, are launched. Disabling driver signature and integrity checks via BCDedit commands does not make a difference. How can I properly edit DNSAPI.dll to remove hard-coded domains and not get DNSAPI.dll-related errors?
There are functional ways to block those domains, such as using Pi-Hole for local DNS server, but Pi-Hole does not work for VPN tunnels. VPN tunnels encrypt traffic and spoof IP's, but they don't prevent Microsoft from identifying your PC via mentioned domains. Blocking those telemetry domains is the only solution. There are 3rd party programs, such as YogaDNS, which function within VPN tunnels by acting as DNS drivers and blocking domains in hosts file, including domains hard-coded into DNSAPI.dll. The problem with YogaDNS is that it cannot be started up until after VPN tunnel is established, allowing Windows to send telemetry between the time VPN tunnel is established and time YogaDNS is started.
That leaves editing DNSAPI.dll as the only true solution to block domains hard-coded into it, but any attempt to HEX-edit DNSAPI.dll results in errors when programs, such as CCleaner, are launched. Disabling driver signature and integrity checks via BCDedit commands does not make a difference. How can I properly edit DNSAPI.dll to remove hard-coded domains and not get DNSAPI.dll-related errors?
![[H]ard|Forum](/styles/hardforum/xenforo/logo_dark.png)