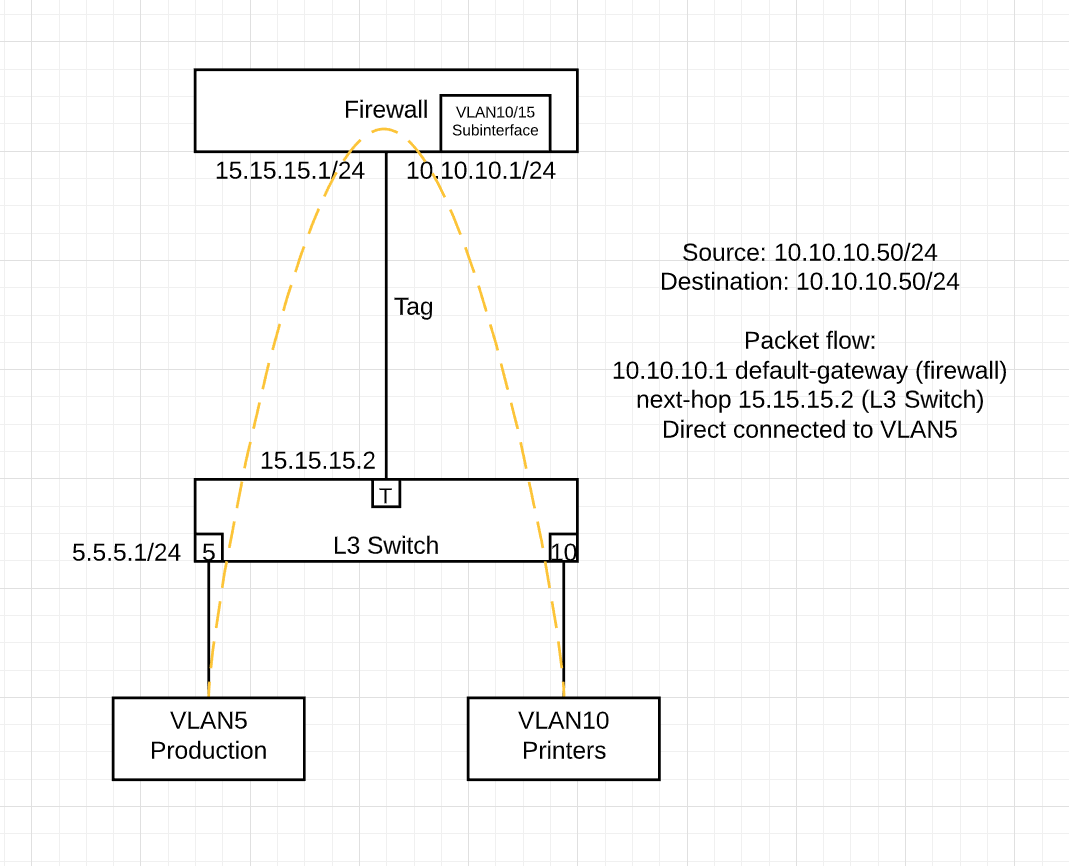
Hello all, im trying to get somthing setup and I think im having a brain fart. The setup is as follows (actual VLAN ID's and IP addresses are different):
VLAN 5 = Production - 5.5.5.0/24
VLAN 10 = Printers - 10.10.10.0/24
VLAN 15 = Uplink to firewall from switch - 15.15.15.0/30
I have several VLANs that all have their gateways on a layer 3 switch, with an uplink to the firewall for WAN access. Lets say VLAN 5 is the regular production network, I have the routing working so that this VLAN can talk to all other "layer 3" VLANs that also reside on the switch, and the switch has a static route of 0.0.0.0/0 pointing to the firewalls LAN uplink (this connection is VLAN 15, its a /30 subnet with the firewall port being 15.15.15.1 and the L3 switch is 15.15.15.2, with an IP policy sending traffic from .1 to the WAN port on the firewall). The issue I am having is that VLAN 10 (printers) has the gateway set as a port on the firewall (virtual port, VLAN 10) and I cant for the life of me figure out how to get it talking back to the other VLANs that reside on the L3 switch. I have 2 IP policies defined on the firewall that sends traffic between the L3 switch uplink port and the printer port (both ports are on the firewall), yet doing a ping from a host on the printer subnet to a host on the production subnet results in the packet getting confused on the L3 switch (Reply from 15.15.15.2: Destination host unreachable). I have another VLAN dedicated for servers, which hosts DHCP for all of the other VLANs, and also resides on the L3 switch. The printer subnet is able to pull addresses from the server (DHCP relay on the printer port), so I know the packets are at least getting through, and I can ping the gateway address of the printer subnet from the production VLAN (and vice versa), so I would assume the VLAN is tagged properly. What am I missing here? I thought that maybe since the packet was getting routed through the firewall, and coming out the uplink port that it would pick up the tag of that VLAN (15), so I added tags to the ports im testing on, but still nothing. Adding an IP address to the printer VLAN results in the same destination host unreachable error, but this time its coming from whatever IP I set VLAN 10 to on the L3 switch.
Hopefully that makes sense, im exhausted, which is probobly why im in this mess in the first place
Any help would be greatly appreciated.
VLAN 5 = Production - 5.5.5.0/24
VLAN 10 = Printers - 10.10.10.0/24
VLAN 15 = Uplink to firewall from switch - 15.15.15.0/30
I have several VLANs that all have their gateways on a layer 3 switch, with an uplink to the firewall for WAN access. Lets say VLAN 5 is the regular production network, I have the routing working so that this VLAN can talk to all other "layer 3" VLANs that also reside on the switch, and the switch has a static route of 0.0.0.0/0 pointing to the firewalls LAN uplink (this connection is VLAN 15, its a /30 subnet with the firewall port being 15.15.15.1 and the L3 switch is 15.15.15.2, with an IP policy sending traffic from .1 to the WAN port on the firewall). The issue I am having is that VLAN 10 (printers) has the gateway set as a port on the firewall (virtual port, VLAN 10) and I cant for the life of me figure out how to get it talking back to the other VLANs that reside on the L3 switch. I have 2 IP policies defined on the firewall that sends traffic between the L3 switch uplink port and the printer port (both ports are on the firewall), yet doing a ping from a host on the printer subnet to a host on the production subnet results in the packet getting confused on the L3 switch (Reply from 15.15.15.2: Destination host unreachable). I have another VLAN dedicated for servers, which hosts DHCP for all of the other VLANs, and also resides on the L3 switch. The printer subnet is able to pull addresses from the server (DHCP relay on the printer port), so I know the packets are at least getting through, and I can ping the gateway address of the printer subnet from the production VLAN (and vice versa), so I would assume the VLAN is tagged properly. What am I missing here? I thought that maybe since the packet was getting routed through the firewall, and coming out the uplink port that it would pick up the tag of that VLAN (15), so I added tags to the ports im testing on, but still nothing. Adding an IP address to the printer VLAN results in the same destination host unreachable error, but this time its coming from whatever IP I set VLAN 10 to on the L3 switch.
Hopefully that makes sense, im exhausted, which is probobly why im in this mess in the first place
Any help would be greatly appreciated.
![[H]ard|Forum](/styles/hardforum/xenforo/logo_dark.png)