Cerulean
[H]F Junkie
- Joined
- Jul 27, 2006
- Messages
- 9,476
Greetings,
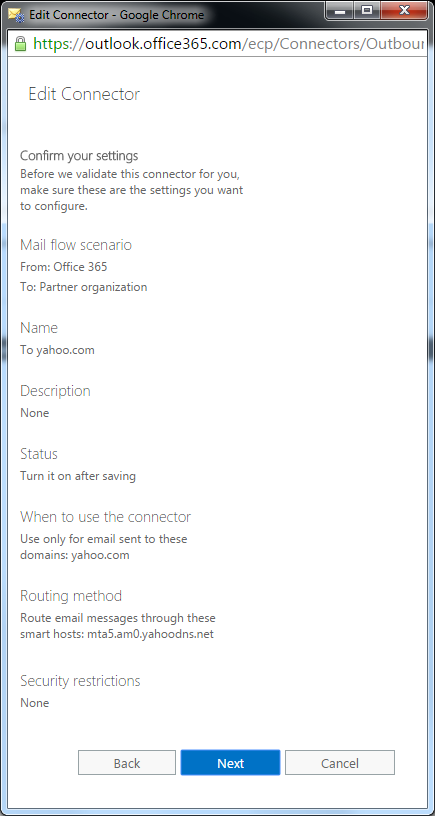
I've been having trouble with getting proper SPF record setup for my Exchange 365 which I use on domain szan.to. I have recently tried:
But Kitterman's tool at http://www.kitterman.com/spf/validate.html kicks it back saying szan.to is recursive. It validates if I remove szan.to from the SPF record. But, Yahoo complains of the same thing AppMailDev at http://www.appmaildev.com/en/spf/ is complaining about:
And straight out rejects my message. My mom is unable to send mail to szan.to I think for similar reasons, so she always e-mail my secondary e-mail addresses hosted with Google. Google Apps / GMail users have no problem sending e-mails to szan.to.
szan.to is hosted at DreamHost. DNS records of domain:
I changed modified the SPF record slightly before posting this, but validators say it isn't going to work and will still result in error. IntoDNS identifies four IP addresses belonging to the MX record.
Here is the full report from AppMailDev:
I've been having trouble with getting proper SPF record setup for my Exchange 365 which I use on domain szan.to. I have recently tried:
Code:
v=spf1 mx ptr include:szan-to.mail.protection.outlook.com include:szan.to include:spf.protection.outlook.com ~allBut Kitterman's tool at http://www.kitterman.com/spf/validate.html kicks it back saying szan.to is recursive. It validates if I remove szan.to from the SPF record. But, Yahoo complains of the same thing AppMailDev at http://www.appmaildev.com/en/spf/ is complaining about:
received-spf: Noneszan.to does not designate permitted sender hosts)
And straight out rejects my message. My mom is unable to send mail to szan.to I think for similar reasons, so she always e-mail my secondary e-mail addresses hosted with Google. Google Apps / GMail users have no problem sending e-mails to szan.to.
szan.to is hosted at DreamHost. DNS records of domain:
Code:
A 208.97.176.168
MX 0 szan-to.mail.protection.outlook.com.
NS ns1.dreamhost.com.
NS ns2.dreamhost.com.
NS ns3.dreamhost.com.
TXT v=spf1 mx ptr include:szan.to include:spf.protection.outlook.com ~all
autodiscover CNAME autodiscover.outlook.com.
mail CNAME autodiscover.outlook.com.I changed modified the SPF record slightly before posting this, but validators say it isn't going to work and will still result in error. IntoDNS identifies four IP addresses belonging to the MX record.
Here is the full report from AppMailDev:
This email is an automatic response from AdminSystem DKIM verifier service (1.0.0.5).
The service allows email senders to perform a simple check of SPF, DKIM and DomainKeys.
It is provided free of charge, in the hope that it is useful to the email community.
We welcome any feedback you may have at <[email protected]>.
Thank you for using the service.
AdminSystem Software Limited
============================================================
SPF result: TempError
============================================================
Domain: szan.to
IP: 207.46.163.140
SPF Record: szan.to
IN TXT = "v=spf1 mx ptr include:szan-to.mail.protection.outlook.com include:szan.to include:spf.protection.outlook.com ~all"
---SPF Trace Log---
Start to check SPF record
Sender IP:207.46.163.140
Sender Domain:szan.to
Parse Sender-IP 207.46.163.140
Query TEXT record from DNS server for: szan.to
[TXT]: v=spf1 mx ptr include:szan-to.mail.protection.outlook.com include:szan.to include:spf.protection.outlook.com ~all Parsing SPF record: v=spf1 mx ptr include:szan-to.mail.protection.outlook.com include:szan.to include:spf.protection.outlook.com ~all
Mechanisms: v=spf1
Mechanisms: mx
Testing mechanism mx
Query MX record from DNS server for: szan.to
[MX]: szan-to.mail.protection.outlook.com
Testing mechanism A:szan-to.mail.protection.outlook.com/128
Query A record from DNS server for: szan-to.mail.protection.outlook.com
[A]: 207.46.163.138
[A]: 207.46.163.170
[A]: 207.46.163.215
[A]: 207.46.163.247
Testing CIDR: source=207.46.163.140; 207.46.163.138/128 Testing CIDR: source=207.46.163.140; 207.46.163.170/128 Testing CIDR: source=207.46.163.140; 207.46.163.215/128 Testing CIDR: source=207.46.163.140; 207.46.163.247/128
Mechanisms: ptr
Query PTR record from DNS server for: 207.46.163.140, szan.to
[PTR]: mail-bn1lp0140.outbound.protection.outlook.com
Mechanisms: include:szan-to.mail.protection.outlook.com
Testing mechanism include:szan-to.mail.protection.outlook.com
Query TEXT record from DNS server for: szan-to.mail.protection.outlook.com
Exception: DNS server failure
============================================================
DomainKey result: none (no signature)
============================================================
============================================================
DKIM result: none (no signature)
============================================================
---Original Message Header---
x-sender: [email protected]
x-receiver: [email protected]
Received: from na01-bn1-obe.outbound.protection.outlook.com ([207.46.163.140]) by mail.appmaildev.com over TLS secured channel with Microsoft SMTPSVC(7.5.7600.16385);
Mon, 17 Mar 2014 23:38:27 -0400
Received: from BY2PR05MB096.namprd05.prod.outlook.com (10.242.38.19) by BY2PR05MB095.namprd05.prod.outlook.com (10.242.38.18) with Microsoft SMTP Server (TLS) id 15.0.898.11; Tue, 18 Mar 2014 03:38:11 +0000
Received: from BY2PR05MB096.namprd05.prod.outlook.com ([169.254.8.10]) by BY2PR05MB096.namprd05.prod.outlook.com ([169.254.8.140]) with mapi id 15.00.0898.005; Tue, 18 Mar 2014 03:38:10 +0000
From: Joshua Szanto <[email protected]>
To: "[email protected]" <[email protected]>
Subject: Test
Thread-Topic: Test
Thread-Index: Ac9CW3kQHt5b5cXRQROcLD0jxLVfLA==
Date: Tue, 18 Mar 2014 03:38:10 +0000
Message-ID: <d3ca4525c2f14aa489633512f967f4d9@BY2PR05MB096.namprd05.prod.outlook.com>
Accept-Language: en-US
Content-Language: en-US
X-MS-Has-Attach:
X-MS-TNEF-Correlator:
x-originating-ip: [108.206.5.182]
x-forefront-prvs: 0154C61618
x-forefront-antispam-report: SFV:NSPM;SFS10019001)(6009001)(428001)(199002)(189002)(83072002)(74706001)(74366001)(53806001)(15202345003)(95416001)(63696002)(54316002)(95666003)(19300405004)(74316001)(85852003)(69226001)(81686001)(551214005)(558084003)(81542001)(66066001)(80976001)(65816001)(87936001)(80022001)(59766001)(77982001)(56776001)(79102001)(51856001)(20776003)(555874004)(81342001)(85306002)(33646001)(54356001)(221733001)(74876001)(19580395003)(83322001)(94946001)(31966008)(76786001)(76576001)(16236675002)(46102001)(90146001)(47976001)(49866001)(77096001)(50986001)(76482001)(56816005)(47736001)(76796001)(76176001)(97186001)(47446002)(15975445006)(74662001)(86362001)(93136001)(97336001)(93516002)(87266001)(74502001)(81816001)(74482001)(4396001)(2656002)(92566001)(94316002)(24736002)(558944008);DIR:OUT;SFP:1102;SCL:1;SRVR:BY2PR05MB095;H:BY2PR05MB096.namprd05.prod.outlook.com;FPR:;MLV:sfv;PTR:InfoNoRecords;A:1;MX:1;LANG:en;
received-spf: Noneszan.to does not designate permitted sender hosts)
Content-Type: multipart/alternative;
boundary="_000_d3ca4525c2f14aa489633512f967f4d9BY2PR05MB096namprd05pro_"
MIME-Version: 1.0
X-OriginatorOrg: szan.to
Return-Path: [email protected]
X-OriginalArrivalTime: 18 Mar 2014 03:38:27.0898 (UTC) FILETIME=[864241A0:01CF425B]
Last edited:
![[H]ard|Forum](/styles/hardforum/xenforo/logo_dark.png)