DooKey
[H]F Junkie
- Joined
- Apr 25, 2001
- Messages
- 13,551
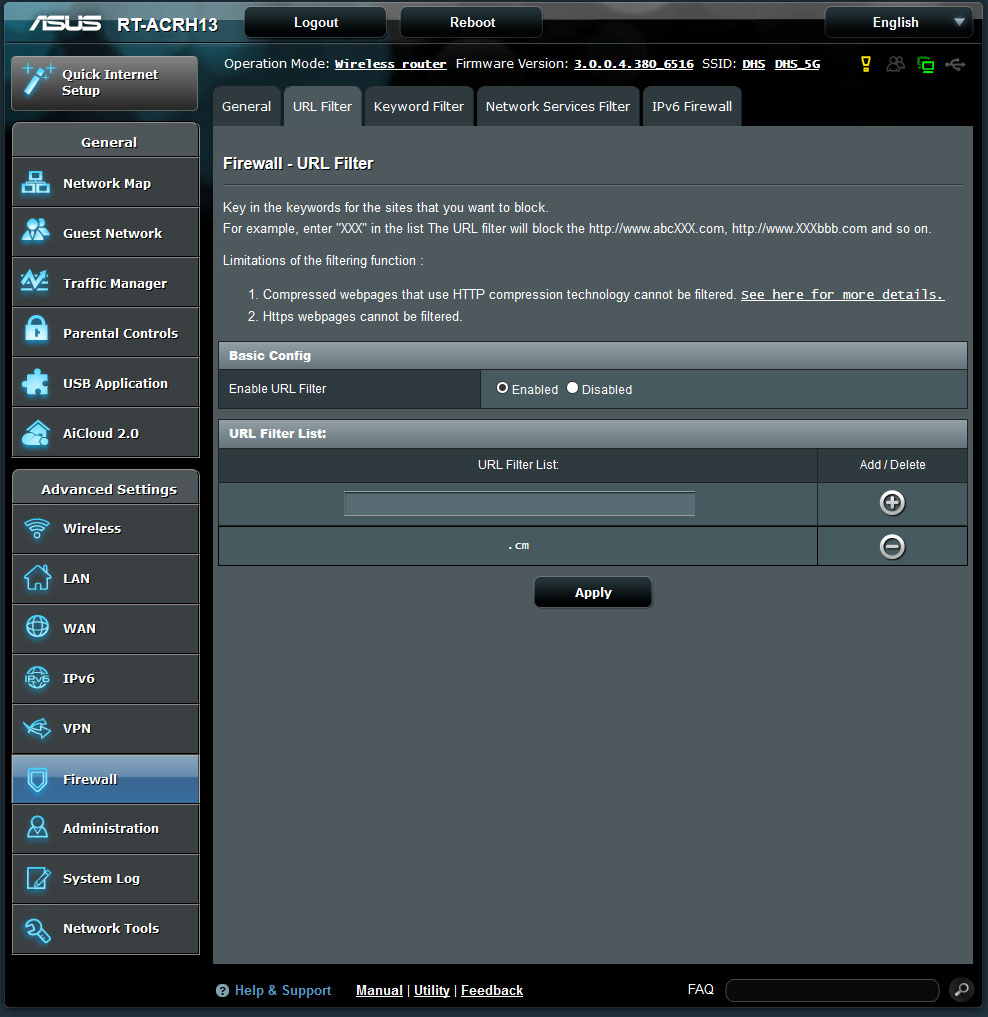
Apparently the self-proclaimed Spam King has gobbled up lots of .cm domains and they love to dish out malware. People around the web are finding this out in a bad way and their computers are getting hit with all sorts of garbage. Furthermore, these sites appear to automatically remove their code or download files if researchers try to go there to find out what's there. I don't know about anybody else, but I'm going to block the .cm domain so I don't accidently get hit with this kind of stuff. Thanks cageymaru.
Espn[dot]cm is one of more than a thousand so-called “typosquatting” domains hosted on the same Internet address (85.25.199.30), including aetna[dot]cm, aol[dot]cm, box[dot]cm, chase[dot]cm, citicards[dot]cm, costco[dot]cm, facebook[dot]cm, geico[dot]cm, hulu[dot]cm, itunes[dot]cm, pnc[dot]cm, slate[dot]cm, suntrust[dot]cm, turbotax[dot]cm, and walmart[dot]cm.
Espn[dot]cm is one of more than a thousand so-called “typosquatting” domains hosted on the same Internet address (85.25.199.30), including aetna[dot]cm, aol[dot]cm, box[dot]cm, chase[dot]cm, citicards[dot]cm, costco[dot]cm, facebook[dot]cm, geico[dot]cm, hulu[dot]cm, itunes[dot]cm, pnc[dot]cm, slate[dot]cm, suntrust[dot]cm, turbotax[dot]cm, and walmart[dot]cm.
![[H]ard|Forum](/styles/hardforum/xenforo/logo_dark.png)