Stanley Pain
2[H]4U
- Joined
- Apr 5, 2001
- Messages
- 2,510
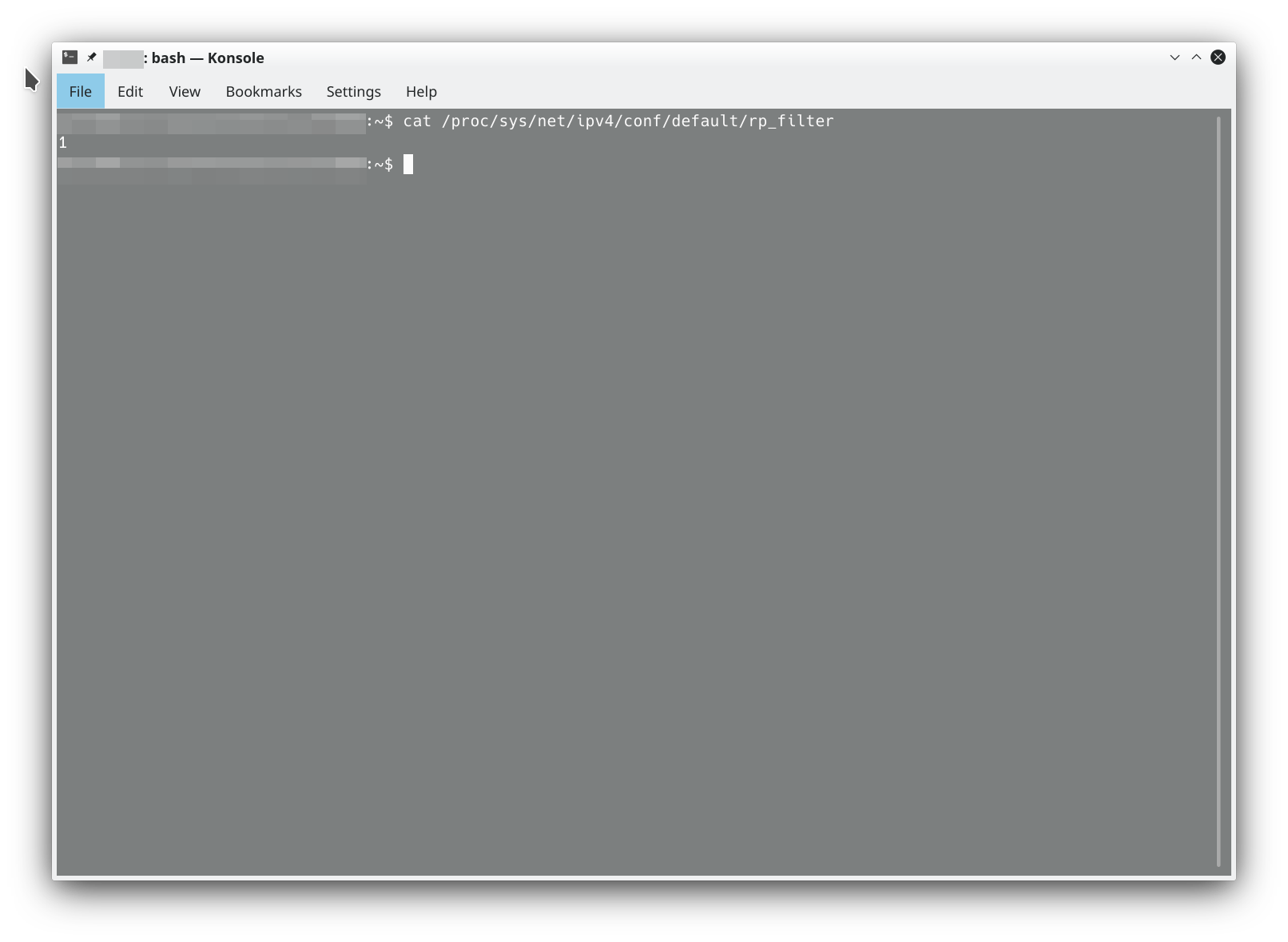
Fairly nasty VPN vuln across multiple Linux distros (and Android, MacOS and other *Nix OSes). Not systemd specific either since rc.d and sysV init systems were found to be vulnerable.
https://seclists.org/oss-sec/2019/q4/122
There are some mitigations discussed in the link. Definitely worth a read from an informative perspective and highly recommended if you have users out in the field or have large deployments. Going to be interesting to see how this plays out over the next few days.
https://seclists.org/oss-sec/2019/q4/122
There are some mitigations discussed in the link. Definitely worth a read from an informative perspective and highly recommended if you have users out in the field or have large deployments. Going to be interesting to see how this plays out over the next few days.
![[H]ard|Forum](/styles/hardforum/xenforo/logo_dark.png)