Hi All,
I have a basic understanding of networking concepts (OSI layers, etc), and read up on VLANs in order to setup the VLANs in our organization.
First things first, I'd like to put wireless guest clients on a separate VLAN
Equipment on hand
Fortigate Router/Firewall
Cisco SG300 core switch
Unifi Access Points
Current Setup
Everything is on a single /24 network, untagged and without VLANs at all.
Fortigate - no VLAN configured, everything is on the 'internal'/management network.
Cisco SG300 - while this is running in L3 mode, nothing is configured with regards to VLAN.
Unifi APs - connected to ports on the SG300; have 2 SSIDs presently configured but are essentially on the same subnet. One SSID ideally for internal, authorized clients - other for guests whom Id like on the separate VLAN
Unifi Controller
What I'd like to do:
Is there any end-to-end tutorial on configuring VLANs I could read up on? The tutorials I see mostly deal with single devices but don't really talk about how to have the switch properly talk to the router, and to the APs in particular.
I hope I haven't left out any other necessary information needed to help set this thing up.
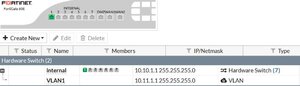
In my screenshot - 10.10.1.0/24 - Original network; 10.11.1.0/24 - VLAN created for guest clients.
Thanks!
I have a basic understanding of networking concepts (OSI layers, etc), and read up on VLANs in order to setup the VLANs in our organization.
First things first, I'd like to put wireless guest clients on a separate VLAN
Equipment on hand
Fortigate Router/Firewall
Cisco SG300 core switch
Unifi Access Points
Current Setup
Everything is on a single /24 network, untagged and without VLANs at all.
Fortigate - no VLAN configured, everything is on the 'internal'/management network.
Cisco SG300 - while this is running in L3 mode, nothing is configured with regards to VLAN.
Unifi APs - connected to ports on the SG300; have 2 SSIDs presently configured but are essentially on the same subnet. One SSID ideally for internal, authorized clients - other for guests whom Id like on the separate VLAN
Unifi Controller
What I'd like to do:
- Create VLAN 1 on Fortigate
- Setup DHCP for VLAN 1 on Fortigate
- Setup SG300 to properly recognize untagged packets (the main, original organization) and packets with VLAN1 (guest network)
- Put guest network on VLAN 1 (this is the easiest to do, done on the Unifi controller)
- Have existing computers connect to the untagged, original /24 network, as well as those who connect to the proper non-guest network.
Is there any end-to-end tutorial on configuring VLANs I could read up on? The tutorials I see mostly deal with single devices but don't really talk about how to have the switch properly talk to the router, and to the APs in particular.
I hope I haven't left out any other necessary information needed to help set this thing up.
In my screenshot - 10.10.1.0/24 - Original network; 10.11.1.0/24 - VLAN created for guest clients.
Thanks!
![[H]ard|Forum](/styles/hardforum/xenforo/logo_dark.png)