http://www.512tech.com/technology/l...d-over-security-flaws/BcAs80f0W8yrX4o59S1jmI/
Did you guys see this? It's quite scandalous.
I hope the shareholders nail their asses to the wall on this. It's high time that AMD's PR department gets a complete overhaul. They have been ruining hardware websites and forums just like this one for years now. They completely abuse the tech journalists and they infest tech forums with their viral scum. The last time I checked, AMD was the only company out there that actually encourages their own employees to post on social media, without disclosing their affiliation. I guess I shouldn't be surprised seeing as they didn't disclose the Spectre bug.
Did you guys see this? It's quite scandalous.
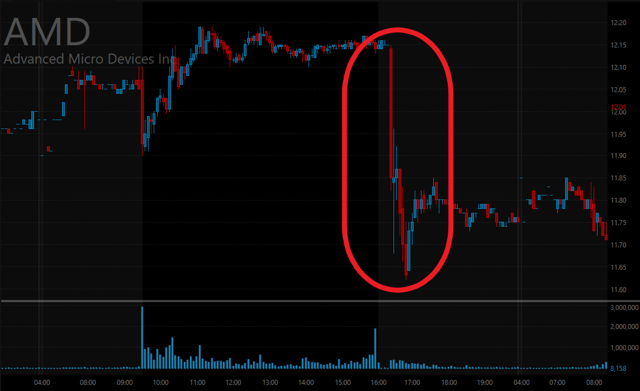
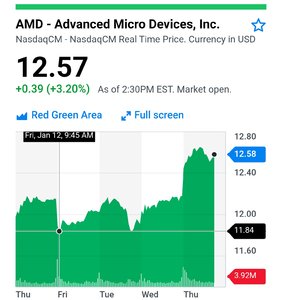
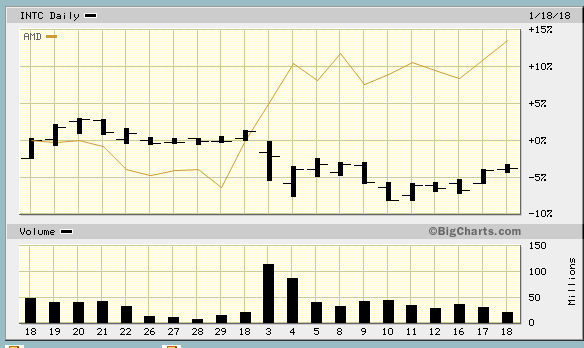
I have known for years now that the PR department at AMD is corrupt and cannot be trusted. But to hear Lisa Su recently claiming that AMD's processors were unaffected by the Meltdown and Spectre bugs, it really made me feel that their company is corrupt right to the bone. Spectre has *always* been the more serious of the bugs in terms of performance loss, and AMD has *always* been affected by it.AMD “made false and/or misleading statements and/or failed to disclose that: (i) a fundamental security flaw in AMD’s processor chips renders them susceptible to hacking,” the Rosen Law Firm’s filing says. “As a result, AMD’s public statements were materially false and misleading at all relevant times.”
The suits claim AMD made misleading statements through security filings and other public statements from Feb. 21, 2017 to Jan. 11 of this year.
I hope the shareholders nail their asses to the wall on this. It's high time that AMD's PR department gets a complete overhaul. They have been ruining hardware websites and forums just like this one for years now. They completely abuse the tech journalists and they infest tech forums with their viral scum. The last time I checked, AMD was the only company out there that actually encourages their own employees to post on social media, without disclosing their affiliation. I guess I shouldn't be surprised seeing as they didn't disclose the Spectre bug.
![[H]ard|Forum](/styles/hardforum/xenforo/logo_dark.png)