The Lurker
Fully [H]
- Joined
- Jul 1, 2001
- Messages
- 19,081
I have been playing around with Sophos UTM for about 6 months now and I think I have pretty much nailed down how to administer it for our needs. But there are a few things I still have questions about, none affect network users day to day directly but I wonder about the imperceptible impacts.
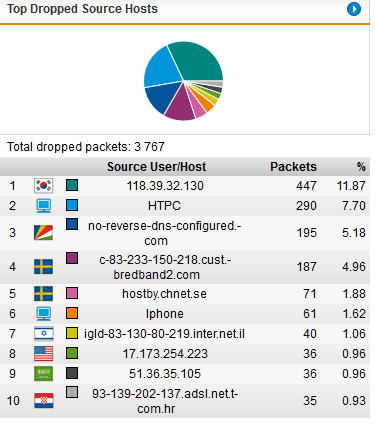
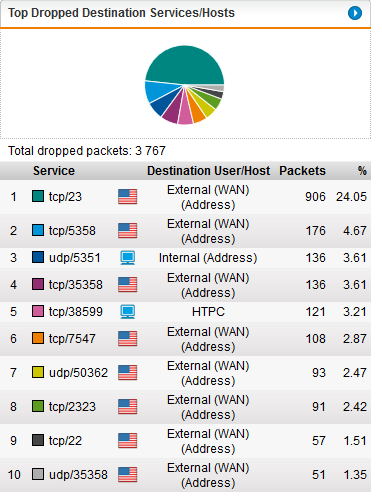
One thing that pops out at me constantly is the shear volume of dropped packets originating from internal traffic. Currently I only allow devices on the network to communicate only over certain ports, as created upon initial install, and then I added a few more for things like steam, team viewer, NTP, facetime and etc. But the number of packet being dropped is still tremendous. Sometimes in the 20k range on a particularly busy day spread out over multiple hosts. As I said, it doesnt affect usability but I still wonder about the impact. For example, Google Home will not stop trying to hit the google DNS server.
This morning, as an experiment, I allowed all network addresses access to all ports to the internet to see what happens to the packet drops.
My question is. 1. Is this OK? 2. What do you do with your outbound traffic?
One thing that pops out at me constantly is the shear volume of dropped packets originating from internal traffic. Currently I only allow devices on the network to communicate only over certain ports, as created upon initial install, and then I added a few more for things like steam, team viewer, NTP, facetime and etc. But the number of packet being dropped is still tremendous. Sometimes in the 20k range on a particularly busy day spread out over multiple hosts. As I said, it doesnt affect usability but I still wonder about the impact. For example, Google Home will not stop trying to hit the google DNS server.
This morning, as an experiment, I allowed all network addresses access to all ports to the internet to see what happens to the packet drops.
My question is. 1. Is this OK? 2. What do you do with your outbound traffic?
![[H]ard|Forum](/styles/hardforum/xenforo/logo_dark.png)