I have building an application platform, and plan to deploy it on Google Cloud (GCP) once it becomes a viable product and makes money. ;-)
In the interim, I would like to setup my home network to be able to run the same platform as the one that will eventually run on GCP.
The question I have is not about if I should just use CGP, another Cloud provider, etc.
Lets take it for granted that it is a good idea to run this from my own infrastructure at home.
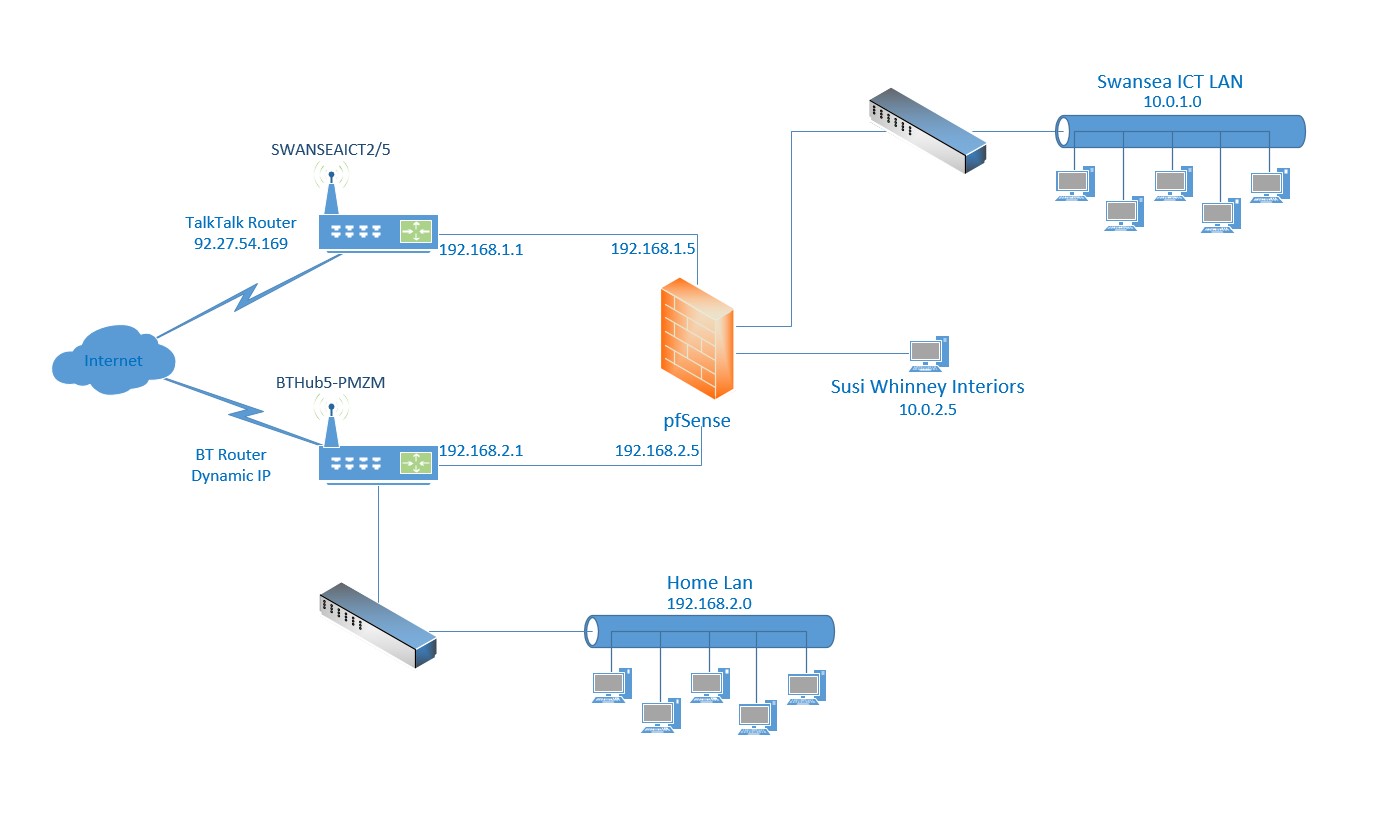
Here is a basic diagram of as is network at my soho network.
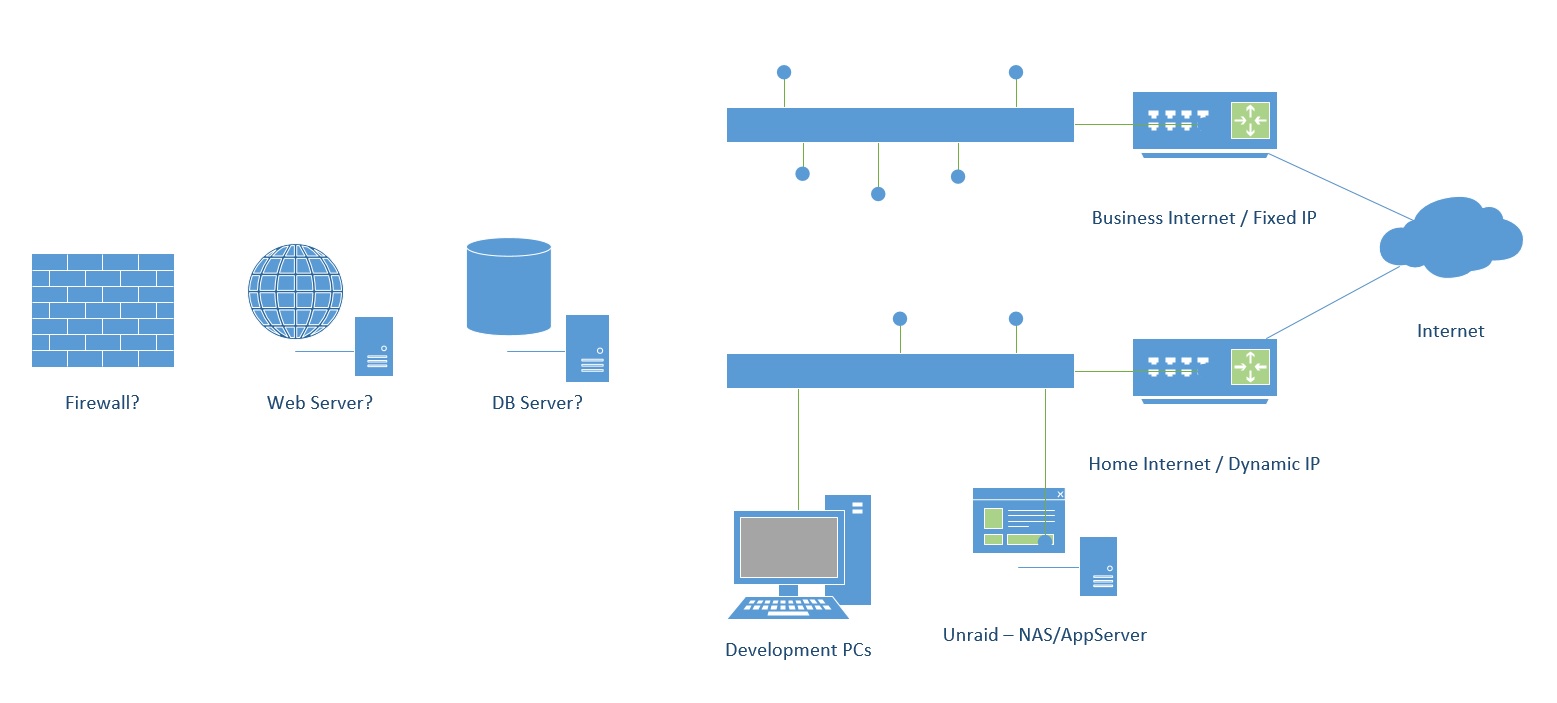
Like most home networks, I have a home ISP service with dynamic IP, and where I do all my development, and a NAS (Unraid Server), and a bunch of VMs that allow me to create a dev\test infrastructure.
I also have a HomeOffice ISP service with Static IP, where I would like to put all my "Production" servers for my platform\product.
My needs are:
In the interim, I would like to setup my home network to be able to run the same platform as the one that will eventually run on GCP.
The question I have is not about if I should just use CGP, another Cloud provider, etc.
Lets take it for granted that it is a good idea to run this from my own infrastructure at home.
Here is a basic diagram of as is network at my soho network.

Like most home networks, I have a home ISP service with dynamic IP, and where I do all my development, and a NAS (Unraid Server), and a bunch of VMs that allow me to create a dev\test infrastructure.
I also have a HomeOffice ISP service with Static IP, where I would like to put all my "Production" servers for my platform\product.
My needs are:
- What approach/setup do I use to deploy/connect my dev components to the production network
- What firewall setup would you recommend (right now only ones are the one in those cheap routers provided by the IPSs)
- Is there a setup that I could use to locally connect the production network to the dev/home network?
![[H]ard|Forum](/styles/hardforum/xenforo/logo_dark.png)