- Joined
- Aug 20, 2006
- Messages
- 13,000
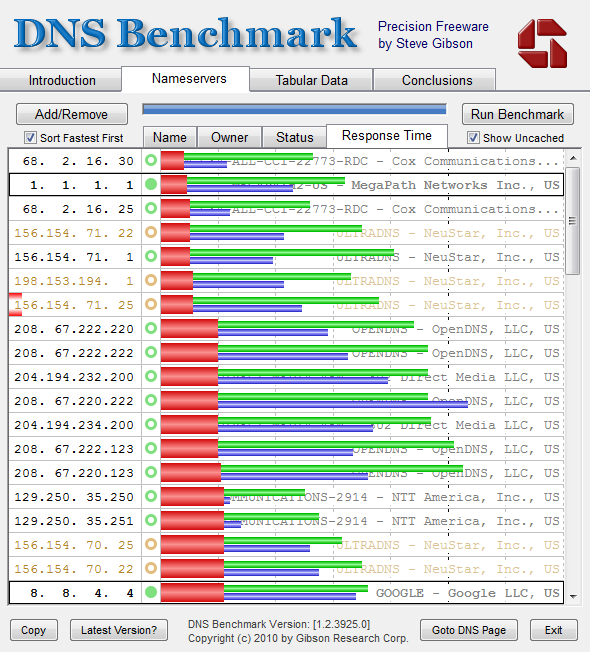
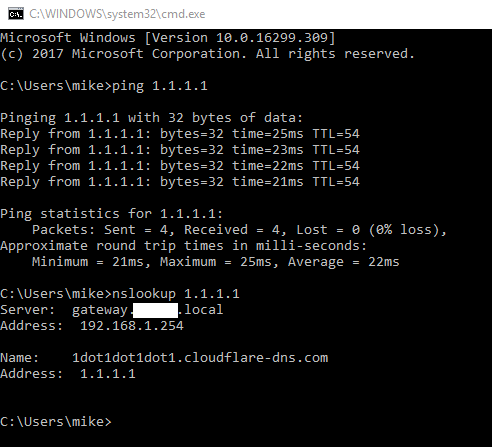
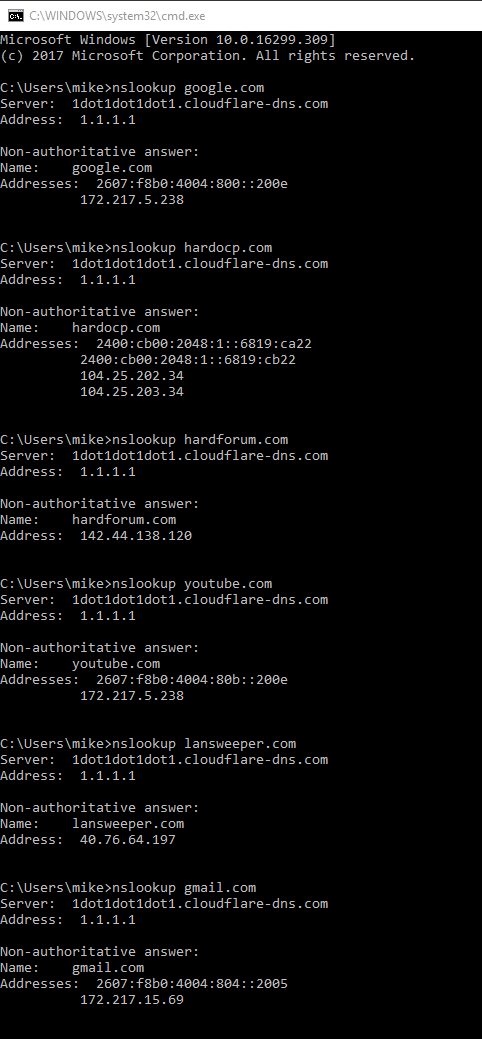
Cloudflare has launched a new DNS service, 1.1.1.1, which promises both speed and privacy, allowing users to keep their website queries private. According to DNSPerf’s current rankings, 1.1.1.1 is placed first with a query speed of 14.24 ms. Users may visit https://1.1.1.1/ from any device to get started.
What many Internet users don't realize is that even if you're visiting a website that is encrypted — has the little green lock in your browser — that doesn't keep your DNS resolver from knowing the identity of all the sites you visit. That means, by default, your ISP, every wifi network you've connected to, and your mobile network provider have a list of every site you've visited while using them.
What many Internet users don't realize is that even if you're visiting a website that is encrypted — has the little green lock in your browser — that doesn't keep your DNS resolver from knowing the identity of all the sites you visit. That means, by default, your ISP, every wifi network you've connected to, and your mobile network provider have a list of every site you've visited while using them.
![[H]ard|Forum](/styles/hardforum/xenforo/logo_dark.png)