Hilbert over at guru3d posted a cool tool that will show if your system is all patched up from the Bios and OS perspective. The author is Steve Gibson from Gibson security research. The tool has a toggle on and off button if you were interested in before and after performance impact from the security patches. Here is the page http://www.guru3d.com/news-story/download-inspectre-meltdown-and-spectre-check-tool.html
Navigation
Install the app
How to install the app on iOS
Follow along with the video below to see how to install our site as a web app on your home screen.
Note: This feature may not be available in some browsers.
More options
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Inspectre:Meltdown & Sprectre check tool!
- Thread starter bud1974
- Start date
Nice little tool, been using Gibson's online port scanner for years.
Direct Link:
https://www.grc.com/inspectre.htm
Direct Link:
https://www.grc.com/inspectre.htm
Powershell, from microsoft last week:
https://www.powershellgallery.com/packages/SpeculationControl
Automating it over the network:
https://blogs.technet.microsoft.com...ifying-spectre-meltdown-protections-remotely/
https://www.powershellgallery.com/packages/SpeculationControl
Automating it over the network:
https://blogs.technet.microsoft.com...ifying-spectre-meltdown-protections-remotely/
Denpepe
2[H]4U
- Joined
- Oct 26, 2015
- Messages
- 2,269
Nice little tool, been using Gibson's online port scanner for years.
Direct Link:
https://www.grc.com/inspectre.htm
Hmm clicked that link, edge was not happy, claims its a scammer site and to stay away.
Hmm clicked that link, edge was not happy, claims its a scammer site and to stay away.
Yeah, from the same company that screwed up the patches, figures. Gibson is reputable.
Ruiner
2[H]4U
- Joined
- Aug 22, 2000
- Messages
- 3,093
My ivy bridge has a sad.
thesmokingman
Supreme [H]ardness
- Joined
- Nov 22, 2008
- Messages
- 6,617
GRC is very old school.
Deadjasper
2[H]4U
- Joined
- Oct 28, 2001
- Messages
- 2,584
Edge, LOL. 
Gibson Research is a respected company and website.
I wouldn't use the word "respected", because he is definitely not in various circles.
Legitimate, yes, they are not intentionally trying to serve up malware. Is their basic message on whatever security-issue-of-the-day usually grounded in some meaningful truth, yes. Are they alarmist blowhards that often aim in the wrong direction? Oh yes. The stance on "silent firewall ports" back in the day was serious facepalm bad advice.
I wouldn't use the word "respected", because he is definitely not in various circles.
Legitimate, yes, they are not intentionally trying to serve up malware. Is their basic message on whatever security-issue-of-the-day usually grounded in some meaningful truth, yes. Are they alarmist blowhards that often aim in the wrong direction? Oh yes. The stance on "silent firewall ports" back in the day was serious facepalm bad advice.
Steve Gibson has been around a long time and is respected.
I think that is accurate.
He wrote the program Spinrite and has done a ton of other stuff.
Your opinion shall be noted in the annals of the internet forever and ever.
.
so I'm not sure that GRC tool is all that useful... I had messed about trying to use the VMware driver tool to patch the microcode for my i7-4770K /Z87X-UD3H rig.. blah blah blah... more reading makes it look like this isn't a viable solution as the microcode patch is applied too late in start up for windows to enable the spectre protections..
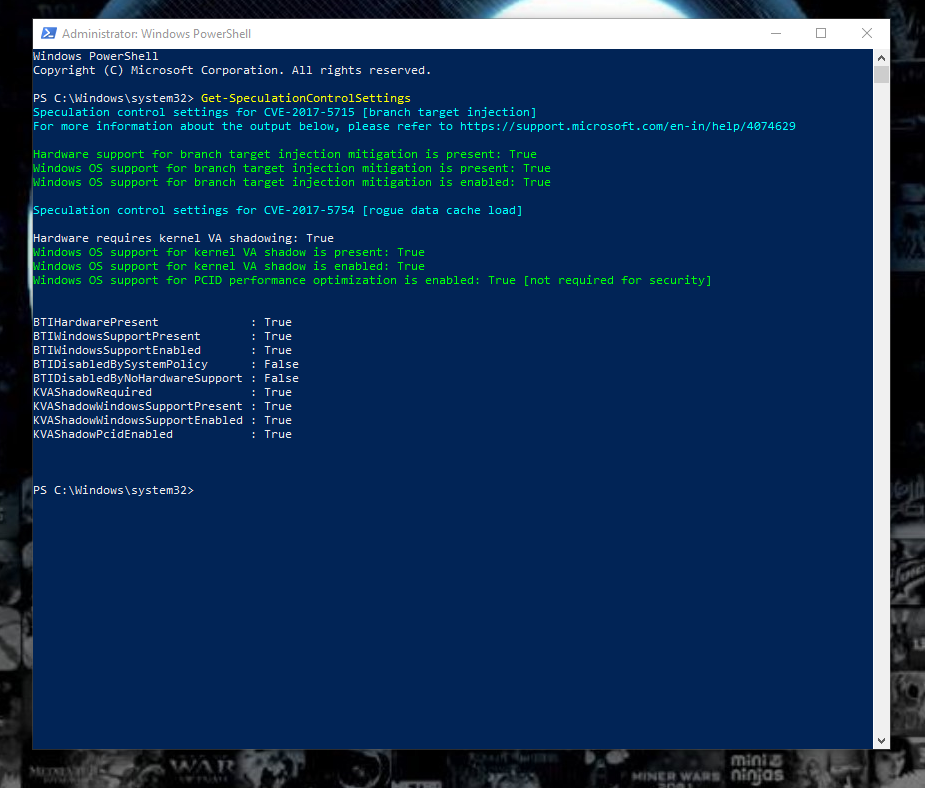
but: GRC tool happily showed this:: (prior to using the vmware driver tool the GRC app showed this system was vulnerable to spectre)
while running the powershell script gives you the sad truth that you are still sort of boned..
but: GRC tool happily showed this:: (prior to using the vmware driver tool the GRC app showed this system was vulnerable to spectre)

while running the powershell script gives you the sad truth that you are still sort of boned..

Last edited:
Good info atarione.
This is getting a bit ridiculous to have to install these patches only to find out they are installed but not enabled.
I created the "enable" registry keys, but I see no change on the SpeculationControlSettings results.
https://support.microsoft.com/help/4073119
Anybody have this figured out yet?
.
This is getting a bit ridiculous to have to install these patches only to find out they are installed but not enabled.
I created the "enable" registry keys, but I see no change on the SpeculationControlSettings results.
https://support.microsoft.com/help/4073119
Anybody have this figured out yet?
.
the_real_7
[H]ard|Gawd
- Joined
- Sep 10, 2007
- Messages
- 1,404
Im not patching crap but thats cool someone made a tool.
the tools best feature is to bypass windows 10 patches, my 8700k k is happy again
It says my hardware is still vulnerable but the OS is patched. I upgraded to latest bios last night, not sure what else I can do.
Man I totally forgot about Steve Gibson. I used to use Spinrite all the time way back in the day. I also remember Shields Up! I think the last time I spent any time on his page was during the XP era, he made tools to block UPnP and other fun stuff (LOL I see those are still listed on his site, but I guess some people still use XP)
Man I totally forgot about Steve Gibson. I used to use Spinrite all the time way back in the day. I also remember Shields Up! I think the last time I spent any time on his page was during the XP era, he made tools to block UPnP and other fun stuff (LOL I see those are still listed on his site, but I guess some people still use XP)
How do I ensure I do not download or auto install any of this crap? I'm serious. I'm not interested in degrading any performance on my 2 gaming machines. These two machines will not be running into any odd sites/places etc. My machine in sig and my daughters 6700k with gtx 1060. I don't want windows auto installing anything. How do I avoid this?
How do I ensure I do not download or auto install any of this crap? I'm serious. I'm not interested in degrading any performance on my 2 gaming machines. These two machines will not be running into any odd sites/places etc. My machine in sig and my daughters 6700k with gtx 1060. I don't want windows auto installing anything. How do I avoid this?
blacklist the KB's assuming Windows OS, since the OS is not in your sig.
Last edited:
blacklist the KB's assuming Windows OS, since the OS is not in your sig.
Windows 10. How do I blacklist the KB's. What does KB stand for?
Steve Gibson has been around a long time and is respected.
I think that is accurate.
He wrote the program Spinrite and has done a ton of other stuff.
Your opinion shall be noted in the annals of the internet forever and ever.
.
The point that you think spinrite is all sunshine and roses is telling.
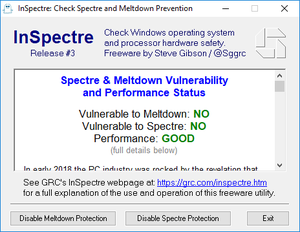
so I'm not sure that GRC tool is all that useful... I had messed about trying to use the VMware driver tool to patch the microcode for my i7-4770K /Z87X-UD3H rig.. blah blah blah... more reading makes it look like this isn't a viable solution as the microcode patch is applied to late in start up for windows to enable the spectre protections..
but: GRC tool happily showed this:: (prior to using the vmware driver tool the GRC app showed this system was vulnerable to spectre)
View attachment 50779
while running the powershell script gives you the sad truth that you are still sort of boned..
View attachment 50780
Well now, would you look at that...
The point that you think spinrite is all sunshine and roses is telling.
Well now, would you look at that...
Telling of what? That you don't know what you're talking about?
Spinrite was always a great tool to fix logical hard drive errors, I've used it a lot with very good results.
Norton Utilities was also very useful before Peter Norton sold out to Symantec.
And look at what?
That Inspectre and the Powershell script have differing test results on a complex issue that's been known about
for a few weeks? So Inspectre has no value because of that?
Ever heard of software updates?
I have no idea what your problem is dude.
You're just making noise and you have no point.
That's called trolling.
.
Last edited:
I just disabled the protection a few minutes ago through the Inspectre tool and rebooted just to see if I could tell any difference. Unfortunately, I could tell a seat of the pants "so to speak" difference in opening apps, chrome, quick file transfer, etc. Just much more snappy. I had new bios with micro code updated around the 4th this month and whenever the Microsoft update hit. Its been quite awhile and didn't really realize at the time that I was getting hit in the performance department! Just ran a couple of benchies and didn't see a big hit... Oh well, I almost don't want to turn the protection back on lol!!!
Powershell, from microsoft last week:
https://www.powershellgallery.com/packages/SpeculationControl
Automating it over the network:
https://blogs.technet.microsoft.com...ifying-spectre-meltdown-protections-remotely/
Amazing that people won't trust "M$" and use/learn simple PowerShell to verify they are patched. But they'll immediately use a third party tool that does the same exact shit.
Amazing that people won't trust "M$" and use/learn simple PowerShell to verify they are patched. But they'll immediately use a third party tool that does the same exact shit.
I think a lot of people don't even know how to run powershell, let alone understand the output of said script. I mean green is good and red is bad, right?
I think a lot of people don't even know how to run powershell, let alone understand the output of said script. I mean green is good and red is bad, right?
That's it.
Command line tools are fine for us tech folks, but my customers would have no idea how to run that or what they are looking at.
People hear about all of this in the press and they want to know the status of their own computers.
I don't have time to run around to hundreds of computers checking for them. I can send them a link to Inspectre and they can
check it themselves if they want to. They would get totally lost trying to run the Powershell script.
BTW, Inspectre is being updated. It has the Release number when you run it.
.
Last edited:
I think a lot of people don't even know how to run powershell, let alone understand the output of said script. I mean green is good and red is bad, right?
I guess I misunderstood the point of the tool - I ASSumed it was geared for IT professionals.
But yeah, I can see the need for a super-dumbed down "green = good" app for a BDU to run.
Amazing that people won't trust "M$" and use/learn simple PowerShell to verify they are patched. But they'll immediately use a third party tool that does the same exact shit.
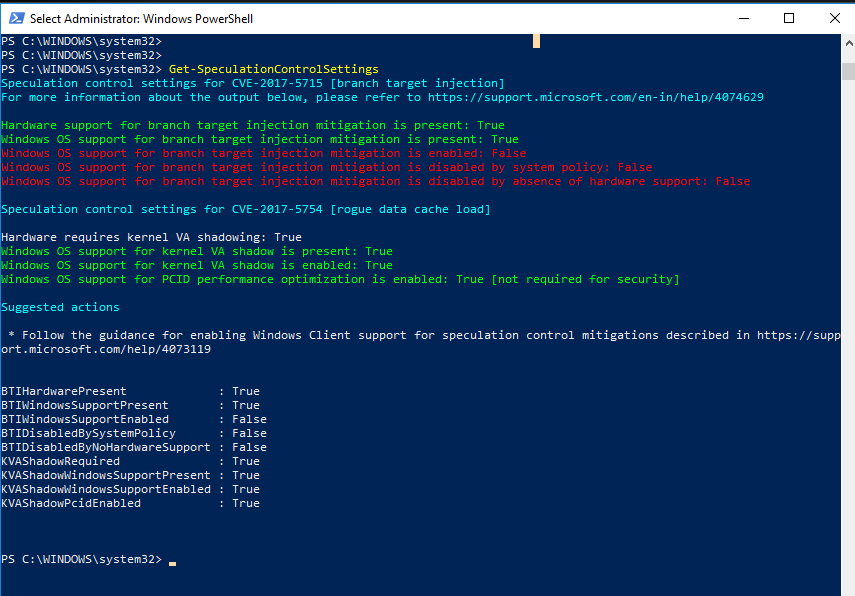
it would be "ok" if it was doing the "same shit" but most recent version #5 still says I'm patched for Spectre (which sadly is incorrect) after attempting to use VMware driver tool to apply microcode update .. which doesn't work because it doesn't load quickly enough for windows to enable the spectre mitigation..
the powershell script does properly report that the spectre mitigation is not active..
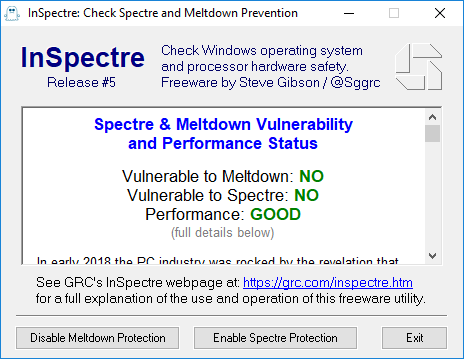
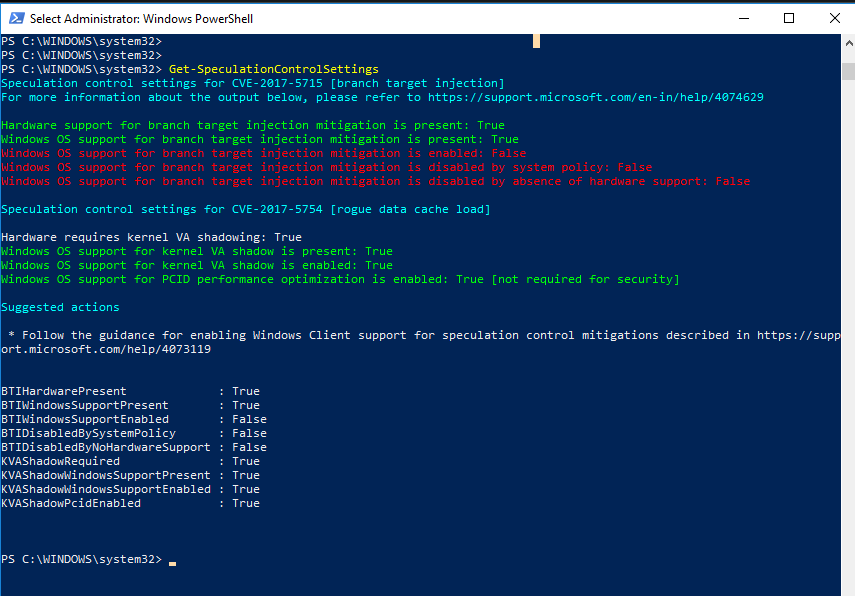
spectre needs the firmware upgrade for the intel cpu you cannot enable or disable that until then... my problem is that the os software for meltdown is not working...and I am running only windows defender don't know why it's not working....
Make sure you are on 1709 if running Windows 10.
Keep applying all Windows updates.
You may need to look at "Optional Updates" and install all of the OS updates.
I had to do that on a server to get the Meltdown patch.
Look for KB4056892 to be installed on desktop OSes.
.
![[H]ard|Forum](/styles/hardforum/xenforo/logo_dark.png)