Navigation
Install the app
How to install the app on iOS
Follow along with the video below to see how to install our site as a web app on your home screen.
Note: This feature may not be available in some browsers.
More options
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
All Intel CPUs in last 10 yrs have critical bug to show protected kernel memory areas
- Thread starter defaultluser
- Start date
TaintedSquirrel
[H]F Junkie
- Joined
- Aug 5, 2013
- Messages
- 12,688
Nice post. He should also label each CPU tested.
I noticed benchmarks with the biggest performance loss are getting the most attention, and those seem to be from random internet users and not professional benchmarkers.
Over time they need to go back and check weaker CPUs. Not everybody owns 7700K's and 8700K's.
I noticed benchmarks with the biggest performance loss are getting the most attention, and those seem to be from random internet users and not professional benchmarkers.
Over time they need to go back and check weaker CPUs. Not everybody owns 7700K's and 8700K's.
Furious_Styles
Supreme [H]ardness
- Joined
- Jan 16, 2013
- Messages
- 4,515
Most of the performance loss appears to be on storage related stuff. I don't know that I'd notice it unless I was transferring lots of large files recently.
https://cloudblogs.microsoft.com/mi...-and-meltdown-mitigations-on-windows-systems/
Here is the summary of what we have found so far:
- With Windows 10 on newer silicon (2016-era PCs with Skylake, Kabylake or newer CPU), benchmarks show single-digit slowdowns, but we don’t expect most users to notice a change because these percentages are reflected in milliseconds.
- With Windows 10 on older silicon (2015-era PCs with Haswell or older CPU), some benchmarks show more significant slowdowns, and we expect that some users will notice a decrease in system performance.
- With Windows 8 and Windows 7 on older silicon (2015-era PCs with Haswell or older CPU), we expect most users to notice a decrease in system performance.
- Windows Server on any silicon, especially in any IO-intensive application, shows a more significant performance impact when you enable the mitigations to isolate untrusted code within a Windows Server instance. This is why you want to be careful to evaluate the risk of untrusted code for each Windows Server instance, and balance the security versus performance tradeoff for your environment.
TaintedSquirrel
[H]F Junkie
- Joined
- Aug 5, 2013
- Messages
- 12,688
Windows 7 And 8
Microsoft said that it expects most users of Windows 7 and 8 to see a significant drop in performance on their computers after the Meltdown and Spectre patches are applied.
Microsoft explained that the reason why Windows 7 and 8 are more impacted than Windows 10 is because the two use older kernels which perform more transitions between the kernel-mode and the user-mode. The Meltdown and Spectre patches add security checks in-between those transitions, which explains why the performance degradation is larger on these operating systems.
Microsoft didn’t say whether or not it would be possible to upgrade Windows 7 and 8 to the newer kernel. Presumably, it would take too much work to fix operating systems that are supposed to be discontinued in a few years anyway.
Most of the performance loss appears to be on storage related stuff. I don't know that I'd notice it unless I was transferring lots of large files recently.
If you paid $300+ for a CPU with design defects, you'll notice and you won't forget either.
BinarySynapse
[H]F Junkie
- Joined
- Feb 6, 2006
- Messages
- 15,103
Did notice and remember about the defects listed in this document? http://support.amd.com/TechDocs/53072_Rev_Guide_16h_Models_30h-3Fh.pdfIf you paid $300+ for a CPU with design defects, you'll notice and you won't forget either.
or how about the ones listed in this one? https://www.mouser.com/pdfdocs/desktop-6th-gen-core-family-spec-update.pdf
All CPUs have defects.
Gideon
2[H]4U
- Joined
- Apr 13, 2006
- Messages
- 3,543
Did notice and remember about the defects listed in this document? http://support.amd.com/TechDocs/53072_Rev_Guide_16h_Models_30h-3Fh.pdf
or how about the ones listed in this one? https://www.mouser.com/pdfdocs/desktop-6th-gen-core-family-spec-update.pdf
All CPUs have defects.
Difference between a defect which has to be patched before it works fully and a defect that robs you of performance forever that you paid for.
If you paid $300+ for a CPU with design defects, you'll notice and you won't forget either.
Did notice and remember about the defects listed in this document? http://support.amd.com/TechDocs/53072_Rev_Guide_16h_Models_30h-3Fh.pdf
or how about the ones listed in this one? https://www.mouser.com/pdfdocs/desktop-6th-gen-core-family-spec-update.pdf
All CPUs have defects.
Thank you. I have 3 Skylakes and 1 Kabylake that I'm about to replace as soon as Ryzen APU is out. I won't even bother with the "patches". I even pressed my AMD FX-8350 back into service, feels nice & toasty right about now, lol. Also, I never liked the stupid Intel mobo pins that bend if you just breathe on them.
BinarySynapse
[H]F Junkie
- Joined
- Feb 6, 2006
- Messages
- 15,103
Difference between a defect which has to be patched before it works fully and a defect that robs you of performance forever that you paid for.
I don't see many people remembering the TLB bug in AMD processors from years ago that would lock up the CPU. That's a pretty serious loss of performance right there. And the immediate fix for it had some overall performance penalties too.
At least the defect in this case doesn't rob you of performance. Only the current fixes for it do. Time will tell if that improves, though.
TaintedSquirrel
[H]F Junkie
- Joined
- Aug 5, 2013
- Messages
- 12,688
"I replaced my Kaby Lake with an old FX-8350 because of Meltdown" sounds like something a troll would say.Thank you. I have 3 Skylakes and 1 Kabylake that I'm about to replace as soon as Ryzen APU is out. I won't even bother with the "patches". I even pressed my AMD FX-8350 back into service, feels nice & toasty right about now, lol. Also, I never liked the stupid Intel mobo pins that bend if you just breathe on them.
Go post that on /r/AMD and enjoy 10k upvotes.
Furious_Styles
Supreme [H]ardness
- Joined
- Jan 16, 2013
- Messages
- 4,515
"I replaced my Kaby Lake with an old FX-8350 because of Meltdown" sounds like something a troll would say.
Go post that on /r/AMD and enjoy 10k upvotes.
Agreed. Not in a hurry to get all butthurt until I've seen the definitive decreases in performance. I'm not happy to lose any performance but then again who is?
Gideon
2[H]4U
- Joined
- Apr 13, 2006
- Messages
- 3,543
I don't see many people remembering the TLB bug in AMD processors from years ago that would lock up the CPU. That's a pretty serious loss of performance right there. And the immediate fix for it had some overall performance penalties too.
At least the defect in this case doesn't rob you of performance. Only the current fixes for it do. Time will tell if that improves, though.
TLB patch could be turned on and off and very few people actually did what needed to be done for the bug to happen. I used to run with the TLB patch turned off, still sucked that it happened but at least my cpu ran at full speed since I did not use the programs that caused the issue.
OutOfPhase
Supreme [H]ardness
- Joined
- May 11, 2005
- Messages
- 6,574
Agreed. Not in a hurry to get all butthurt until I've seen the definitive decreases in performance. I'm not happy to lose any performance but then again who is?
I think I know - those horrible people who think "passionfruit" is a flavor which should be rammed in the arse of iced tea at all eating establishments. Also, people who think Kanye West is a genius.
Those people might like losing performance.
Before the patch, older version of Win 10, 6700K system with 1gb Intel 600p NVME:
CrystalDiskMark 5.2.1 x64 (C) 2007-2017 hiyohiyo
Crystal Dew World : http://crystalmark.info/
-----------------------------------------------------------------------
* MB/s = 1,000,000 bytes/s [SATA/600 = 600,000,000 bytes/s]
* KB = 1000 bytes, KiB = 1024 bytes
Sequential Read (Q= 32,T= 1) : 1842.186 MB/s
Sequential Write (Q= 32,T= 1) : 555.339 MB/s
Random Read 4KiB (Q= 32,T= 1) : 541.580 MB/s [132221.7 IOPS]
Random Write 4KiB (Q= 32,T= 1) : 519.301 MB/s [126782.5 IOPS]
Sequential Read (T= 1) : 1080.344 MB/s
Sequential Write (T= 1) : 574.231 MB/s
Random Read 4KiB (Q= 1,T= 1) : 29.496 MB/s [ 7201.2 IOPS]
Random Write 4KiB (Q= 1,T= 1) : 161.698 MB/s [ 39477.1 IOPS]
Test : 1024 MiB [C: 52.7% (502.3/953.4 GiB)] (x1) [Interval=5 sec]
Date : 2017/03/29 9:04:38
OS : Windows 10 [10.0 Build 14393] (x64)
After Patch:
CrystalDiskMark 5.2.1 x64 (C) 2007-2017 hiyohiyo
Crystal Dew World : http://crystalmark.info/
-----------------------------------------------------------------------
* MB/s = 1,000,000 bytes/s [SATA/600 = 600,000,000 bytes/s]
* KB = 1000 bytes, KiB = 1024 bytes
Sequential Read (Q= 32,T= 1) : 1776.941 MB/s
Sequential Write (Q= 32,T= 1) : 577.035 MB/s
Random Read 4KiB (Q= 32,T= 1) : 439.499 MB/s [107299.6 IOPS]
Random Write 4KiB (Q= 32,T= 1) : 356.630 MB/s [ 87067.9 IOPS]
Sequential Read (T= 1) : 1124.128 MB/s
Sequential Write (T= 1) : 80.143 MB/s
Random Read 4KiB (Q= 1,T= 1) : 35.269 MB/s [ 8610.6 IOPS]
Random Write 4KiB (Q= 1,T= 1) : 154.763 MB/s [ 37783.9 IOPS]
Test : 1024 MiB [C: 68.2% (650.2/953.4 GiB)] (x1) [Interval=5 sec]
Date : 2018/01/09 19:58:16
OS : Windows 10 [10.0 Build 16299] (x64)
Some performance loss but I really have not noticed it.
CrystalDiskMark 5.2.1 x64 (C) 2007-2017 hiyohiyo
Crystal Dew World : http://crystalmark.info/
-----------------------------------------------------------------------
* MB/s = 1,000,000 bytes/s [SATA/600 = 600,000,000 bytes/s]
* KB = 1000 bytes, KiB = 1024 bytes
Sequential Read (Q= 32,T= 1) : 1842.186 MB/s
Sequential Write (Q= 32,T= 1) : 555.339 MB/s
Random Read 4KiB (Q= 32,T= 1) : 541.580 MB/s [132221.7 IOPS]
Random Write 4KiB (Q= 32,T= 1) : 519.301 MB/s [126782.5 IOPS]
Sequential Read (T= 1) : 1080.344 MB/s
Sequential Write (T= 1) : 574.231 MB/s
Random Read 4KiB (Q= 1,T= 1) : 29.496 MB/s [ 7201.2 IOPS]
Random Write 4KiB (Q= 1,T= 1) : 161.698 MB/s [ 39477.1 IOPS]
Test : 1024 MiB [C: 52.7% (502.3/953.4 GiB)] (x1) [Interval=5 sec]
Date : 2017/03/29 9:04:38
OS : Windows 10 [10.0 Build 14393] (x64)
After Patch:
CrystalDiskMark 5.2.1 x64 (C) 2007-2017 hiyohiyo
Crystal Dew World : http://crystalmark.info/
-----------------------------------------------------------------------
* MB/s = 1,000,000 bytes/s [SATA/600 = 600,000,000 bytes/s]
* KB = 1000 bytes, KiB = 1024 bytes
Sequential Read (Q= 32,T= 1) : 1776.941 MB/s
Sequential Write (Q= 32,T= 1) : 577.035 MB/s
Random Read 4KiB (Q= 32,T= 1) : 439.499 MB/s [107299.6 IOPS]
Random Write 4KiB (Q= 32,T= 1) : 356.630 MB/s [ 87067.9 IOPS]
Sequential Read (T= 1) : 1124.128 MB/s
Sequential Write (T= 1) : 80.143 MB/s
Random Read 4KiB (Q= 1,T= 1) : 35.269 MB/s [ 8610.6 IOPS]
Random Write 4KiB (Q= 1,T= 1) : 154.763 MB/s [ 37783.9 IOPS]
Test : 1024 MiB [C: 68.2% (650.2/953.4 GiB)] (x1) [Interval=5 sec]
Date : 2018/01/09 19:58:16
OS : Windows 10 [10.0 Build 16299] (x64)
Some performance loss but I really have not noticed it.
BinarySynapse
[H]F Junkie
- Joined
- Feb 6, 2006
- Messages
- 15,103
It might be a stupid question but are consoles plagued by the same bug ( ex xbone and PS4 )?
The two you mentioned are since they use variants of mainstream AMD x86 CPUs. The Switch uses an Nvidia SoC, but, depending on which ARM core they implement, could still be vulnerable. They all have the benefit of only running signed code, but they might be exploitable if that signed code can be exploited.
Shintai
Supreme [H]ardness
- Joined
- Jul 1, 2016
- Messages
- 5,678
Thank you. I have 3 Skylakes and 1 Kabylake that I'm about to replace as soon as Ryzen APU is out. I won't even bother with the "patches". I even pressed my AMD FX-8350 back into service, feels nice & toasty right about now, lol. Also, I never liked the stupid Intel mobo pins that bend if you just breathe on them.
Then you can enjoy Zen with its Spectre issues, Crashes on Authenticode, lower performance and so on
Shintai
Supreme [H]ardness
- Joined
- Jul 1, 2016
- Messages
- 5,678
It might be a stupid question but are consoles plagued by the same bug ( ex xbone and PS4 )?
Yes, since they are OOO designs. All performance CPUs since and with Pentium Pro and K6 are affected, with the only exception being Itanium. Your phone is affected too, so is IBM mainframes and everything else. For x86 you have to buy one of the older Atoms, not newer to get an In Order design. Else it´s all the way back to Pentium MMX and K5.
Intel Quark and IoT style ARM CPUs are also In Order designs.
OrangeKhrush
[H]ard|Gawd
- Joined
- Dec 15, 2016
- Messages
- 1,673
Then you can enjoy Zen with its Spectre issues, Crashes on Authenticode, lower performance and so on
what spectre issues can they expect? most issues start at the aptly named "meltdown" when full security is passed and you can literally be hacked without protection at that point. spectre has never been the overall concern, spectre 2 seems the warning signs for near full break in but they wouldn't know that either, that is a privilege for us Intel PCMR. I am really just concerned about someone knowing what my H password is.
Shintai
Supreme [H]ardness
- Joined
- Jul 1, 2016
- Messages
- 5,678
what spectre issues can they expect? most issues start at the aptly named "meltdown" when full security is passed and you can literally be hacked without protection at that point. spectre has never been the overall concern, spectre 2 seems the warning signs for near full break in but they wouldn't know that either, that is a privilege for us Intel PCMR. I am really just concerned about someone knowing what my H password is.
Spectre is the absolute most dangerous since its an entirely new attack vector where the surface is just barely scratched. And this could kill OOO designs for good. Personally I can´t see OOO designs fixing this. So we are back to In Order designs and compiler scheduling. But this will take a decade or more since software is so far behind.
So what to expect? Plenty more of this on all platforms. And it will also yet again raise the question about support for Android phones from vendors that axe support quickly.
Last edited:
OrangeKhrush
[H]ard|Gawd
- Joined
- Dec 15, 2016
- Messages
- 1,673
Spectre is the absolute most dangerous since its an entirely new attack vector where the surface is just barely scratched. And this could kill OOO designs for good. Personally I can´t see OOO designs fixing this. So we are back to In Order designs and compiler scheduling.
reading the notes the only thing about spectre that remotely seems bad is that it is impossible to eradicate on OOO type designs but, it can be mitigated with regular OS updates. Meltdown gets its name because it is the effect of full security breaks allowing the attacker to have access to anything, it is more the "break point" of spectre intrusions.
Shintai
Supreme [H]ardness
- Joined
- Jul 1, 2016
- Messages
- 5,678
reading the notes the only thing about spectre that remotely seems bad is that it is impossible to eradicate on OOO type designs but, it can be mitigated with regular OS updates. Meltdown gets its name because it is the effect of full security breaks allowing the attacker to have access to anything, it is more the "break point" of spectre intrusions.
The current migrations is only against the now known issues. There will be more in the future. It is now a new research field, never touched before.
OrangeKhrush
[H]ard|Gawd
- Joined
- Dec 15, 2016
- Messages
- 1,673
The current migrations is only against the now known issues. There will be more in the future. It is now a new research field, never touched before.
that is true, now people are aware so hopefully this becomes a point of prime interest.
Meltdown exploits side effects of out-of-order execution on modern processors to read arbitrary kernel-memory locations including personal data and passwords. Out-of-order execution is an indispensable performance feature and present in a wide range of modern processors. The attack is independent of the operating system, and it does not rely on any software vulnerabilities. Meltdown breaks all security assumptions given by address space isolation as well as paravirtualized environments and, thus, every security mechanism building upon this foundation. On affected systems, Meltdown enables an adversary to read memory of other processes or virtual machines in the cloud without any permissions or privileges, affecting millions of customers and virtually every user of a personal computer.
Meltdown is a very bad issue, the bold being the major difference, it is a a full on system break that results in corporate losses since it is normally the Google system that is hacked and the attacker has access to the full user database and can steal information from anyone on there. Spectre remains more personal and relies on application vulnerability indicating that the application coders can still improve their security. Meltdown affects everything without discern, cloud/remote, virtual, servers, and by inference any device that accesses such point ie: mobile. I think spectre is being made to be the issue instead of facing the bigger problem, #3 is the IT levels of bad.
Shintai
Supreme [H]ardness
- Joined
- Jul 1, 2016
- Messages
- 5,678
that is true, now people are aware so hopefully this becomes a point of prime interest.
Meltdown is a very bad issue, the bold being the major difference, it is a a full on system break that results in corporate losses since it is normally the Google system that is hacked and the attacker has access to the full user database and can steal information from anyone on there. Spectre remains more personal and relies on application vulnerability indicating that the application coders can still improve their security. Meltdown affects everything without discern, cloud/remote, virtual, servers, and by inference any device that accesses such point ie: mobile. I think spectre is being made to be the issue instead of facing the bigger problem, #3 is the IT levels of bad.
You focus too much on Meltdown. You can see the next attack type tomorrow or sometime in the future. I bet you some organizations and people already sits on these new exploits.
Track Drew
Limp Gawd
- Joined
- Dec 6, 2007
- Messages
- 511
Before the patch, older version of Win 10, 6700K system with 1gb Intel 600p NVME:
...
Some performance loss but I really have not noticed it.
I'm not seeing a BIOS update for that board (https://www.gigabyte.com/Motherboard/GA-Z170N-Gaming-5-rev-10#support-dl), so safe to assume these benchmarks are without the updated microcode?
BinarySynapse
[H]F Junkie
- Joined
- Feb 6, 2006
- Messages
- 15,103
I'm not seeing a BIOS update for that board (https://www.gigabyte.com/Motherboard/GA-Z170N-Gaming-5-rev-10#support-dl), so safe to assume these benchmarks are without the updated microcode?
Microcode doesn't have to be embedded in the BIOS to be updated. It can be done by the OS during boot.
thebufenator
[H]ard|Gawd
- Joined
- Dec 8, 2004
- Messages
- 1,383
I am shocked that Shintai says Spectre is the problem and not Meltdown.
Shocked I say. Nothing to do with the Intel specific performance drop.
NOTHING AT ALL
Shocked I say. Nothing to do with the Intel specific performance drop.
NOTHING AT ALL
OutOfPhase
Supreme [H]ardness
- Joined
- May 11, 2005
- Messages
- 6,574
I am shocked that Shintai says Spectre is the problem and not Meltdown.
Shocked I say. Nothing to do with the Intel specific performance drop.
NOTHING AT ALL
Surprise or not, he's not wrong in terms of overall lasting impact to the industry.
Track Drew
Limp Gawd
- Joined
- Dec 6, 2007
- Messages
- 511
Microcode doesn't have to be embedded in the BIOS to be updated. It can be done by the OS during boot.
Of course. It just looks like he's running Windows, and to my knowledge Microsoft hasn't pushed out a microcode update yet. (I could be mistaken)
So unless they've patched the BIOS themselves, safe to say it's not running the updated microcode? (this is the reason I asked them)
Yes that is correct unless Windows updated the microcode.I'm not seeing a BIOS update for that board (https://www.gigabyte.com/Motherboard/GA-Z170N-Gaming-5-rev-10#support-dl), so safe to assume these benchmarks are without the updated microcode?
Shintai
Supreme [H]ardness
- Joined
- Jul 1, 2016
- Messages
- 5,678
Unless Microsoft changes the cyclus the next Windows microcode change will be the next major Win10 upgrade. So 3-4 months or whatever it is. Linux and unix variants should already be done.
BinarySynapse
[H]F Junkie
- Joined
- Feb 6, 2006
- Messages
- 15,103
Unless Microsoft changes the cyclus the next Windows microcode change will be the next major Win10 upgrade. So 3-4 months or whatever it is. Linux and unix variants should already be done.
What makes you think they would wait an entire product cycle to release a security patch?
Here's a chart of KB numbers for the Windows updates.
I added the ones for 2008 R2 & 2012 R2, they differ from the original numbers in the chart.
I don't have many 2016 servers under my watch, but will update when I find out the correct KB number.
.
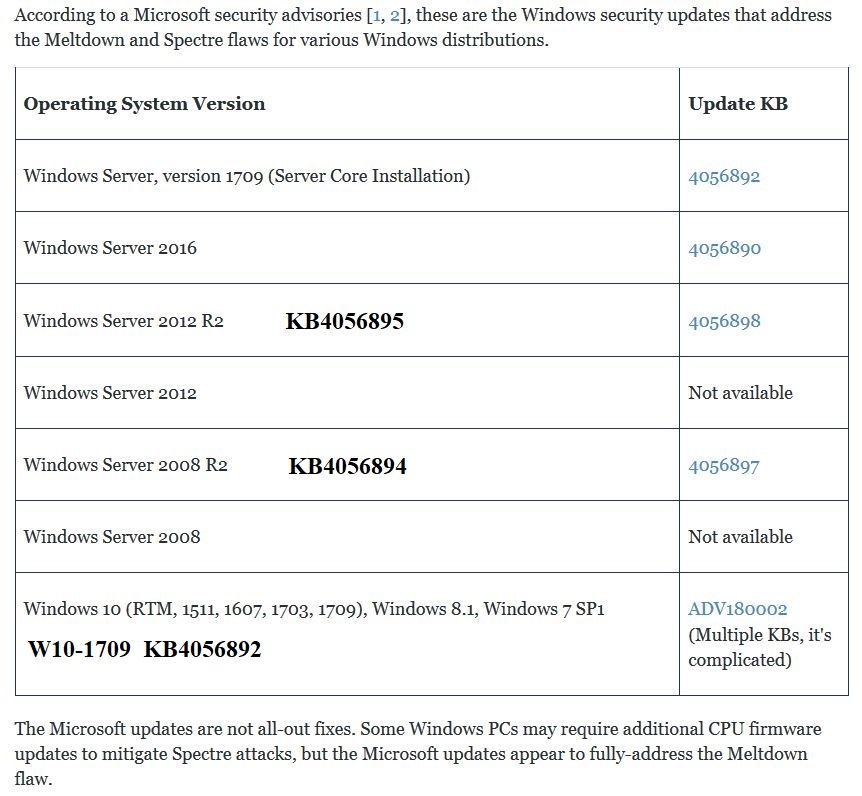
I added the ones for 2008 R2 & 2012 R2, they differ from the original numbers in the chart.
I don't have many 2016 servers under my watch, but will update when I find out the correct KB number.
.

Last edited:
Shintai
Supreme [H]ardness
- Joined
- Jul 1, 2016
- Messages
- 5,678
What makes you think they would wait an entire product cycle to release a security patch?
It´s no different than in the past, also security issues and so forth. I think everyone in the industry wished that MS would get its thing together tho. We can all agree than everyone automatically downloading a Windows update patch is better than messing with BIOS updates. The other OSes figured that out ages ago.
OrangeKhrush
[H]ard|Gawd
- Joined
- Dec 15, 2016
- Messages
- 1,673
Fine wine patches that can fix how a CPU works.


SighTurtle
[H]ard|Gawd
- Joined
- Jul 29, 2016
- Messages
- 1,410
https://www.theverge.com/platform/a...tre-disclosure-embargo-google-microsoft-linux
The Verge published a article relating to how Meltdown and Spectre we're kept secret for months before the dam bursted. Quite interesting, especially the tidbit about CERT. If anyone remembers, they issued a recommendation to "Replace all affected CPUs" for Meltdown and Spectre, something that was remarked upon a lot with bemusement by many.
The Verge published a article relating to how Meltdown and Spectre we're kept secret for months before the dam bursted. Quite interesting, especially the tidbit about CERT. If anyone remembers, they issued a recommendation to "Replace all affected CPUs" for Meltdown and Spectre, something that was remarked upon a lot with bemusement by many.
viscountalpha
2[H]4U
- Joined
- Oct 16, 2011
- Messages
- 2,618
https://www.theverge.com/platform/a...tre-disclosure-embargo-google-microsoft-linux
The Verge published a article relating to how Meltdown and Spectre we're kept secret for months before the dam bursted. Quite interesting, especially the tidbit about CERT. If anyone remembers, they issued a recommendation to "Replace all affected CPUs" for Meltdown and Spectre, something that was remarked upon a lot with bemusement by many.
Someone had a grudge against the CEO selling all that stock. That's the only reason I can think that this was leaked out like this.
Thank you. I have 3 Skylakes and 1 Kabylake that I'm about to replace as soon as Ryzen APU is out. I won't even bother with the "patches".
Interesting though, considering that RyZen chips are being patched as well.
![[H]ard|Forum](/styles/hardforum/xenforo/logo_dark.png)