Navigation
Install the app
How to install the app on iOS
Follow along with the video below to see how to install our site as a web app on your home screen.
Note: This feature may not be available in some browsers.
More options
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Exploits for Intel CPUs (NOT AMD) Documented
- Thread starter FrgMstr
- Start date
OrangeKhrush
[H]ard|Gawd
- Joined
- Dec 15, 2016
- Messages
- 1,673
AMD marketing will find a way to let this golden opportunity slip through it's fingers.
Most decisions based on opportunity are from Lisa Su directly, and her business acumen is better than many, her decisions have turned AMD from a billion dollar loss company to about that in profit in a year. AMD heads of the past perhaps would screw this up but Lisa has been getting AMD in the door even before this bombshell was dropped and you best believe she is not the type of person that will rest on laurels.
OrangeKhrush
[H]ard|Gawd
- Joined
- Dec 15, 2016
- Messages
- 1,673
D
Deleted member 93354
Guest
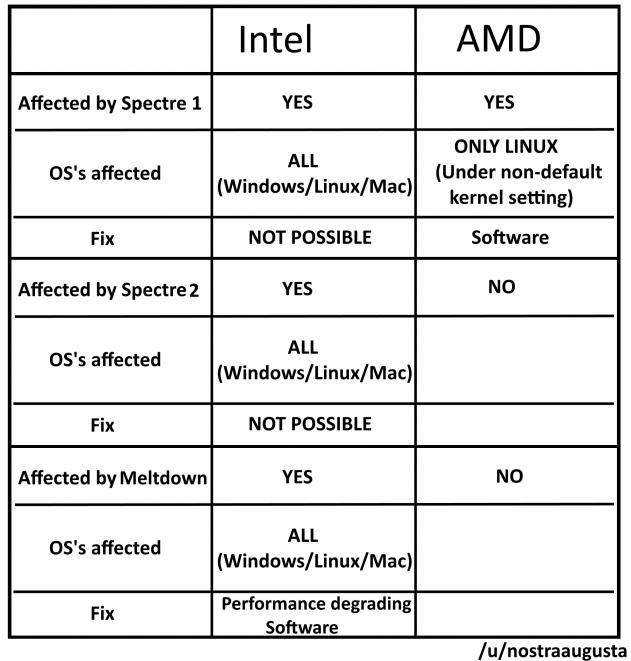
Spectre 1 applies to older amd cpu's not ryzen/TR/epyc from my understanding.
OrangeKhrush
[H]ard|Gawd
- Joined
- Dec 15, 2016
- Messages
- 1,673
Spectre 1 applies to older amd cpu's not ryzen/TR/epyc from my understanding.
possible if they used the out of order kernel syscall method, not like many people use old AMD anymore, most FX users are likely using Ryzen now and FX actually seems fine, Athlon and Phenom meh I think people actually using them are near non existent, its to old and slow by modern standards.
Riccochet
Fully [H]
- Joined
- Apr 11, 2007
- Messages
- 29,903
This isn't going to effect gaming and desktop applications as much as it'll effect datacenter operations, such as database and large data set workload applications.
We're already in talks with Cisco about upgrading our blades, but they don't currently offer AMD based solutions. That's going to change very quickly.
We're already in talks with Cisco about upgrading our blades, but they don't currently offer AMD based solutions. That's going to change very quickly.
OrangeKhrush
[H]ard|Gawd
- Joined
- Dec 15, 2016
- Messages
- 1,673
This isn't going to effect gaming and desktop applications as much as it'll effect datacenter operations, such as database and large data set workload applications.
We're already in talks with Cisco about upgrading our blades, but they don't currently offer AMD based solutions. That's going to change very quickly.
It is a fantastic opportunity for AMD to earn some new customers and hopefully impress, pretty much what Lisa Su wants, product + satisfied client, this opens up new opportunities and eco systems for AMD down the line.
OrangeKhrush
[H]ard|Gawd
- Joined
- Dec 15, 2016
- Messages
- 1,673
I'm happy....
So far.....
(Reason in signature)
It is a nice system, I would probably not use those graphics cards but perhaps you have a reason for it and I am cool with that.
don't participate in the class action.
sue independently in small claims.
Intel will not show up, and you'll get a thousand bucks for a new laptop.
THIS CANNOT BE STRESSED ENOUGH!!!!!!!!
DejaWiz
Fully [H]
- Joined
- Apr 15, 2005
- Messages
- 21,825
AMD better take this as an opportunity to step in and offer deals on enterprise data center solutions...the result could be Epyc for their bottom line.
OrangeKhrush
[H]ard|Gawd
- Joined
- Dec 15, 2016
- Messages
- 1,673
AMD better take this as an opportunity to step in and offer deals on enterprise data center solutions...the result could be Epyc for their bottom line.
It would be like christmas in january/february, that and pinnacle ridge coming could make it a merry good start.
It is a nice system, I would probably not use those graphics cards but perhaps you have a reason for it and I am cool with that.
I do lots of adobe stuff at my job, and I crunch video for my students video projects. The Vega FE is a really nice card for that, I got the second one for well, just because....I've always had a soft spot in my heart for AMD. I've owned many Intel/Nvidia systems during my days though and will switch back when my wallet dictates. The 1950X was too good of a deal to pass up at the time.
OrangeKhrush
[H]ard|Gawd
- Joined
- Dec 15, 2016
- Messages
- 1,673
I do lots of adobe stuff at my job, and I crunch video for my students video projects. The Vega FE is a really nice card for that, I got the second one for well, just because....I've always had a soft spot in my heart for AMD. I've owned many Intel/Nvidia systems during my days though and will switch back when my wallet dictates. The 1950X was too good of a deal to pass up at the time.
that seems like a perfectly understandable reason, serves a purpose. Like my CPU is not really conducive to the audio production software I have, TR would be an absolute breeze in this type of hobby.
https://spectreattack.com/spectre.pdf said:1.3 Targeted Hardware and Current Status
Hardware.
We have empirically verified the vulnerability of several Intel processors to Spectre attacks, including Ivy Bridge, Haswell and Skylake based processors. We have also verified the attack’s applicability to AMD Ryzen CPUs. Finally, we have also successfully mounted Spectre attacks on several Samsung and Qualcomm processors (which use an ARM architecture) found in popular mobile phones.
From the Graz University of Technology team. Regarding Meltdown, they only say that it is unclear whether ARM and AMD are affected.
Amazingly, the "fix" for Meltdown was originally proposed to prevent ANOTHER security flaw on Intel processors: TSX timing attacks. So, good to know that exploit is also getting fixed?
Last edited:
M76
[H]F Junkie
- Joined
- Jun 12, 2012
- Messages
- 14,036
This is still a little fuzzy to me. So what does the exploit do? does it dump random snippets from memory, the entire memory, or can it gain direct access to a specific targeted app's memory locations?
Todd Walter
Gawd
- Joined
- May 10, 2016
- Messages
- 634
This is still a little fuzzy to me. So what does the exploit do? does it dump random snippets from memory, the entire memory, or can it gain direct access to a specific targeted app's memory locations?
Yes.
M76
[H]F Junkie
- Joined
- Jun 12, 2012
- Messages
- 14,036
Yes what?Yes.
Trepidati0n
[H]F Junkie
- Joined
- Oct 26, 2004
- Messages
- 9,269
"Oh look, the hardware that runs the entire @#$% cloud has a major security flaw...but since my Crysis frame rate is unaffected, it must be no big deal."
Is this seriously a conversation we're having right now?
Linux users with their massive superiority ego made it such that a typical person gives no fucks about the finer nuances of computing systems.
Todd Walter
Gawd
- Joined
- May 10, 2016
- Messages
- 634
Yes what?
ALL of the things you mentioned are enabled via these attacks.
M76
[H]F Junkie
- Joined
- Jun 12, 2012
- Messages
- 14,036
Source on that?ALL of the things you mentioned are enabled via these attacks.
Why would you want random memory fragments if you can target specific running apps? If the exploit enables targeted memory access the other two are meaningless.
Todd Walter
Gawd
- Joined
- May 10, 2016
- Messages
- 634
Source on that?
Why would you want random memory fragments if you can target specific running apps? If the exploit enables targeted memory access the other two are meaningless.
The whitepapers from the people who discovered it. https://meltdownattack.com/
M76
[H]F Junkie
- Joined
- Jun 12, 2012
- Messages
- 14,036
I read that page and it doesn't mention any specifics like that. Or do you mean the actual white papers linked there? Did you read those?The whitepapers from the people who discovered it. https://meltdownattack.com/
Todd Walter
Gawd
- Joined
- May 10, 2016
- Messages
- 634
I read that page and it doesn't mention any specifics like that. Or do you mean the actual white papers linked there? Did you read those?
Yeah, the actual white papers. I find the two-column format headache inducing but is better than the glossy overview.
This is still a little fuzzy to me. So what does the exploit do? does it dump random snippets from memory, the entire memory, or can it gain direct access to a specific targeted app's memory locations?
https://meltdownattack.com/meltdown.pdf said:Meltdown allows an unprivileged process to read data mapped in the kernel address space, including the entire physical memory on Linux and OS X, and a large fraction of the physical memory on Windows. This may include physical memory of other processes, the kernel, and in case of kernel-sharing sandbox solutions (e.g., Docker, LXC) or Xen in paravirtualization mode, memory of the kernel (or hypervisor), and other co-located instances. While the performance heavily depends on the specific machine, e.g., processor speed, TLB and cache sizes, and DRAM speed, we can dump kernel and physical memory with up to 503 KB/s.
https://spectreattack.com/spectre.pdf said:Spectre attacks involve inducing a victim to speculatively perform operations that would not occur during correct program execution and which leak the victim’s confidential information via a side channel to the adversary. This paper describes practical attacks that combine methodology from side channel attacks, fault attacks, and return-oriented programming that can read arbitrary memory from the victim’s process.
Spectre abuses branch prediction, and targets another process. Meltdown uses exceptions instead of branch prediction, and targets the kernel.
BinarySynapse
[H]F Junkie
- Joined
- Feb 6, 2006
- Messages
- 15,103
I read that page and it doesn't mention any specifics like that. Or do you mean the actual white papers linked there? Did you read those?
From the white paper:
... an attacker can leak the complete kernel memory if the virtual address of the kernel base is known. Since all major operating systems also map the entire physical memory into the kernel address space (cf. Section 2.2), all physical memory can also be read. Before kernel 4.12, kernel address space layout randomization (KASLR) was not active by default [30]. If KASLR is active, Meltdown can still be used to find the kernel by searching through the address space (cf. Section 5.2). An attacker can also simply de-randomize the direct-physical map by iterating through the virtual address space
Looks like computer engineers are going to have to learn a bit about criminal psychology, because this exploit functions exactly like social engineering. Social engineering relies on people performing predictable actions, and you just insert yourself into that predictable behavior long enough to get what you want from them.
Ive always known if you blow enough smoke up someone's ass you can get them to believe anything, didn't realize it worked the same way for computers. But that's way absolute order works, it only serves to shelter those who know how to exploit the order.
Ive always known if you blow enough smoke up someone's ass you can get them to believe anything, didn't realize it worked the same way for computers. But that's way absolute order works, it only serves to shelter those who know how to exploit the order.
cyberguyz
Gawd
- Joined
- Aug 28, 2014
- Messages
- 710
I'm happy....
So far.....
(Reason in signature)
Same here ^^
OldBuzzard
Gawd
- Joined
- Jun 6, 2004
- Messages
- 911
I like how the mufuka that be the intel ceo, keeps this bullshit quiet just long enough for him to dump his millions of bucks of shares before news leaked out and intel share value fell.
What a cnut.
Very possibly illegal
I'm not surprised at this.
Intel, as a corporate entity, has been criminal scum since the days when the Athlon was beating the Intel CPUs like rented mules, and Intel started using illegal anti-competitive business practices to suppress AMD sales by folks like Dell, etc.
That's why I have never bought an Intel CPU for any new build, nor will I in the future. I refuse to reward CRIMINALS for their actions.
lollerwaffle
Gawd
- Joined
- Feb 3, 2008
- Messages
- 665
Bunch of malarky to me. Disabling the particular workaround on my Win10 box and moving along without performance hits. I can accept this risk.
Ok maybe I'm not understanding this. But it looks to me like 1) someone has to get a malicious program running on my system; 2) has use this exploit to get a memory dumb; 3) has to somehow get that memory dump transmitted to them and 4) has to comb through to see if they got lucky to get a password (and know what that password applies to) or CC#. I'm not losing much sleep over this (but I'm not running a server for say Amazon I'm only talking about my home PC). And a program to do 1-3 seems like that's going to have a signature once known and can be virus scanned.
And for speed. This mostly is on I/O. I/O that's cached and can be predicted is that correct? So my most I/O intensive task is doing a make on a large project. But it's just reading straight from the SSD and then writing the complied code back to the SSD, so this isn't likely to be effected by the patch if I understand what's going on.
Yes, this is only a vulnerability. It's not a malware tool or package. The real issue is it needs to be fixed so it isn't exploited.
The fixes have bad side effects, or they have to replace hardware. That's much worse from a usability and business standpoint than most exploitable issues.
The headlines are because of what it takes to fix these. Most security issues are fixed by "take these pills, and all's well" these two are the equivolent to amputation, and brain transplant. The first is doable, but it's gonna have life changing effects. The second...
Master_shake_
Fully [H]
- Joined
- Apr 9, 2012
- Messages
- 17,794
It's not AMD at all and only some arm processors which arm themselves have listed on their site.The cnn.Com article makes it sound like this is all intel, arm, and amd systems or pretty much all computers.
Didn't see a feedback link and had to leave for work.
As opposed to another chipmaker who is playing with fire.
Well, right now, but it seems like to be useful (for targeting your average home user) it will need a malware tool kit (again I'm only talking home, not some server that has tons of users of various levels). Anyway glad I'm not running DB servers, but those server farms, yikes!Yes, this is only a vulnerability. It's not a malware tool or package.
Well of course there are those kids who might use it to steal their parents passwords (the ones who can't unlock their parents phones with their faces anyway)
Gideon
2[H]4U
- Joined
- Apr 13, 2006
- Messages
- 3,557
Bunch of malarky to me. Disabling the particular workaround on my Win10 box and moving along without performance hits. I can accept this risk.
You will regret that if your on the internet, very easy to get compromised with this particular vulnerability and likely wont know you were compromised. Kernel level access is all bad.
![[H]ard|Forum](/styles/hardforum/xenforo/logo_dark.png)