So yesterday, one of our development servers and a couple of our virtualization servers were hit by a crypto locker.
kangarooencryption
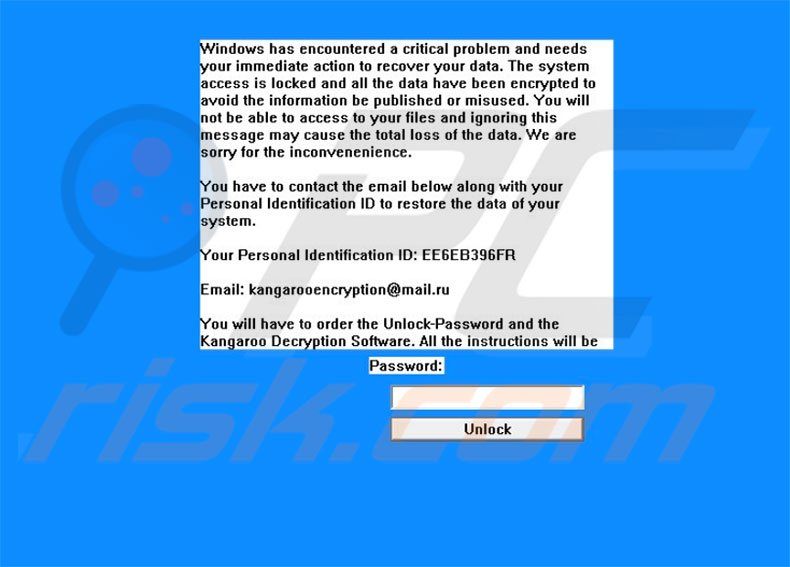
Fortunately the virtual machines themselves were not affected and while most files on the develpment server were encrypted, pretty much all the important stuff was on a cloud backup and a local NAS.
Suffice to say that the infected devices were cleaned and encrypted files deleted.
On the bright side, its the perfect time to install Windows Server 2016, which I already did on one of the Virtualization servers and the other sometime tonight I guess.
kangarooencryption

Fortunately the virtual machines themselves were not affected and while most files on the develpment server were encrypted, pretty much all the important stuff was on a cloud backup and a local NAS.
Suffice to say that the infected devices were cleaned and encrypted files deleted.
On the bright side, its the perfect time to install Windows Server 2016, which I already did on one of the Virtualization servers and the other sometime tonight I guess.
![[H]ard|Forum](/styles/hardforum/xenforo/logo_dark.png)