Wrecked Em
Supreme [H]ardness
- Joined
- Sep 14, 2004
- Messages
- 8,169
I recently decided to try out Nextcloud and have been playing around with it a bit. It's currently running on my main unraid box, behind a single untangle router. Seems to be working great.
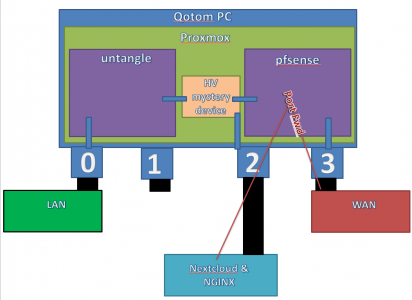
I'm a networking noob, but sort of latched onto the idea of a dual firewall, mostly because wikipedia says it's better. I was wondering if I could accomplish this in a single box. My router is a qotom i5 machine with 4 nics.
Would running this all under a single proxmox instance, as shown below, provide any benefit at all, or would it just be a bunch of extra effort for nothing? The end goal would be to have nothing on the LAN externally accessible.
In my head, this seems like a nice elegant setup, but can't seem to find any instance of someone even mentioning it, so I'm assuming there's some obvious flaw that I'm overlooking.
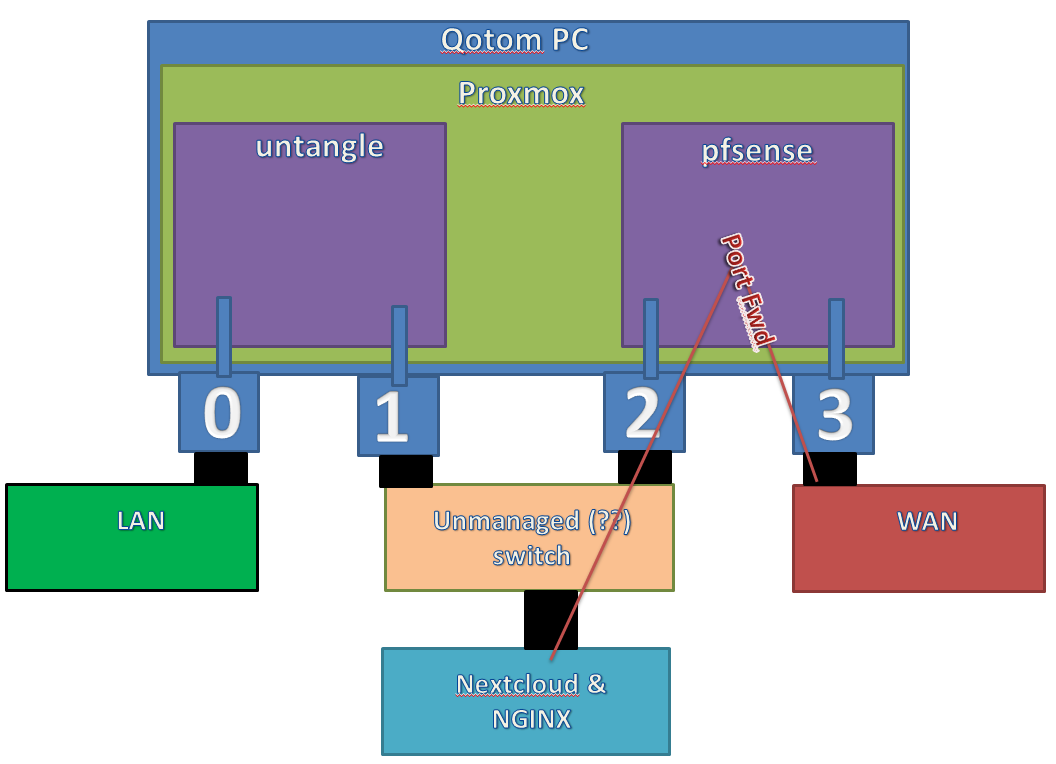
If this seems reasonable, then the next question is how to get rid of the external switch?
-------edit---------- I think this is how it would look.
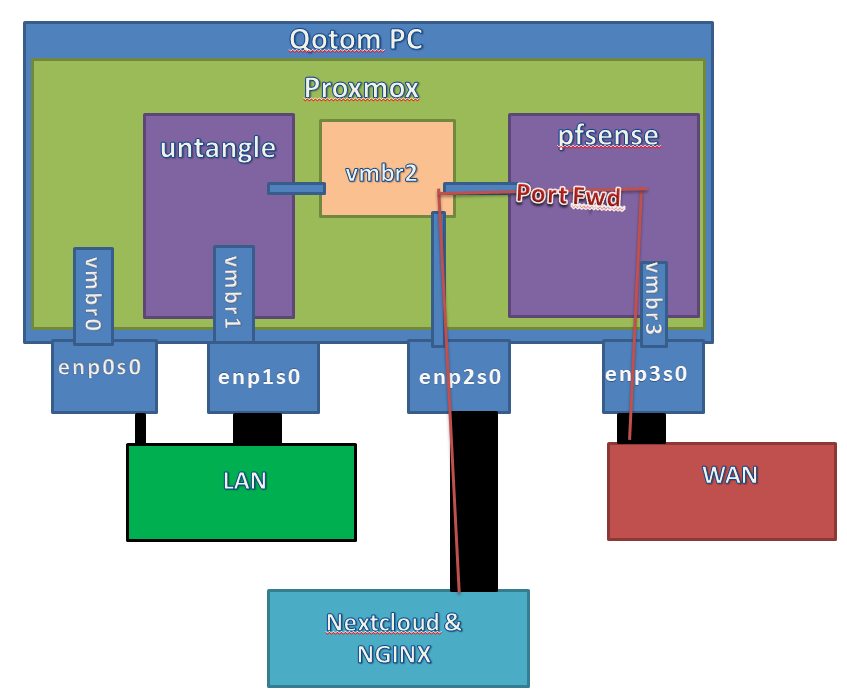
I'm a networking noob, but sort of latched onto the idea of a dual firewall, mostly because wikipedia says it's better. I was wondering if I could accomplish this in a single box. My router is a qotom i5 machine with 4 nics.
Would running this all under a single proxmox instance, as shown below, provide any benefit at all, or would it just be a bunch of extra effort for nothing? The end goal would be to have nothing on the LAN externally accessible.
In my head, this seems like a nice elegant setup, but can't seem to find any instance of someone even mentioning it, so I'm assuming there's some obvious flaw that I'm overlooking.

If this seems reasonable, then the next question is how to get rid of the external switch?
-------edit---------- I think this is how it would look.

Attachments
Last edited:
![[H]ard|Forum](/styles/hardforum/xenforo/logo_dark.png)