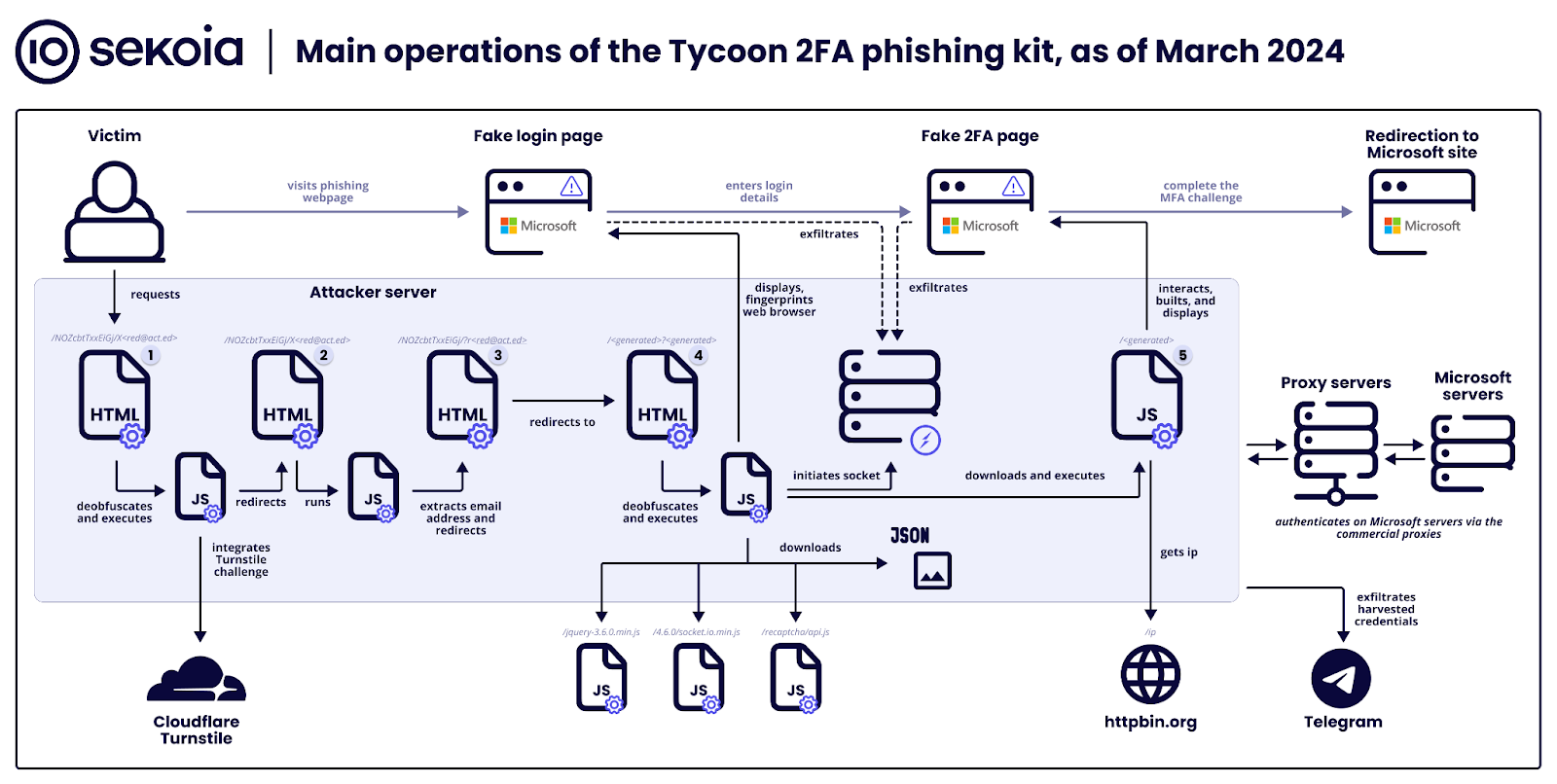
https://www.bleepingcomputer.com/ne...hing-kit-targets-microsoft-365-gmail-accounts
It's only going after O365 and Gmail now, but I can see how it could easily be expanded.
And people wonder why I have trust issues...
It's only going after O365 and Gmail now, but I can see how it could easily be expanded.
And people wonder why I have trust issues...

![[H]ard|Forum](/styles/hardforum/xenforo/logo_dark.png)